
A secure browser that protects your privacy is a critical tool for staying safe online and keeping your data secure from third parties. We have been reviewing, testing, and ranking browsers for the past six years and this guide contains the latest recommendations for 2024.
Do you want a secure browser that truly keeps your data private? Well, you may be surprised by how much of your data is actually getting exposed.
WARNING: Many browsers today are actually data collection tools for advertising companies. This is the case for Google Chrome, the largest and most popular browser. By collecting data through your browser, these companies can make money through their advertising partners with targeted ads. We see this same privacy-abusing business model with search engines, email services, and even free mobile apps.
Unless properly configured, most browsers contain lots of private information that can be exploited – or simply collected – by various third parties:
- Browsing history: all the websites you visit
- Login credentials: usernames and passwords
- Cookies and trackers: these are placed on your browser by the sites you visit
- Autofill information: names, addresses, phone numbers, etc.
And as we will explain further below, using “private” or “incognito” browsing will not protect you. Your IP address will remain exposed and various third parties can still track all of your activities. And even legal action may not protect you. Here is a recent headline related to a lawsuit against Google for capturing data from users who are in Incognito mode. This case has been going on for years now and isn’t close to resolution yet.
And even with a locked-down and hardened browser, exploits may still be found that expose your data and possibly your identity. For example, in 2021 there was a spate of zero-day exploits in Google Chrome with various effects up to allowing hackers to remotely execute code on affected systems. We discuss some other privacy issues (and solutions) in our guides on browser fingerprinting and also WebRTC leaks.
But don’t panic. Effective solutions and tools exist to deal with these problems and we cover them in detail in this article. In this browser security and privacy guide, we’re going to explain the following topics:
- Best secure browsers that respect your privacy
- Problems with other browsers
- Browser privacy compartmentalization
- Secure browser add-ons
- “Private browsing” mode is NOT very private (and why you need a VPN in addition to a secure browser)
Incognito / Private browsing mode still leaves you EXPOSED
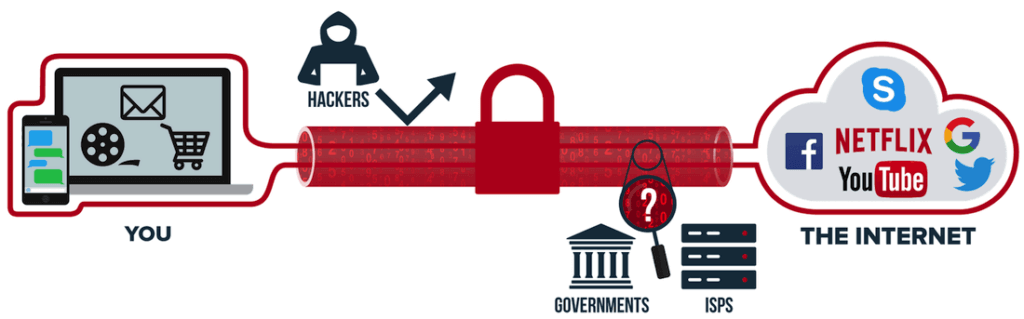
When using “private” or “incognito” browsing mode in your browser, your real IP address and location are still being revealed to every website, ad, and tracker that loads in your browser. Additionally, all your activities remain visible to your internet service provider (ISP). And at least here in the United States, ISPs log everything you do online and share the data with many other parties. This is why it’s critical to use a good VPN for basic digital privacy.
The best way to achieve true privacy while hiding your real IP address and online activities is to use a secure browser together with a good VPN. This protects you at both ends of the line, and in the middle too.
The secure browser will protect you as described in this article, while the VPN will protect your identity by hiding your real IP address and location. The VPN will also encrypt your traffic so your ISP (and any other snoops out there) cannot see your activities online. Here are our top three recommendations from the best VPN list that we have tested and reviewed:
- NordVPN: A fast, secure, audited VPN with advanced privacy features, built-in ad blocker, and a strict no-logs policy, based in Panama (see the 74% off coupon).
- Surfshark VPN: A no-logs VPN service with a large lineup of privacy and security features, based in The Netherlands.
- ExpressVPN – This is a secure and reliable VPN that boasts some great privacy features and also works well for streaming. It is based in the British Virgin Islands.
Now let’s examine the most secure browsers you can combine with a VPN for maximum privacy.
Secure browsers that protect your privacy
In this section we will examine the best browsers based on two main factors:
- Security: How well does the browser protect you from hackers, vulnerabilities, and online exploits?
- Privacy: How much data is the browser itself collecting about you and who is this data being shared with? How does the browser protect your privacy?
Conflicting opinions! Just like with Tor, opinions about browser privacy and security can be wildly divergent and contentious.
This guide is not meant to sell everyone on one browser that beats all others. Rather, it is a summary of information about different web browsers that do well with both privacy and security. Choose the best browser for you based on your own unique needs and threat model.
Here are the most secure and private browsers for 2024:
1. Brave: The most secure and private browser (for both desktop and mobile)

