
Researchers from New York University and KU Leuven have developed two new attacks collectively named ‘TunnelCrack’ that can cause a broad range of VPN clients to leak user traffic outside the protected encryption tunnels.
The two attacks, ‘LocalNet’ and ‘ServerIP,’ stem from how VPN clients configure the underlying OS to route traffic through VPN tunnels by updating the system’s IP routing tables. The OS retains some exceptions for local network communications and for direct data exchange between the VPN client and the VPN server. The researchers discovered that it’s possible to manipulate exceptions in the routing scheme by using spoofed DNS responses and rogue WiFi access points, achieving unencrypted network traffic leak even when a VPN connection is active.
Through extensive testing and experimentation on 66 VPN products and five operating system platforms, the university researchers found that all of them are vulnerable to TunnelCrack in at least one case. The researchers presented the full details of their discovery in a technical paper on USENIX Security.
LocalNet Attack
LocalNet attack requires the adversary to set up a malicious WiFi access point and entice victims to connect. Once this happens, the attacker assigns them a public IP address and subnet such that all external website addresses will appear to the client as reachable in the local network.
Because most VPNs allow direct access to the local network, setting this as an exception to the routing table, the traffic generated under these conditions is not passed through the encrypting tunnels.
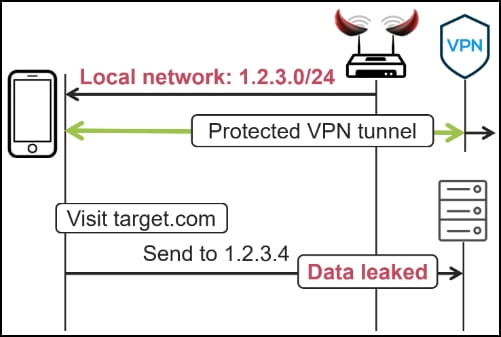
tunnelcrack.mathyvanhoef.com
This problem was given the identifier CVE-2023-36672, carrying a CVSS score of 6.8, mitigated mainly by the fact that the attacker has to have LAN access or be in WiFi range to launch the attack. Even then, the victim must be tricked into connecting to the rogue access point using a deceptive SSID.
ServerIP Attack
The ServerIP attack exploits a design flaw present in many VPNs, which do not encrypt traffic destined to directly reach the VPN server for speed and computational resource usage efficiency. The attack requires setting up a rogue WiFi hotspot again or hijacking the target’s local area network.
Next, the attacker exploits the non-tunneled communication between the VPN client and the VPN server to redirect DNS requests to a server under their control. Hence, whenever the user tries to connect to the service’s legitimate VPN server, they will instead link to the attacker’s server, allowing them to intercept network traffic and capture secrets.
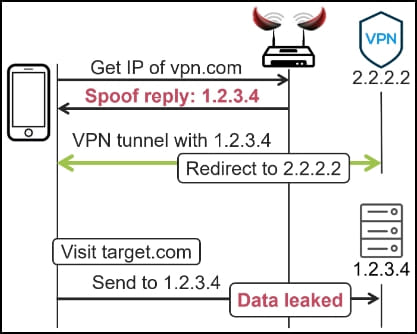
tunnelcrack.mathyvanhoef.com
It is essential to note that the captured data remains encrypted in this case, so deciphering it might be challenging depending on how strong the encryption used by the particular VPN product is. However, even if the intercepted traffic remains protected, the attacker can still manipulate the data exchange and inject malware or other malicious payloads in the stream destined for the user’s device.
This issue that can leak user traffic to arbitrary IP addresses is tracked as CVE-2023-36673 and has a severity rating of 7.4 under the CVSS scoring system.
TunnelCrack Impact
LocalNet attack was found to impact all VPN apps on iOS, all VPN clients except for one on macOS, the majority of the tested VPNs on Windows, and over one-third of VPNs on Linux. Android was the safest platform in terms of impact by LocalNet, with roughly 21% of the VPN apps found to be susceptible.
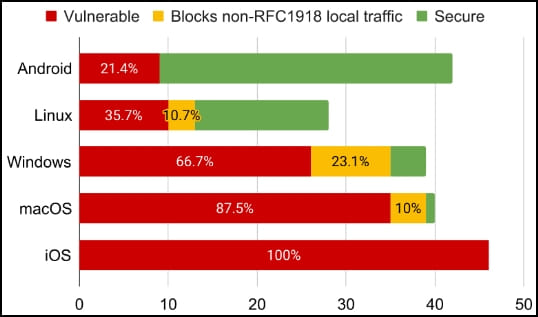
tunnelcrack.mathyvanhoef.com
The most definitive solution to LocalNet attacks is to automatically disable local network access if public IP addresses are used, which should prevent the misrouting of traffic outside the VPN tunnel.
Regarding ServerIP, the researchers have not provided statistics about the impact of this attack on the tested VPN products, so that part remains unclear. In terms of mitigation, the recommended actions include using DNS over HTTPS (DoH) or DNS over TLS (DoT), which encrypt and protect the DNS queries from tampering.
In general, users should only connect to trusted WiFi networks, avoid unknown public hotspots, and beware of spoofed access points that appear as duplicates in the scan list.
At this time, there are no known reports of active exploitation of ‘TunnelCrack,’ however, this could change following the full disclosure of the issues. The security researchers have shared instructions on how to manually test VPN clients on GitHub, which aspiring attackers could use to develop effective data-stealing attacks against specific targets.
VPN users are advised to keep their clients up to date and apply the available security updates as soon as those are released, across all their devices and platforms.

 Millions Potentially Affected in Colorado Department of Higher Education Data Breach
Millions Potentially Affected in Colorado Department of Higher Education Data Breach
FEAR MONGERING.
“We at Mullvad have been aware of this for a long time but not considered it a practical or important attack vector in the scope of being fixed by a VPN app. If an attacker controls the router/AP, which they need to do to perform this attack, they can block any traffic from the victim’s device anyway. We do not believe that being able to do it selectively for certain IP ranges changes anything significant. Any device that is configured in such a way that it connects to unauthenticated (the only type that can be spoofed like this) WiFi access points is susceptible to denial of service attacks, period”
Oh and this want already mentioned by Mullvad on their blog.
https://mullvad.net/en/blog/2023/8/9/response-to-tunnelcrack-vulnerability-disclosure/
Mullvad seems to be overall most secure option against this, check PDF with list of VPNs.
Yeah, Mullvad is very secure and fast. The only problem I have with it is its users. Mullvad is by far the most captcha strucken VPN out there. No other VPN attrackts captchas like Mullvad.
I’m sick of people pretending Mullvad is perfect, and if you don’t agree, you are an evil shill.
Mullvad sucks when it comes to streaming, and it also has lots of CAPTCHA problems, which is a major issue for everyday use, as others have pointed out here in the comments. I think it’s strong in the privacy and security areas, but that’s about it.
Yes, I agree.
Excellent research. Another reason for not to use wifi, better with an ethernet cable. Thanks Heinrich!
Lol. What research, kiddo? I don’t see Heinrich’s name in the study.
But do tell if Samsung or Huawei partly funded the study which isn’t peer reviewed.