
The American gaming-focused consumer electronics maker Razer (RAZER) has responded to the rumors about a data breach, saying that it is investigating.
The allegations about a data breach on Razer belong to a threat actor who posted on ‘BreachForums’ during the weekend, saying that he is willing to sell a rich dataset containing valuable assets of the company.
“We have been made aware of a potential breach and are currently investigating,” reads Razer’s tweet that responds to threat intelligence platform FalconFeedsio, which was the first to spot the sale.
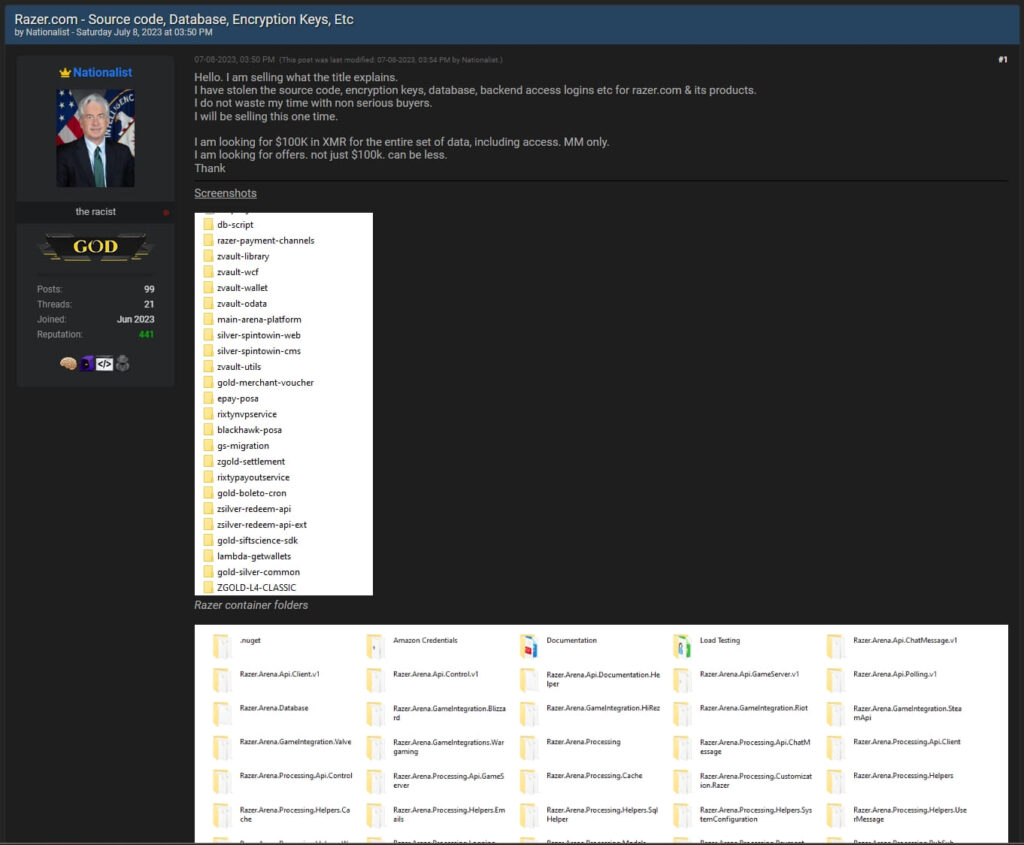
The threat actor claims to have stolen source code, encryption keys, database dumps, backend access credentials for razer.com and subbrands, and more.
The asking price for the above is $100,000 in Monero (XMR), a hard-to-trace cryptocurrency that many threat actors prefer over more mainstream options such as Bitcoin or Ether.
