
It seems we can’t go more than a few days without news of another giant ransomware attack somewhere in the world. These attacks are big news and they impose big costs and problems for everyone — from individuals to major corporations and governments. Most recently, supply chains have been getting pounded, with attacks on targets like fuel pipelines and network management systems.
It has gotten so bad that this year, the World Economic Forum (WEF) is running Cyber Polygon, a training session focused on protecting against these types of cyberattacks.
So let’s start with the basics and define exactly what we’re talking about.
A definition of ransomware
Ransomware is a type of malware. When a person or organization is the target of a ransomware attack, the threat is that the victim’s data is being held hostage and won’t be returned until the victim makes the required ransom payment.
The developers of ransomware frequently design it to be able to spread across a network, attacking not only other user’s computers, but the servers they are connected to. Similarly, with the Kaseya ransomware attack, several downstream businesses and organizations were affected.
These attacks can bring an entire organization to its knees. And while ransomware previously targeted mostly individuals, today the main targets seem to be large organizations like governments, major corporations, and universities. Here are two reasons why:
- Profits: Large organizations can afford multi-million dollar payouts, as we have seen recently with both the Colonial Pipeline ransomware payout and also the JBS payout, both in the tens of millions of dollars.
- Visibility: When hackers gain access to high-profile targets, they are guaranteed to grab the international spotlight with news reports around the world. This brings more fame to the hackers, which in turn, may help them to extract more money from their victims.
The volume of ransomware attacks seems to be growing rapidly, with the ransoms that are being demanded growing even faster.
The main types of ransomware
At the most general level, there are three main types of ransomware. We’ll look at each one quickly, then spend the rest of the article on the worst type of ransomware.
1. Scareware
Scareware is a term for all those rogue security software and tech support scams that pop up scary-looking messages on your screen or otherwise try to trick you into calling a phone number where someone will ‘help you solve the problem.’
In reality, there’s nothing wrong with your system, aside from the presence of pop-ups with fake warnings. If you simply ignore the annoying messages your system should continue to work fine.
You might receive a pop-up message claiming that malware was discovered and the only way to get rid of it is to pay up. If you do nothing, you’ll likely continue to be bombarded with pop-ups, but your files are essentially safe.
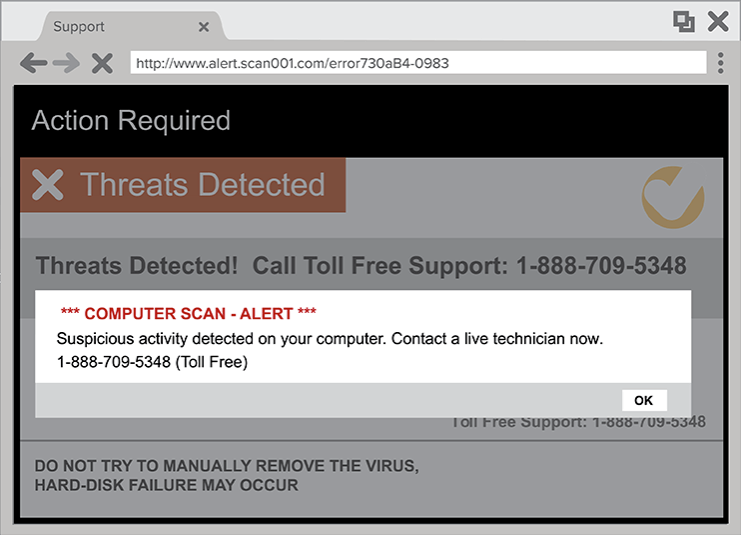
Think about it. Do real tech support companies remotely scan your computer without permission? Do legitimate security apps suddenly appear on your system when there’s a problem? All this stuff is trickery to get you on the phone with some smooth salesperson who will try to talk you into paying to get ‘the problem’ on your device fixed.