Brave is arguably the most secure browser with simple, out-of-the-box privacy. It is a Chromium-based browser that is fast, secure, and privacy-focused by default. It has a built-in ad blocker and browser fingerprinting protection, while also giving you access to numerous add-ons and extensions. The main developer behind Brave is Brandon Eich, who formerly worked for Mozilla.
To summarize this browser, Brave is based on open-source Chromium, but configured for more privacy. It does well with its default privacy settings and extra features. Here is a brief overview:
- Blocks ads and trackers by default
- Protects against browser fingerprinting and even offers fingerprint randomization
- Built-in script blocker
- Blocks all third-party storage
- Easy access to the Tor network
One of the reasons we like Brave is because it offers simple, out-of-the-box privacy by default. This makes it ideal for those who do not have the time, patience, or know-how for browser customizations and tinkering. Brave can also be used with Chrome extensions, making it an ideal alternative for Chrome. Just download it and you’re good to go.
Tor network – Brave also has a feature that allows you to access the Dark web by simply opening a new window with Tor. We discuss this feature in our guide on how to access the Dark web safely.
Ads – Brave has received some criticism for its ads program, which allows users to “view non-invasive ads without compromising your privacy.” While some people find it hypocritical that a privacy-focused browser has its own ad program, we also see it as a secure funding source. And with many browsers financially struggling, it appears that Brave’s business model is securing this browser’s future and ability to continue to innovate its products.
Here are some more results of Brave’s continuing innovation:
- Brave has developed a private search engine called Brave Search, which is now the default search engine when you do a new installation of the Brave browser. In March of 2023, they added the AI-powered Summarizer to Brave Search.
- A cookie consent blocker, which at least partly frees you from the endless hassle of accepting or rejecting cookies at new sites you visit.
- Brave News, an RSS news reader.
- Brave Wallet, a built-in cryptocurrency wallet.
You can read more about Brave’s privacy features here.
https://brave.com
2. Firefox (when modified and tweaked for privacy)

Firefox is a great all-around browser for privacy and security. It offers strong privacy protection features, many customization options, excellent security, and regular updates with an active development team. The newest versions of Firefox are fast and lightweight with many privacy customization options.

Out of the box, Firefox is not the best for privacy, but it can be customized and hardened, and we show you exactly how in our Firefox privacy modifications guide. Be sure to disable telemetry in Firefox, which is a feature that will collect “technical and interaction data” and also “install and run studies” within your browser.
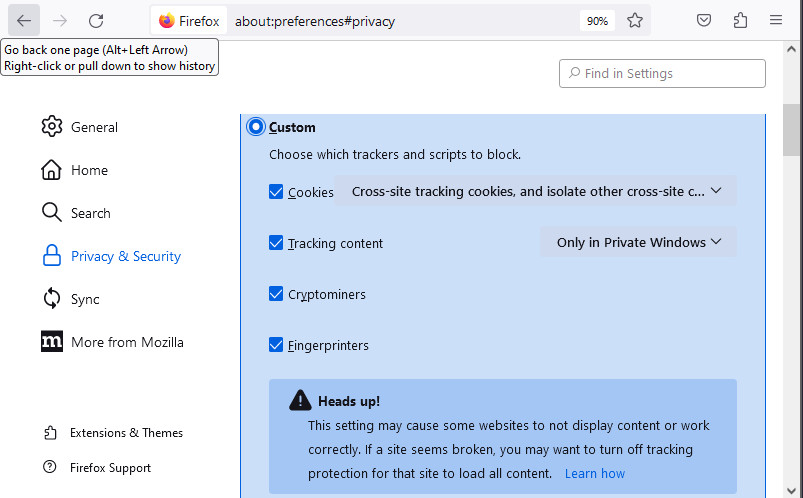
Within the Privacy & Security settings area, there are many useful customization options for different levels of privacy: Standard, Strict, or Custom.
Another great benefit of Firefox is the ability to use numerous browser extensions that can enhance your privacy and security. We’ll go over some of these extensions later in this article.
Firefox highlights:
- Open source code that has been independently audited
- Active development with frequent updates
- Excellent privacy features and customization options
- Total Cookie Protection (TCP) to prevent cookies from tracking you as you move around the web
- Firefox View to easily return to recently used sites
- Built-in ad blocker
- Many browser extensions supported
- Telemetry and tracking need to be manually disabled
- Other modifications necessary for extra privacy and security
If you want to keep using older add-ons that are no longer supported by the latest Firefox release, you can go with the Firefox Extended Support Release (ESR). For those times when you want the maximum privacy viewing content on your Android phone, you could try Firefox Focus.
For additional customization and privacy settings, check out our Firefox privacy guide.
https://www.mozilla.org/firefox
3. Tor browser