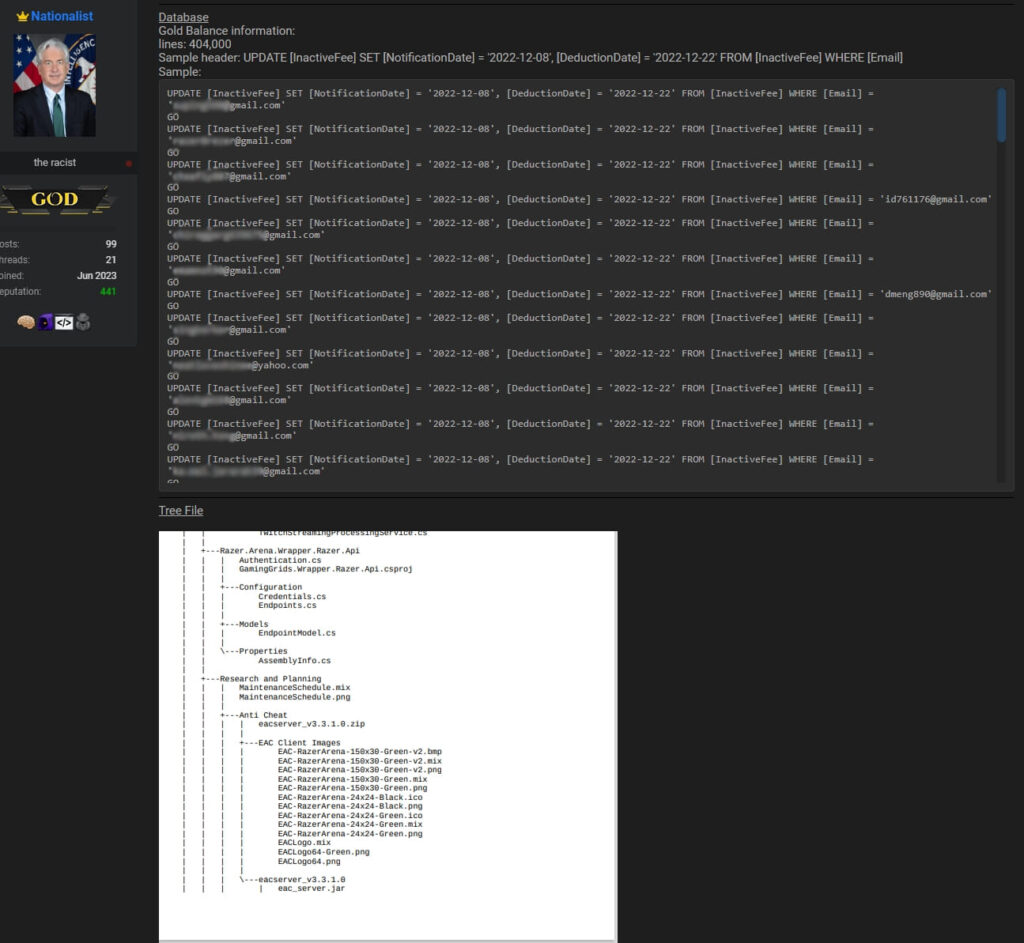
The seller, a newly registered user in the hacker forum, has also posted several screenshots showing the directory tree of the accessed files, credential pairs, and other file content.
(RestorePrivacy)
(RestorePrivacy)
The stolen database allegedly contains over 400 thousand lines, so it’s implausible that the listed emails pertain solely to Razer’s employees, making it more likely that customer information is included in it too.
RestorePrivacy has requested Razer to clarify if the screenshots posted by the cybercriminal show what appears as authentic data, but we have not received a response yet.
Razer’s 2020 Lapse
In September 2020, unprotected database “hunter” Volodymyr Diachenko discovered a database belonging to Razer, which was misconfigured to allow unauthenticated access to anyone with a valid URL since at least mid-August 2020.
That database contained the full names, email addresses, phone numbers, customer ID, order details, billing details, and shipping addresses of 100,000 customers of the gaming company.
Although in the 2020 case it was never proved that anyone besides Diachenko had accessed the data, the more recent incident clearly involves at least one cybercriminal, and the number of those having access to the data may grow exponentially very soon.
Regarding the potential links between the two incidents, the data samples posted by the forum user date to as recently as December 2022, so we can assume that this concerns a new security lapse.

 Privacy-Focused Smartphone Fairphone 4 Enters the U.S. Market
Privacy-Focused Smartphone Fairphone 4 Enters the U.S. Market
Leave a Reply