
A security researcher has discovered multiple vulnerabilities impacting the Linux version of the CyberGhost VPN client, which could be exploited for remote code execution and man-in-the-middle attacks.
The flaws that impacted CyberGhost VPN for Linux version 1.3.5 and older were discovered and reported to the leading VPN provider on December 01, 2022.
The vendor partially fixed the flaws with the release of version 1.4.0 on December 24, 2022. On February 22, 2023, CyberGhost VPN released version 1.4.1, which fully addressed all discovered vulnerabilities.
However, because the CyberGhost VPN client for Linux does not update automatically, users need to download and apply the security update themselves manually.
Vulnerability Details
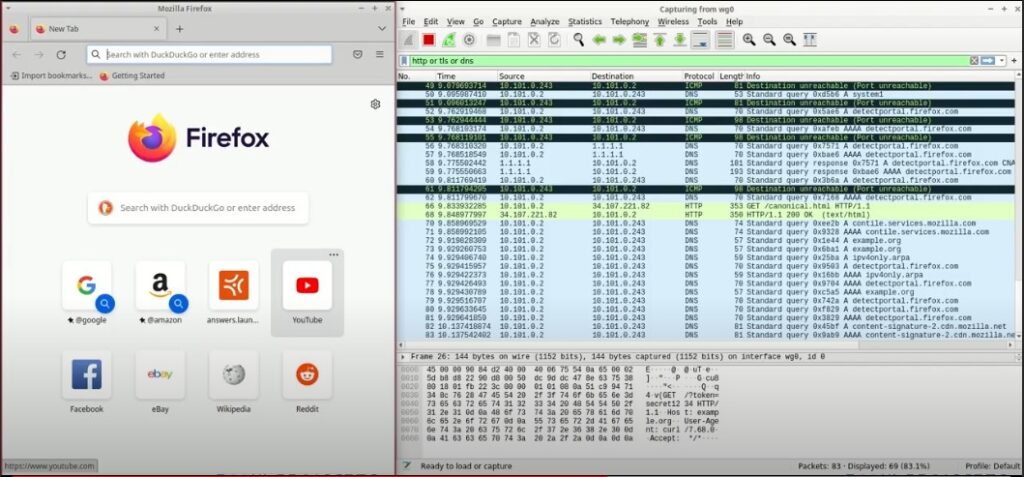
The first flaw, which is also the basis for the second problem, is a lack of certificate validation in the communication between the CyberGhost API and the VPN client. This could lead to the client trusting an illegitimate server created by an attacker that imitates the vendor’s API. In that case, the attacker could capture all data packets exchanged between the client and the network, essentially performing a man-in-the-middle attack.
“The only prerequisite to conduct the attack is to make the client connect to the illegitimate API. This prerequisite requires an attacker to have the ability to successfully conduct a DNS cache poisoning attack, or to perform ARP spoofing if they’re on the same local network. Malicious ISPs and hackers exploiting intermediate network devices or DNS servers are also in a perfect position to redirect the traffic.”
– mmmds.pl
mmmds.pl
The second issue concerns an attacker’s capability to perform command injection on the vulnerable device after exploiting the lack of certificate validation issue described previously. When establishing a connection with the phony server, the client sends a Wireguard configuration file by issuing a shell command, to which the malicious server can respond with a command injection payload. This payload can be executed on the victim’s machine with root user privileges, giving the attacker complete control over the vulnerable device.
The third and final problem is an attacker’s ability to perform local privilege escalation by abusing one of the VPN’s client helper functions and, more specifically, its interaction with the operating system. An unprivileged user can modify the client’s configuration file, located in a directory accessible by all users, and inject commands that elevate their privileges to root.
The researcher has also posted videos to showcase the exploitation of the issues on his writeup but provided limited technical details on the first two flaws to avoid generating attack waves targeting users who haven’t patched yet.
For those unable to upgrade the CyberGhost VPN for Linux client to version 1.4.1, it is recommended to switch their connection type from Wireguard to OpenVPN, which mitigates the man-in-the-middle and remote code execution issues.

 How to Check if Your Data Was Sold on the Genesis Market
How to Check if Your Data Was Sold on the Genesis Market
CyberGhost is owned by Kape Technologies, right?
Yes that is correct.
It’s ok. It’s affecting Linux only. Lol.
Anyway, we need some more information on the US’s RESTRICT Act!