Next up we have the Tor browser. The Tor browser is a hardened version of Firefox that is configured to run on the Tor network. By default, the Tor Browser is a secure browser that protects you against browser fingerprinting, but it also has some disadvantages.
Because it uses the Tor network, which routes traffic over three different hops, download speeds with the Tor browser can be quite slow. The default version may also break some sites due to script blocking. Finally, there are drawbacks to the Tor network itself. These include:
- Malicious/dangerous exit nodes
- High latency
- Many websites block IP addresses originating from the Tor network
- Dependence on US government financing, leading some to claim the Tor network to be fundamentally compromised
See the pros and cons of Tor here.
Another option is to use the Tor browser with the Tor network disabled. In this sense, the Tor browser will work like the other secure and private browsers we’ve covered above. Additionally, you can simply run a VPN in the background. Like the Tor network, a VPN will also encrypt your traffic and hide your IP, but it will be much faster.
There’s a new browser out there that takes exactly this approach. It is a collaboration between Mullvad and the Tor project, and you can learn more about it in spot #6 on this list.
Be careful when adjusting the settings for the Tor browser, however, as this may compromise the browser’s built-in privacy and security features.
https://www.torproject.org/
4. Ungoogled Chromium browser

Ungoogled Chromium is an open source project to provide a Chromium browser, without the Google privacy issues:
ungoogled-chromium is Google Chromium, sans dependency on Google web services. It also features some tweaks to enhance privacy, control, and transparency (almost all of which require manual activation or enabling).
ungoogled-chromium retains the default Chromium experience as closely as possible. Unlike other Chromium forks that have their own visions of a web browser, ungoogled-chromium is essentially a drop-in replacement for Chromium.
UPDATE: Support for Ungoogled-Chromium has continued, but it has moved from its original github archive to the new archive linked below. It does require some technical skills to download this browser from the archives.
https://github.com/ungoogled-software/ungoogled-chromium
5. LibreWolf – A private and secure fork of Firefox

LibreWolf is a fork of Firefox that continues to grow in popularity. The project’s stated goals are to deliver a browser that is focused on privacy, security, and freedom. From the LibreWolf website:
LibreWolf is designed to increase protection against tracking and fingerprinting techniques, while also including a few security improvements. This is achieved through our privacy and security oriented settings and patches. LibreWolf also aims to remove all the telemetry, data collection and annoyances, as well as disabling anti-freedom features like DRM.
The website lists the main features of LibreWolf as:
- No Telemetry
- Private Search
- uBlock Origin pre-installed
- Enhanced Privacy
- Fast Updates
- Open Source code
LibreWolf is available for desktop operating systems, including Windows, Mac OS, Linux, and Open BSD. You can find installation instructions here.
One issue to keep in mind, however, is that there are no automatic updates. This means that you will need to manually update the browser, which is certainly a drawback to consider. Fortunately, LibreWolf frequently pushes these browser updates to the relevant archive managers, making it easier to update than it would otherwise be.
LibreWolf is always based on the latest version of Firefox. Updates usually come within three days from each upstream stable release, at times even the same day. Unless problems arise, we always try to release often and in a timely manner.
– LibreWolf FAQ section
This is definitely a browser to consider for those wanting more privacy and security on desktop operating systems.
https://librewolf.net/
6. Mullvad Browser – A privacy collaboration between Mullvad and Tor

When we talked about the Tor browser earlier in this article, we suggested using the Tor browser with the Tor network disabled and a quality VPN might be a better way to go than using the Tor network. We’re not the only people who feel this way. The Mullvad Browser is designed to do exactly this.
This privacy-focused web browser is a joint project between Mullvad VPN and the Tor Project. It incorporates the privacy benefits of the Tor browser such as tracker blocking and fingerprinting. But the Mullvad Browser isn’t designed to connect to the Tor network.
Instead of going through the Tor network, the Mullvad Browser is meant to be connected to the internet through a quality VPN. Obviously, the folks at Mullvad would love for you to use their browser with their VPN, but you don’t have to. In the image below I am using the Mullvad Browser to view this website through NordVPN.
This browser collaboration definitely has potential. To learn more about it, check out our recent article on this Mullvad – Tor project.
https://mullvad.net/en/browser
7. DuckDuckGo private browser (macOS, iOS, and Android)

