
The Dark web has a mysterious reputation. We’ve all heard rumors about the bad things you can find on the Dark web — but it’s also a resource for information. After all, some of the biggest threat actors host websites on the Dark web discussing their exploits. Others use the Dark web to simply post information that may be censored elsewhere. But how do you go about accessing the Dark web safely?
Ultimately, the Dark web has the allure of a place that most people can’t visit. Since you are reading this, we suspect that you feel the pull of this place and want to take a look for yourself. But you’ll have to be careful not to wander into something you don’t want to see.
You can access the Dark web safely, but just diving in blindly is a bad idea. This is like going spelunking without the proper equipment — you’re likely to get hurt, possibly very badly. We’re going to get you oriented for this journey as fast as possible, then give you the tools you need to get down to the Dark web and look around for yourself.
There are two webs
We usually talk about the World Wide Web (a.k.a. the web) as if it was one thing. But there are actually two webs: the Surface web and the Deep web.
The Surface web
The Surface Web (also referred toy as the Visible Web, the Indexed Web, the Lightnet, and the Clearnet) is the part of the World Wide Web that most of us are familiar with. It is where you are reading this article. If you can find a page with a standard search engine (Google or DuckDuckGo) and visit it with a standard web browser (Chrome or Firefox), it is part of the Surface web.
It is hard to say exactly how large the Surface web actually is. Here’s a quote from Google that gives some idea of the amount of information we’re dealing with:
The Google Search index contains hundreds of billions of webpages and is well over 100,000,000 gigabytes in size. It’s like the index in the back of a book — with an entry for every word seen on every webpage we index. When we index a webpage, we add it to the entries for all of the words it contains.
We do know two things about this: the Surface web is enormous, and it comprises only a small portion of the total web. The majority of the World Wide Web exists in the Deep web.
The Deep web
The Deep web (also known as the Invisible web or the Hidden web) is the part of the World Wide Web that is not visible to standard search engines like Google or DuckDuckGo. While no one knows the exact amount, the total amount of content on the Deep web is believed to be many times as great as that of the Surface web. We’ve often seen estimates that the Deep web is 10 to 20 times as large as the Surface web.
Much of the Deep web consists of databases and intranets that are not accessible without some sort of permission. Most of the rest consists of websites that cannot be reached using standard internet protocols. Those hard-to-access websites are collectively known as the Dark web.
The Dark web
While there is no official naming convention for these things, a common definition of the Dark web is that part of the Deep web that you need specialized tools to visit. You can’t just look up some Dark web page in your regular search engine and dive head first into the darkness. You need a specialized browser and either a specialized search engine or direct knowledge of an address to reach Dark web pages.
The most commonly-known portion of the Dark web is the Tor network. While there are other networks in the Dark web such as I2P ( the Invisible Internet Project), Freenet, and Riffle, we’re going to concentrate on the Tor network for exploring the Dark web.
You can’t visit the Tor network using regular web browsers that work with regular internet protocols. The network functions differently than the World Wide Web you are used to, and has its own protocols that a browser must use to gain access.
You can connect to the Tor network using the Tor browser, a custom web browser designed specifically to work with this network. A popular Surface web browser called Brave browser now also has the ability to connect to the Tor network, so we’ll look at that too.
Tools to access the Dark web
Before we go any further into the dark (web), here’s a summary of the tools we are going to talk about:
The Tor browser
The Tor browser connects directly with the Tor network. It is designed for anonymous web browsing, and has various features (and limitations) that help achieve this.
The Brave browser
The Brave browser is a privacy-oriented Surface web browser that can also connect to the Tor network. To provide more secure access to the Tor network, in 2020 Brave launched its own Tor Onion Service.