2. Screen-locking ransomware
This type of ransomware is a much more serious problem. This stuff can really prevent you from getting access to your device and or files. It usually works something like this:
You start your computer, but instead of your normal starting screen, you see a full-sized window with some sort of scary text, maybe even the FBI or US Department of Justice seal. The message tells you that the Feds have somehow detected illegal activities on your computer and you must immediately pay a fine.
But this isn’t how law enforcement works. If the Feds somehow decided you were doing something really bad on your computer, they wouldn’t send you a message to pay a fine. They might bust down you front door and drag you off to a cell, but they definitely would never lock your screen and send you annoying messages.
The good thing about this kind of ransomware is that all your stuff is probably still safe and sound on your computer. You (or some skilled computer tech) might be able to uninstall the ransomware and give you access to your files again.
3. Encrypting ransomware
Now we’re talking about the really nasty type of ransomware. This is the kind of ransomware that figures so prominently in the news these days (particularly in the United States). The Kaseya ransomware attack is just the biggest and most recent in a series of attacks on critical infrastructure and supply chains. Reportedly well over 1,000 businesses worldwide are currently crippled thanks to this ransomware attack.
The reason that this kind of attack is so much more of a big deal than scareware or screen-locking ransomware has to do with encryption. When a device is successfully attacked by this kind of malware, it encrypts and locks up the files on the device.

Usually, this type of ransomware comes with a simple proposition: pay the ransom to get the decryption key and access your files, or you’ll never see your data again.
If you do pay the ransom (these days usually in the form of Bitcoin), and you are very lucky, the cyber crooks responsible for the attack may send you a decryption key. Assuming the decryption key is legitimate, you will be able to decrypt your data and restore your system to functionality.
Of course the decryption key might not work. And the bad guys might have installed other nasty surprises on your device so they can hit you for more money in the future. And the decryption software might screw up sometimes, randomly destroying some of your files, regardless of your payment. Alternatively, the hackers could simply accept your payment and leave your files permanently encrypted.
Finally, from the privacy perspective, there’s nothing to prevent the hackers from downloading a copy of all your personal files before they encrypt them. Wouldn’t that be an unhappy ending: the files on your computer are destroyed, while the hackers are happily selling all your personal information on the Dark Web.
If you suspect something is wrong, the first thing you can do is completely cut all internet access to the infected machine.
How encrypting ransomware attacks work
While there are variations between individual ransomware infections, they basically work like this:
- Once the ransomware gets onto your device, it starts to encrypt the files on the device. As it encrypts a file, it either deletes it, or sometimes sends a copy of the file back to the hackers for further mischief.
- Once the damage is done, the ransomware starts displaying a ransom message. That message can either be a new desktop background, or a full-screen image displayed by a custom app.
- The message that the victim sees is really a threat. If the victim will quickly pay the ransom, then the hackers will supposedly use a decryption key to restore the victim’s files. If the victim doesn’t pay the ransom, the hacker simply won’t restore the files, leaving the victim in a world of hurt.
- To (attempt to) avoid getting arrested for holding the victim’s files hostage, today’s ransomware bandits usually include a Bitcoin address to receive the ransom payment. Bitcoin isn’t a totally anonymous payment method, but it does give the bad guys a good chance to get away with the money.
- If the victim sends the right amount of Bitcoin to the specified address, the hackers are supposed to send the victim a file or password.
- The victim can use this file or password to activate a decryption program the ransomware installed on the victim’s computer. Best case, it will decrypt the files and then delete all traces of the ransomware from the device.
Even this best case isn’t a very good situation. You will have sent a lot of money to someone who held your important data hostage. And you will be relying on the same people who just robbed you to do the work necessary to release your data, after they already have your money. This is not a great position to be in.
How to protect yourself against ransomware
Here are a few things you can do to protect yourself against ransomware. Some of these suggestions can help you avoid getting hit by ransomware attacks in the first place. Others could help you avoid additional damage from ransomware attacks after one or more of your devices has already been hit.
