
A new variant of AsyncRAT named ‘HotRAT’ by cybersecurity analysts at Avast has been targeting internet users who download cracked and pirated software, including popular games and pro-grade tools.
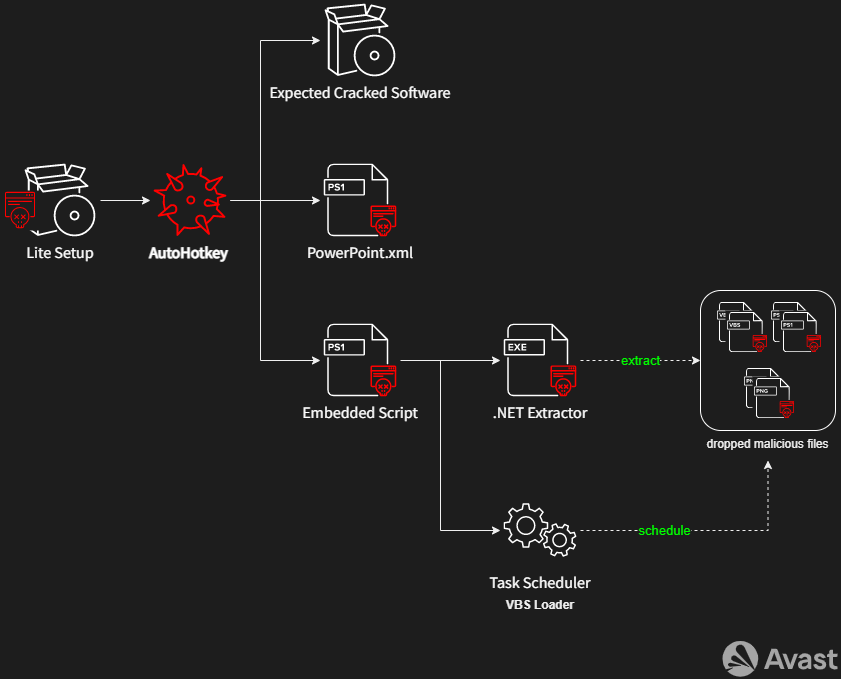
HotRAT distributors source “clean” game and software cracks that are available online and infect them with a malicious AutoHotkey script hiding PowerShell code that turns off security software, establish persistence on the breached system, and eventually deploys the final malware payload using a VBS loader.
Avast
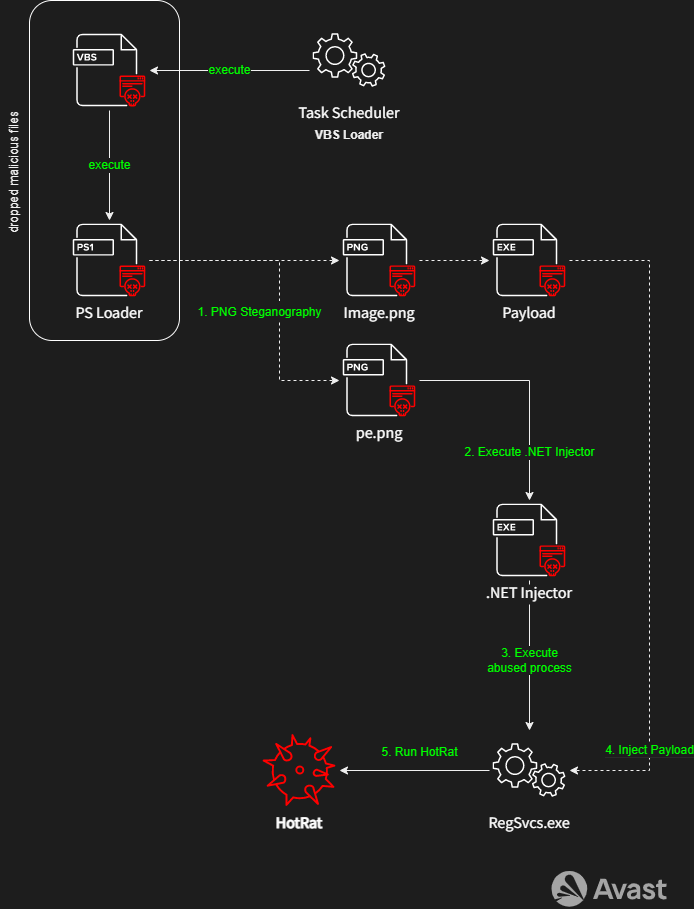
The infection chain involves multiple stages, while the actual deployment of HotRAT using the Task Scheduler is illustrated below.