Opening a new Brave window with Tor connectivity is incredibly simple:
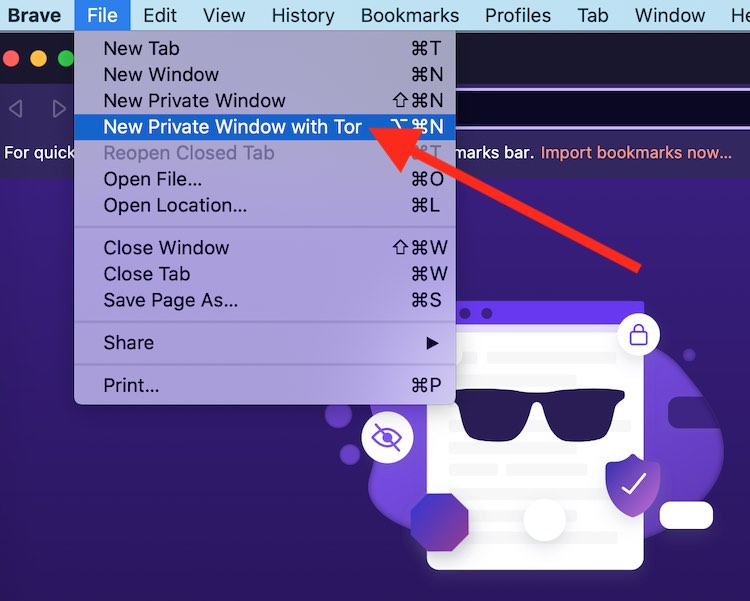
But before doing this, you should connect to a VPN.
You can download Brave here.
A good VPN (virtual private network)
While many people trust the Tor network to provide them with anonymity while using the internet, the network is not perfect. It has been hacked, and there are other ways that hostile forces (from hackers to national security agencies) have been able to compromise the security of the Tor network.
Combining a high-end VPN service with the Tor network adds another layer of defense that will make using the Tor network safer for you. Here is what your VPN will look like with a desktop app running in the background (NordVPN) while you browse the Dark web.
VPNs to use when browsing the Dark web
We have an overview of the best VPN services here.
Currently, our top two recommendations are NordVPN and Surfshark. They both provide the strong security and privacy that is so important when delving into the Dark web. In addition, they are both fast, thanks to their built-in support for the WireGuard VPN protocol. WireGuard is not only extremely fast, but it uses the Transmission Control Protocol (TCP), which is compatible with the Tor network. We used NordVPN when creating the examples in this article.
Check out our guide on the best VPNs for the Dark Web for more info. We also have a guide on Dark Web scans to check if your personal data is exposed.
Accessing the Dark web with the Tor browser
The ‘traditional’ way to use the Dark web is with the Tor browser and network. So we’ll talk about that first.
Who created and runs Tor?
Researchers at the US Naval Research Laboratory created Tor. More specifically, in the 1990s, they invented onion routing, a protocol that makes anonymous communication in a network possible. Messages are protected by multiple layers of encryption, then passed through multiple servers (called nodes). Each node peels away another layer of encryption, like peeling an onion before finally being sent to its final destination.
Tor (The Onion Router) is FOSS (Free and Open Source Software) that allows you to send messages over the Tor network of onion routing nodes. The Tor project is a 501(c)(3) non-profit organization that maintains the Tor software. Tor nodes are owned and operated by volunteers around the world.
How does Tor protect your privacy?
Tor protects your privacy by passing your messages through three nodes in the worldwide Tor network. Thanks to the onion routing used in this network, no node can know both the origin and destination of a message.
As with a VPN, the recipient of a message you send through the Tor network can’t know your IP address, so they can’t associate specific messages with your address. The key difference between Tor and a VPN is that the VPN route your message travel through can associate your IP address with the messages you send, while a Tor node cannot know both your IP address and the content of the message. More simply, when you use a VPN, you have to trust VPN company to protect your privacy. When you use Tor, you don’t need to trust anyone.
Unfortunately, even the Tor network is not perfect.
To function securely, the Tor network nodes need to be running the official Tor software. An attacker can add subverted nodes to the volunteer-run Tor network and cause various kinds of problems. On ongoing example is described in this article at TheRecord.
