
Many Android devices that U.S. carriers offer their subscribers contain dangerous bloatware that introduces severe risks to the privacy and security of the users.
Mobile security firm Quokka has conducted a study by examining 21 Android devices from Tracfone, AT&T, Verizon, T-Mobile, Boost Mobile, and Visible, and concluded that most of them can be traced, tracked, and remotely compromised, if a determined attacker exploits the vulnerabilities in the bloatware that comes pre-installed with the phones.
To make matters even worse, users cannot uninstall these apps nor turn off their background activity, so they constitute a permanent risk for as long as they keep using the devices.
The tested phones include popular models such as the Samsung Galaxy A13 5G and A03S, the Nokia C100 and C200, and the Motorola Moto G Pure and G Power. It is essential to clarify that these phones are perfectly safe to use in their factory state, as their manufacturers and also Google strive hard to offer secure, vetted software and firmware that incorporate multiple data-safety mechanisms that prevent easy abuse.
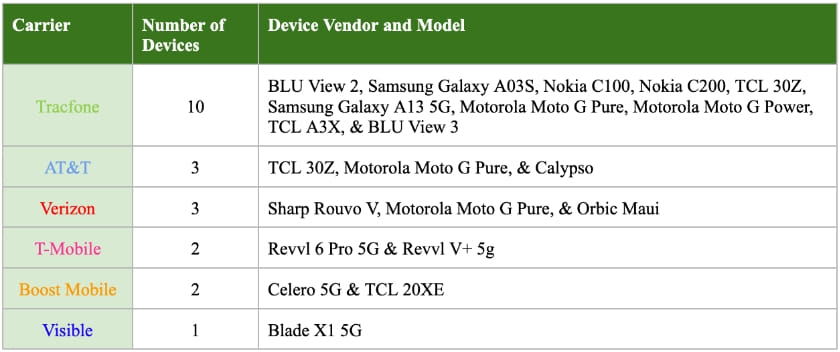
The problem is introduced on the carrier level when these companies decide to add their apps to the phones and also include tools from their vendors, marketing partners, hardware and software testing utilities for their service departments, etc.
These tools are often given the highest privileges on the device, exposing users to unauthorized personal data access without them even knowing about the risk. The reason for this ignorance is that the user knowingly grants risky permissions while installing a new app, but pre-installed apps have secured those permissions without involving the device owner.
“In other cases we observed, pre-loaded software obtains sensitive data and makes it accessible, using one mechanism or another, to co-located apps without performing the requisite access control checks. This creates a leakage of sensitive data where malicious apps can monitor and harvest this sensitive data if they are aware of where to obtain it.”
Quokka
Stealing data from pre-loaded apps
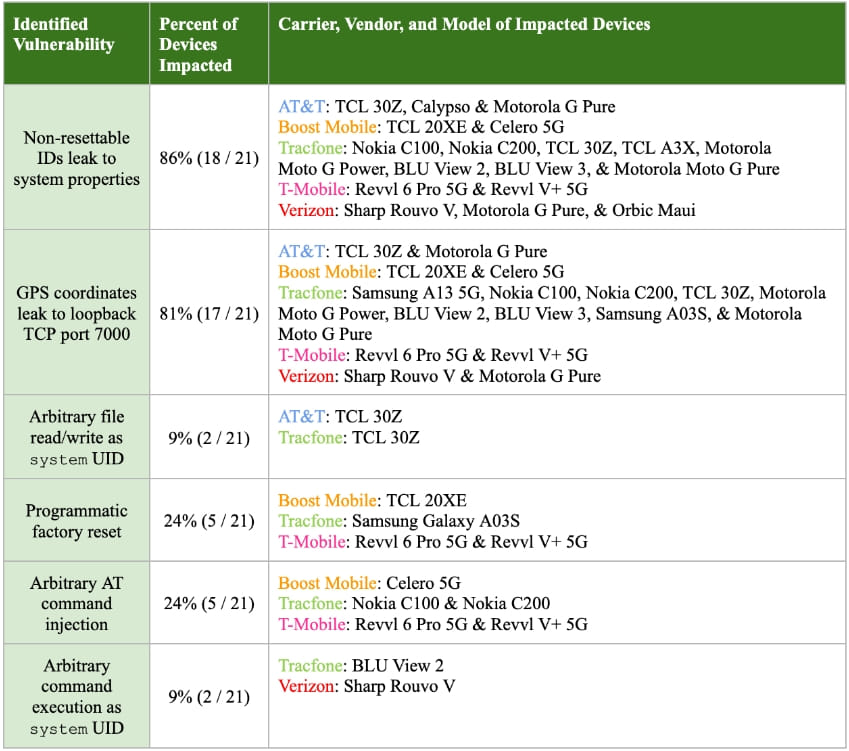
First, Quokka estimated the risk of the pre-loaded carrier apps it found on the examined devices and discovered that most of them are susceptible to persistent user and geolocational tracking. Other problems include arbitrary file access (data breach), forcing factory reset (data loss), command injection, and arbitrary command execution with high privileges.
These vulnerabilities are present on the devices due to the improper implementation of Android’s “Intents,” an internal messaging system used between apps and Android system components to exchange data as needed. Vulnerabilities in the apps and the implementation of the intents component allow third-party apps to potentially intercept their communications with Android’s system and gain access to data that should otherwise be out of reach for them.
Such malicious apps could be anything, appearing totally legitimate, and not requiring to have secured risky or extensive permissions in order to snatch the sensitive data from the carrier apps, so the user would have no way to realize the interception that takes place in the background.
For example, in eighteen out of the twenty-one tested devices, the pre-installed software obtains a non-resettable device identifier that a malicious third-party app can grab without any permissions and then use it as a persistent tracking number.
More worryingly, in 17 of the examined devices, powered by a MediaTek chipset, a pre-installed binary opens a TCP port 7000 and transmits the GPS coordinates to any clients connected to the debug port. A malware app on the same device could easily take advantage of this to infer the device’s location every time the user enables the GPS module.
Protect from carrier bloatware
The general idea for users looking to protect their data while enjoying the advanced capabilities of smartphones would be to use as clean operating systems as possible that do not come pre-loaded with apps and tools, which, in most cases, cannot be deleted. The fewer intermediaries between the device manufacturer and the customer, the less bloatware there generally is on the device.
Mainstream examples include Google’s Pixel line and Apple’s iPhones, but there are also Android distributions that can be installed on any device which feature advanced privacy systems, like GrapheneOS.
Finally, consumers should consider the Murena Fairphone 4, that has recently entered the U.S. market, and which runs a de-Googled and privacy-enhanced Android OS named ‘/e/OS.’

 New TunnelCrack Attack Diverts VPN Traffic Outside the Protected Tunnel
New TunnelCrack Attack Diverts VPN Traffic Outside the Protected Tunnel
Interestingly, Canada which has the highest cell phone plans in the western (developed world) got rid of carrier “locked” phones many years ago to make it in-line with world providers.
Oddly, the US is the only country in the world that still has carrier locked phones. Carrier locked phones always had bloatware. Even OEM unlocked phones do, like from Samsung. Many of the apps can’t be uninstalled, only disabled. They still consumer resources and are waiting to be “woken” up.
The latest iPhone iteration is the only phone in the world that is eSIM only with no physical SIM slot. Everywhere outside North American having two mobile numbers is common, whether it’s for voice only, voice/data, or another line for data only.
It will be interesting to see given the limitations around QR codes (eSIM) et al. will play out in the next few years.
But anyway, if the US didn’t have locked phones this bloatware would never be a problem.”