
Portuguese researchers have presented a prototype system named ‘TorKameleon,’ which enhances Tor network’s resistance to sophisticated deanonymization attacks.
The authors of TorKameleon have tested their solution against state-of-the-art correlation attacks that can deanonymize people and validated that it works as expected without a notable impact on Tor’s browsing performance.
It is important to note that TorKameleon was released as an open-source JavaScript tool, so it could easily be incorporated into Tor when its codebase reaches maturity, or if the Tor Project decides to adopt it.
Tor’s Deanonymization Problem
The Tor network is a decentralized volunteer-operated network only accessible via the Tor browser, where users can interact without exposing their IP addresses, passing their traffic through a series of nodes and relays.
While the Tor network can be used for accessing both the surface web (regular sites), it can also be used for accessing the “dark web” (onion domains). So, while it has legitimate uses, such as accessing or sharing information privately, many use the Tor network for illegal or malicious purposes.
For this reason, intelligence services and law enforcement have repeatedly attempted to launch deanonymization attacks, devise secret backdoors to eavesdrop on Tor’s traffic, or block the nodes of the network to reduce its functionality and impose targeted censorship.
Attackers can take advantage of the lack of traffic obfuscation to use statistical analysis and machine learning models to identify pairs of input and output network flows with similar characteristics, achieving the tracking and eventual identification of Tor users, even if their traffic is encrypted and randomly bounced on the Tor network.
TorKameleon Solution
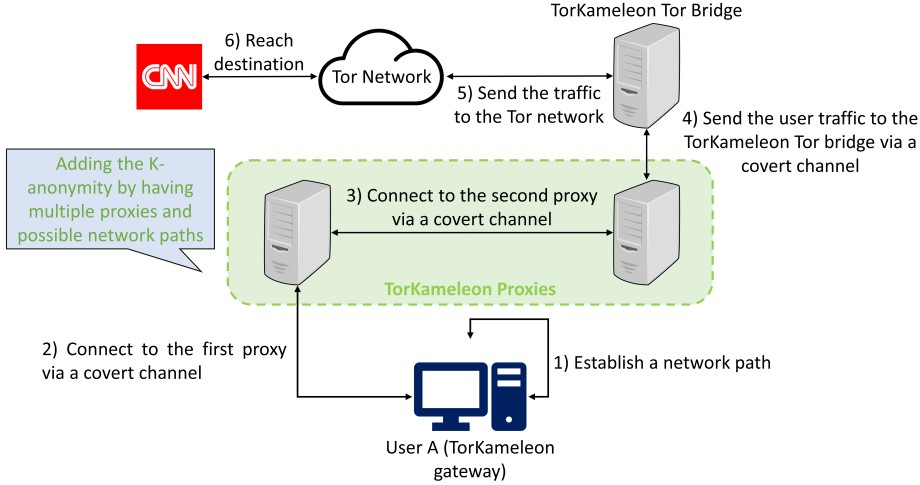
To defend against these attacks, the researchers have developed TorKameleon, a standalone, fully integrated Tor pluggable transport, which combines K-anonymization, WebRTC traffic encapsulation, and TLS encryption.
The system works by de-coupling the user traffic before it forwards it to the Tor network, connecting directly to the TorKameleon bridge using a gateway installed on the user’s system.
At this stage, users of TorKameleon coordinate with K-1 other users to deploy their proxies, creating a larger traffic pool that helps them mask their individual traffic fingerprint before they even connect to the Tor network, which is presumably monitored by adversaries who collect and analyze the network traffic.
arxiv.org
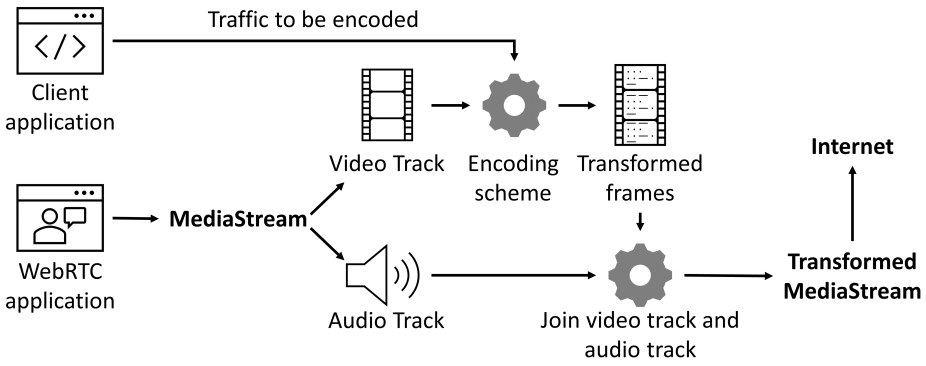
Next, the user’s traffic is mixed with WebRTC media streams that appear normal to censors because the traffic data is embedded into the frames of the stream’s audio and video tracks using TLS encapsulation.
arxiv.org
TorKameleon offers two mixing modes, one that inserts data blocks to a single frame without replacing content (ADD), which makes data transmissions faster, and one that replaces stream data with user traffic data (REPLACE). The second approach guarantees unobservability at the cost of lower throughput.