Reportedly, an attacker has been adding thousands of compromised nodes to the Tor network since January 2020. These nodes identify themselves as exit nodes. Tor network exit nodes strip off the final layer of encryption protecting a message before sending it on to its final destination. This means the node can see the contents of the message, even though it doesn’t know who sent the message.
However, this doesn’t matter for this particular attacker. The subverted nodes look for messages involving cryptocurrency transactions, and appear to redirect cryptocurrency transactions to the attackers own digital wallets. The Tor team keeps detecting and disabling the bad exit nodes, but the attacker keeps deploying new ones.
Attackers can also use timing analysis / traffic analysis to try to trace messages entering and leaving the Tor network. By monitoring the size of messages and time when messages enter and leave the network, it may be possible to match senders and recipients. Something along the lines of:
A message of this size entered the network at time X from a computer with this IP address. A message of the same size left the network headed for a different computer at time X+Y. By monitoring as much Tor network traffic as possible and looking for similar patterns, the attacker could become more and more certain of the identities (IP addresses) of the computers on each end of a stream of messages, and eliminating the anonymity of the people involved.
The weaknesses of Tor are why you need a VPN too
Using a VPN and Tor together can address the Tor weaknesses we have just discussed. A VPN encrypts your messages, then passes them to a VPN server that decrypts the message before sending it on to its final destination. In addition, the VPN server replaces the IP address in the decrypted message. This makes it look like the message originated at the VPN server instead of at your device.
Combining a VPN with Tor gives your messages an additional layer of encryption along with the increased privacy of hiding your actual IP address. You can find out a lot more about the ways these two systems work in our VPN vs Tor comparison.
Let’s look at how this works. We’re going to focus on the approach called Tor over VPN, or Onion over VPN. In this approach, you first connect to a secure VPN, then pass messages through the Tor network. With this setup, your messages are encrypted before they enter the Tor network, and decrypted after they leave the network.
A traffic analysis type attack could determine that you are using a VPN, but the contents of your messages would not be exposed. Nor would your IP address or the IP address of the person(s) you are communicating with be exposed to the Tor network.
There are a few ways to set up a Tor over VPN connection. You can:
- Connect to a VPN, then launch the Tor browser to use the Tor network
- Subscribe to a VPN service that implements Tor over VPN for you
- Connect to a VPN, then launch the Brave browser’s Private Window with Tor Connectivity
We’re going to show you how to do this using Brave. Why Brave instead of the Tor browser?
The Tor browser is optimized for working with the Dark web. But it is not particularly easy to use, and isn’t designed for working with the Surface web.
Brave is a popular Surface web browser with some built-in privacy features. While the vast majority of its users stick to the Surface web, it takes only a couple of clicks to open a new Brave window and access the Dark web. This makes Brave much more convenient for casual trips into the darkness than the Tor browser. It is also one of the top recommendations in our list of secure browsers.
How to access the Dark web using a VPN and Brave
Here are the steps to start exploring the Dark web using a VPN and Brave. While we recommend using either NordVPN or Surfshark for this, we’ll use NordVPN in these examples for simplicity:
- Download and install NordVPN.
- Launch the NordVPN desktop app. Select Settings, then Auto-connect.
- Disable the Choose a VPN protocol and server automatically option.
- In the VPN protocol drop-down menu, select NordLynx.
- Use the back arrow in the top-left corner of the dialog box to return to the NordVPN client’s main screen.
- Connect to a VPN server. Because the Tor network is inherently slow, it makes sense to connect to the VPN server closest to your physical location.
- Download and install the Brave browser.
- Launch Brave. Press the ALT+SHIFT+N keyboard shortcut to open a new Brave Private Window with Tor Connectivity. Using this new window you can browse the Dark web using a Tor over VPN connection.
We have more tips in our guide on using a VPN for the Dark Web and Tor network.
Where can you go now?
Now that you’re connected to the Dark web, you need someplace to go. This is where things can get dicey. There are perfectly acceptable resources on the Dark web.