Avast
HotRAT gives attackers various capabilities, including stealing login credentials, targeting cryptocurrency wallets, capturing screenshots, logging key presses, accessing and modifying clipboard data, or fetching additional payloads from the attacker’s server.
HotRAT Details
Compared to AsyncRAT, an open-source malware that was used as the basis for the new malware family, HotRAT features an additional 20 commands, including for uninstalling AV tools from Avast, Malwarebytes, AVG, McAfee, and Avira, setting up proxies, killing specific processes, and stealing credentials for AnyDesk.
Also, the malware abuses its admin-level execution privileges to add the entire C:\ path into Windows Defender’s exclusion paths, essentially disabling all security alerts that would have warned users of malicious activity taking place on their system.
The cracks used for distributing HotRAT to unsuspecting users include:
- Adobe Illustrator 2023
- Far Cry 4 gold edition
- Adobe Photoshop 2021
- IObit Uninstaller Pro
- Age of Empires IV Digital Deluxe Edition
- Microsoft Office 2022
- Battlefield 3 Premium Edition
- Microsoft Office 2022 LTSC
- Microsoft Office Professional Plus 2021
- Nitro Pro Enterprise
- CCleaner Professional
- Sniper Elite 4 Deluxe Edition
- Command & Conquer Red Alert 2
- The Sims 4
- CyberLink Screen Recorder Deluxe
- Tiktok 18+ Plus PC Download
- Topaz Video AI
- Disk Drill Enterprise
- Vmware Workstation pro
- Wondershare Filmora
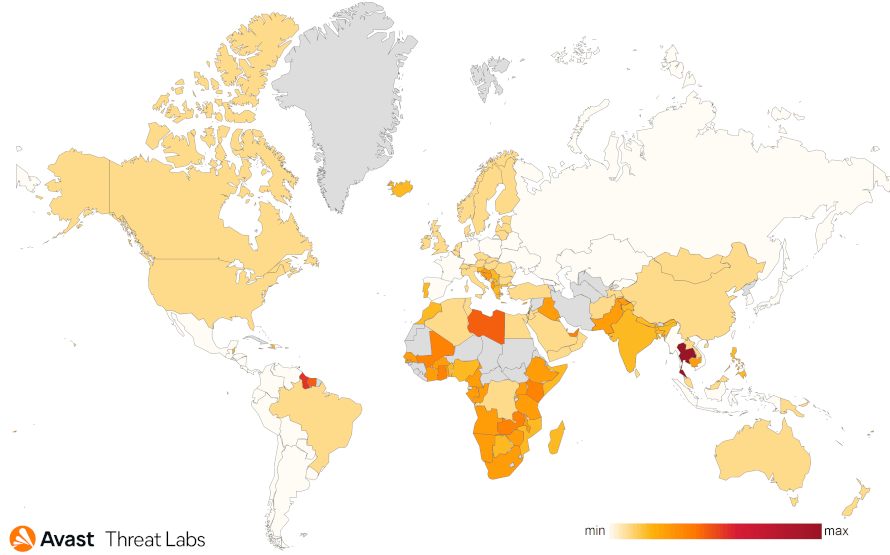
Avast’s infection stats show that HotRAT has been actively distributed to victims worldwide since last year, recording a significant spike of activity in mid-October 2022. Since then, Avast has been observing stable infection rates, so the HotRAT campaign is still active.
While the malware has infected computers in the United States, Europe, and Southeast Asia, the most impacted countries are Thailand, Libya, and Guyana, likely due to internet users in those places engaging more heavily in software piracy.
Avast
Avast’s analysts report that most of the infected cracked software is distributed via websites that “specialize” in piracy and not via the usual suspect, aka torrents. Malicious forum posts promoting installers laced with the HotRAT script have also been observed.
Users are recommended to avoid all dubious software sources and abstain from software piracy entirely, as these downloads always come with an elevated risk for malware infection.

 Milliman Solutions Says Data of 1.2 Million Americans Stolen by Hackers
Milliman Solutions Says Data of 1.2 Million Americans Stolen by Hackers
Leave a Reply