Here are our suggestions, in order of priority:
- Back up your data regularly. This is the #1 way to recover after ransomware attacks. Sometimes the best thing you can do after an attack is to reinstall the operating system on all infected systems, then restore files from backups. It would be a pain to have to do this, but when the alternative is to pay some proven thieves and hope they make everything right, it is probably the best way to ensure that your systems are safe after an attack. Plus you will save the money that would otherwise have gone to the hackers.
- Make sure your backups are secure. Some ransomware can look for backups on external drives or elsewhere on the network. Make sure to do your backups then isolate them from the system you are backing up to prevent smart ransomware from encrypting your backups too.
- Use security software. Ensure that all your computers and mobile devices have security software installed on them. This will greatly reduce the risk of ransomware getting installed on them.
- Keep operating systems and security software up to date. Operating system and security software updates often contain fixes for security flaws that ransomware (and other malware) can use to subvert your systems. Keeping everything updated reduces the chances of ransomware getting onto your system.
- Use secure network connections. Public Wi-Fi networks are generally not secure, and using them can give hackers an easy way to install all sorts of malware. If you must use public Wi-Fi networks, be sure to install and use a VPN. The VPN will encrypt your communications, blocking hackers from getting at your systems through an unsecured network. See our list of the best VPN services for more info on this topic.
Ransomware FAQ
We’ve given you the main story on ransomware above. But there are always side issues that come up. Here are some of the most frequently asked questions about ransomware.
What is ransomware-as-a-service (RaaS)?
Ransomware-as-a-service is a cybercrime economic model that allows malware developers to earn money for their creations without the need to distribute their threats. Non-technical criminals buy their wares and launch the infections, while paying the developers a percentage of their take. The developers run relatively few risks, and their customers do most of the work.
Some instances of ransomware-as-a-service use subscriptions while others require registration to gain access to the ransomware. Learn more about ransomware-as-a-service here.
Who do ransomware authors like to target?
A few years ago, ransomware authors mostly targeted individuals. But that has changed over the years. Today, ransomware writers mostly target big businesses, governments, and universities.
This makes sense. As Willie Sutton supposedly said when asked why he robbed banks, that’s where the money is. Big organizations with critical information stored on their computers have both the money and the motivation to pay big bucks in hopes of getting their data back.
Are Mac users safe from ransomware?
Several years ago, it was true that Mac users didn’t need to worry about ransomware attacks on their computers. That all changed in 2016, when KeRanger ransomware started appearing on Macs.
Apple quickly updated its XProtect anti-malware program to stop KeRanger. However, that doesn’t guarantee that new Mac ransomware won’t show up sooner or later.
Are Linux systems immune to ransomware?
Sorry, no.
Linux systems have been getting hit with ransomware attacks since at least 2017, when Erebus infected a South Korean web hosting company.
What about Android and iOS? Do they get ransomware too?
Sorry again.
Even our beloved smartphones can be infected with ransomware. It appears that iOS devices are less likely to get infected than Android ones, but neither type of device is immune.
Who can I report ransomware attacks to?
Assuming you are in the United States, the FBI suggests some ways of filing a complaint or reporting ransomware incidents. These include:
- Filing a complaint with the Internet Crime Complaint Center (IC3): https://ic3.gov/Home/Ransomware
- Reporting the incident to the Cybersecurity & Infrastructure Security Agency (CISA): https://us-cert.cisa.gov/report
- Contacting the National Cyber Investigative Joint Task Force (NCIJTF): 1-855-292-3937
Conclusion
Ransomware is one of the biggest threats to the Western world’s computerized infrastructure, supply chains, and other internet-connected systems. At the personal level, ransomware attacks could prevent you from accessing your own critical data. In the worst case scenario, a ransomware attack could turn into a major privacy disaster, with your personal information splashed across the internet as punishment for not paying the ransom demanded by the hackers.
There are things you can do to protect your systems from this scourge, but keeping current backups of your most important files and being ready to rebuild every infected system from scratch rather than pay a ransom to (maybe) get your data back, could still be the best solution of all.

Leave a Reply