Note: The next two links take you to Dark web sites. You’ll get an error if you try to reach them with your regular web browser, but should have no problem if you use the Brave or Tor browsers.
For example, here’s the New York Times:
https://www.nytimes3xbfgragh.onion/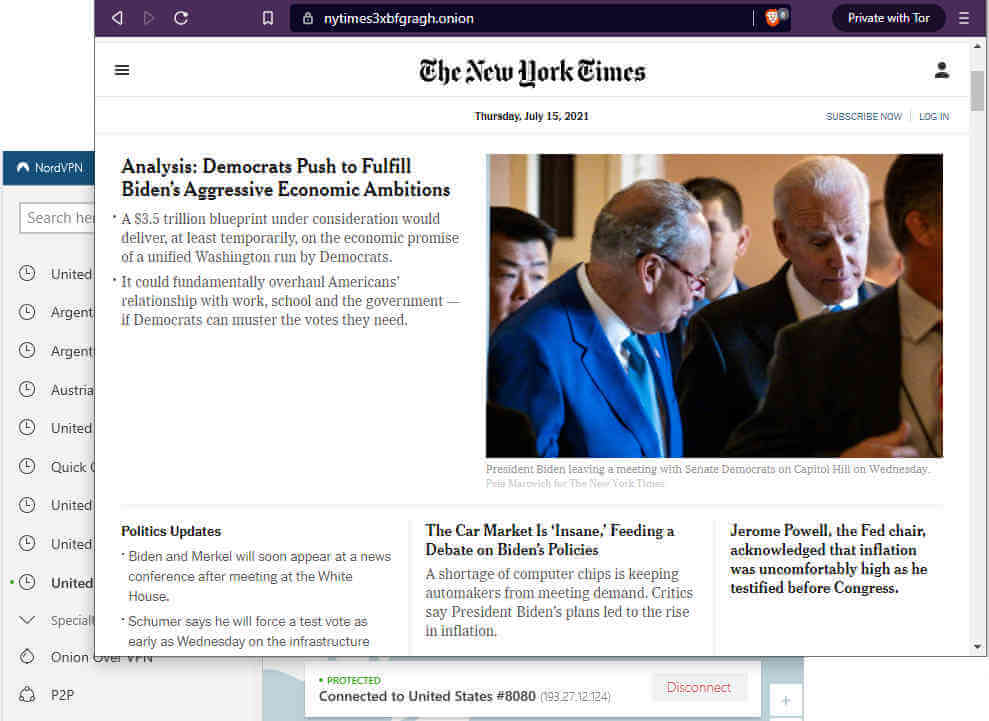
But there are lots of sites down there that you wouldn’t want to show to your grandmother. Fortunately, there are a few reasonably good indexes of Dark web sites available. They are indexed by hand, so they frequently include broken links, but they are the best way available to find your way around. The Hidden Wiki has been around for several years, and seems like a reasonably safe place to set you loose.
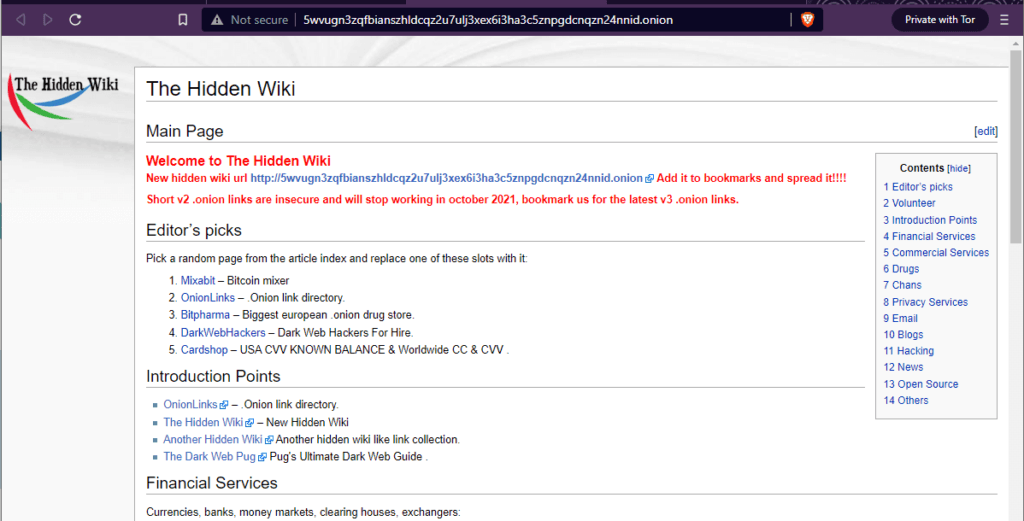
Just be sure to always launch your VPN before accessing the Dark web (via Brave or the Tor browser) for maximum protection when messing around down here.