Testing TorKameleon’s resistance against correlation attacks revealed that the system could successfully evade compromise for packet sizes of 536 bytes in ADD mode and 1050 bytes in REPLACE mode. However, the latter may be increased up to 2078 bytes without significantly raising the risk of exposure.
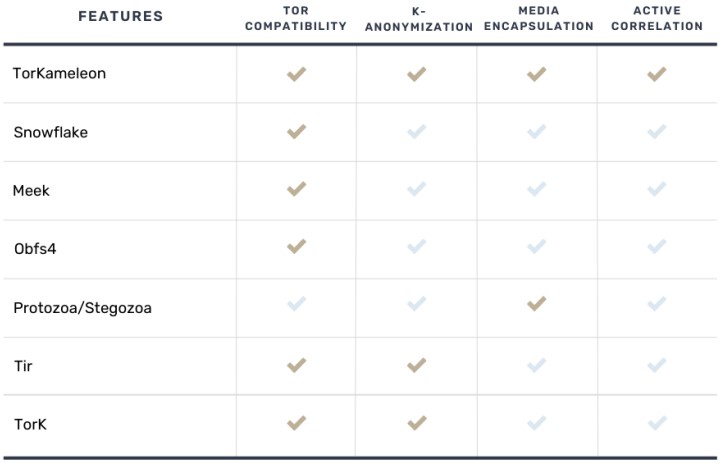
In conclusion, TorkKameleon is the first Tor-compatible evasion tool that can resist state-of-the-art correlation attacks and the first that combines K-anonymization and traffic encapsulation mechanisms.
arxiv.org
If you’re interested in reading more about TorKameleon, check out the technical paper published on Arxiv.org.

 Italian Data Authority Targets ChatGPT for Privacy Violations
Italian Data Authority Targets ChatGPT for Privacy Violations
Well, it’s not a simple approach as a solution based on VPN-enabled input circuits… There is something more that is, in fact, the core of the contribution.
1) The solution enable the possibility to use K-anonymized input circuits, where multiple users ca collaborate to “mix” the traffic” (including the traffic to be hidden for a certain user), so the inout traffic in the special pluggable transport created by the solution creates an enforcement of non-observabality and non-correlation between
traffic flows entering in ToR nodes nd exit circuitos from Tor
2) The traffic in TorKameleon enables curcuitos don’t use necessarily TLS or not being only VPNs… The traffic is embedded in WebRTC (video streaming) … So what you see entering in ToR is webRTC traffic … with the real covert traffic being any other TCP enabled traffic (ex., HTTP)… This is more as “real-time video-streamed steganographic covert channels”. Of course that as alternative or in complementarity, TorKameleon can support different forms of traffic encapsulation: the video-streaming encapsulation OR TLS-Tunneled encapsulation.
The idea for WebRTC is interesting because VPNs can be blocked ny authoritative entites/agencies etc (we observed this)… But to block WebRTC traffic now a days is not easy for such entities
3) Finally what is interesting is that ToRKameleon ws used for example to supporte “covert video-channels” encapsulated in other “WebRTC video conversations ” , a sn interesting proof of concept
This appears to my uneducated eyes to be the extended equivalent of using a VPN first. User-VPN-Tor, which Tor and many others always instinctively recoil from without going in to the full technical details of why it is bad. Such a setup will protect against malicious guard nodes, which Tor has had massive problems with in the past.
To any reading it was around a third of all guard nodes were compromised. Such a thing is purely meant to deanonymize Tor users, this was found late 2021.
Certain VPNs have multiple hops, such as Proton with a secure first connection followed by a secondary VPN connection.
That would be User-VPN Server-VPN Server-Tor. The difference is money, multiple hops in a VPN always cost a few Euro per month where this TorKameleon is free.
To many that means the VPNs have a reason to adhere to strict codes as if they do not they will potentially lose massive amounts of money from customers leaving. This TorKameleon does not. It will be a long time before it is trusted by the community on any real level.
Good of them to do this still but there are hurtles to overcome from the Tor Project itself and the user base before this can be really used.
This is what I was thinking, too. Sven always preaches a good VPN like NordVPN before using Tor–despite all Tor users claiming not to use a VPN–so it seems to me that a good investment like NordVPN would solve any issues.
I meant “Heinrich”….not “Sven.” Not even sure where that came from! 🙂
So when are you guys gonna talk about the Restrict Act that our government is trying to impose on us?
Yeah seriously, the Restrict Act = acting like China (The Great Firewall) to stop muh “China, Russia, or whoever they say”.