Dark web FAQ
Given the controversial nature of the Dark web, people have lots of questions. Here are some of the ones we run into most frequently:
Is it legal to use the Tor network?
Perhaps surprisingly, we don’t know of anywhere that using the Tor network is illegal. While you might think that Tor would be banned all over the place, many different types of people rely on it, including governments and law enforcement agencies.
Will visiting the Dark web attract attention?
It is highly likely that intelligence agencies and law enforcement do their best to monitor who visits the Dark web, or at least certain sites on the Dark web. Those organizations hate the idea that someone could be doing something online that they cannot monitor.
The fact that you are using the Tor network is likely enough to pique their interest. The fact that you are using it to visit the Dark web probably makes you even more interesting. According to this old CNet article, the NSA has likely been tracking anyone who checks out Tor or any other privacy/anonymity tools since 2014 or earlier.
Can the Tor network be hacked?
Yes, the Tor network can be hacked. It has been hacked before, and there is evidence that it is being hacked right now. This is one reason why it is crucial to use a VPN when you are using the Tor network. Nothing is 100% secure, but using the Tor network is safer than using the open internet. And using a Tor over VPN connection is safer still.
However, if you are doing something that will motivate the NSA, or other powerful security agencies like Pakistan’s ISI to come after you, there is probably little you can do to survive.
What are Onion Services?
Onion services (formerly known as Tor Hidden Services) are the hidden services that you can reach through the Tor network and a compatible web browser. Onion Services exist on the Dark web. You can use the Tor Browser or Brave to reach the Dark web.
Conclusion
The Dark web is the part of the World Wide Web that you need special tools to visit. It is a much less civilized place than the Surface web where most of us spend our time. While there are some innocuous sites and services on the Dark web, there are also many places that offer illegal goods and services.
The Dark web is also a place where your computer or other devices could pick up nasty infections, get sucked into a botnet, or otherwise get into lots of trouble.
You can access the Dark web reasonably safely if you do two things:
- Follow the instructions we’ve published here for how to use the Tor network with a VPN.
- Remember that the Dark web is a place with no rules and if you go poking around in dark corners you could get hurt.
Good luck!

Now that i know hot to access where do i find a list of available links and websites bc i dont know the names.
Yes, you can access the Dark web through Whonix and Tails, which are dedicated operating systems, but there are a few drawbacks:
– It is more difficult than just starting up a VPN on your desktop and opening a new window with Tor in Brave.
– It puts all your trust in the Tor network and is difficult to use with a VPN (unless you run Whonix or Tails in a virtual machine and a VPN on your desktop)
only mobile
how I can use please help me
I use PrivadoVPN, I don’t surf the dark web at all. PrivadoVPN comes with openvpn and I use the openvpn connection to keep me truly anonymous and I also use DuckDuckGo.
Hi David,
I’m not sure why you say that “NordVPN does not support NordLynx”. It is their default protocol. With the newest update (as of 20 Oct 2022) and every version that I know of before that, you open NordVPN, click the “gear” (settings) icon, then ‘Connection’, and the 3 available protocols are NordLynx (default), OpenVPN(TCP), and OpenVPN(UDP).
I would use the tor browser but i am unable to successfully connect to it.