The DuckDuckGo private browser is available for macOS as well as mobile devices running iOS or Android. It comes with lots of privacy-focused features by default. According to DuckDuckGo, their browser offers:
- Built-in tracking protection
- Encryption upgrades via Smarter Encryption technology
- Easy data management and clearing options
- Fast speeds
Issues with Microsoft trackers
One important thing to be aware of is that security researchers previously discovered that DuckDuckGo’s browser allowed Microsoft trackers. According to DuckDuckGo founder Gabriel Weinberg, this decision was based on a “confidential” agreement between DuckDuckGo and Microsoft.
Many people in the privacy community were outraged when the situation first came to light on Twitter here. There was clearly an element of hypocrisy going on here as we see DuckDuckGo castigate Google over the same practices. But last year, DuckDuckGo announced that they had reached an agreement to block Microsoft trackers.
Should you use DuckDuckGo’s privacy browser? I’d recommend that you consider some of the alternatives we recommend in this guide. That said, the changes DuckDuckGo has made to block the Microsoft trackers makes us much more comfortable with this browser. Ultimately, the choice is yours.
The DuckDuckGo private browser is available on both the Google Play and Apple stores.
8. Waterfox
Waterfox is a fork of Firefox that was maintained by just one person for many years. In February 2020, news broke that the developer of Waterfox sold out to a pay-per-click ad company called System1. However, in July 2023, news broke that Waterfox is once again independent:
I am happy to say that Waterfox is independent again. This change allows the community and myself to shape the browser’s future direction.
Waterfox Blog
Putting all that aside, Waterfox is a great option for those wanting Firefox with out-of-the-box privacy.
Waterfox website >>
Private browsers worth mentioning (but not necessarily recommended)
Here are a few private and secure browsers that didn’t make our recommended list but we think are still worth mentioning.
9. Bromite (Android)
Bromite is a Chromium-based browser for Android only (no desktop support). It comes with some great features by default, including ad blocking and various privacy enhancements.
Unfortunately, being a small project, Bromite suffers from infrequent updates. The last update was apparently in 2020!
Here are some highlights of this browser from the official Bromite website:
- The main goal is to provide a no-clutter browsing experience without privacy-invasive features and with the addition of a fast ad-blocking engine.
- Minimal UI changes are applied to help curbing the idea of “browser as an advertisement platform”.
- All patches are published under GNU/GPL v3 to enable other open source projects’ usage.
- Bromite is only available for Android Lollipop (v5.0, API level 21) and above.
Another cool feature I like with Bromite is that you can use custom ad block filters — learn more here. Bromite is under active development and remains a great browser for Android users.
https://www.bromite.org/
10. Pale Moon
Pale Moon is another open-source fork of Firefox, which aims for efficiency and customization. In testing out Pale Moon, it does offer different customization options, as well as support for older Firefox add-ons and its own lineup of add-ons. The design feels a bit dated, but it’s also not overly-cluttered and is lightweight and fast. Even more importantly, this secure browser is still being updated
Pale Moon is currently available on Windows and Linux, with other operating systems in development. Unlike other Firefox forks, Pale Moon runs on its own browser engine, Goanna, which is a fork of Gecko (used by Firefox). This is an older engine that was previously used by Firefox, but has long since been replaced. Many argue that this older codebase is a security vulnerability. And it’s also worth noting that the development team is very small compared to more popular browsers.
Pale Moon website >>
11. GNU IceCat
GNU IceCat is a fork of Firefox from the GNU free software project. IceCat is entirely “free software” as defined here and also includes various privacy add-ons and tweaks by default. Here are the privacy-protection features listed on the IceCat page:
- LibreJS
- HTTPS-Everywhere
- SpyBlock
- AboutIceCat
- Fingerprinting countermeasures
No updates – The big issue with GNU IceCat is that there do not appear to have been any updates since 2019. This can expose IceCat users to security vulnerabilities, which is why we are no longer recommending it.
GNU IceCat website >>
12. Iridium
Like Brave, Iridium is a secure browser that is based on Chromium and configured for more privacy by default. The following excerpt from Iridium’s website provides a good overview of this secure browser:
Iridium Browser is based on the Chromium code base. All modifications enhance the privacy of the user and make sure that the latest and best secure technologies are used. Automatic transmission of partial queries, keywords and metrics to central services is prevented and only occurs with the approval of the user. In addition, all our builds are reproducible and modifications are auditable, setting the project ahead of other secure browser providers.
Iridium is still being updated pretty frequently. However, it is not a widely-used browser, and there is no support for Android, iOS, or any other mobile devices.
Iridium browser website >>
Issues with other popular browsers
While some browsers claim to be secure against vulnerabilities, they might not be the best choice from a privacy perspective.
1. Google Chrome
Google Chrome is by far the most popular browser. Unfortunately, it’s a data collection tool as well and not a good choice for anyone looking for privacy.
You can safely assume that everything you do through Google Chrome is collected, saved to your data profile, and used for targeted advertising.
2. Microsoft Internet Explorer/Edge
Edge is a Microsoft product.
Just like with Windows, it’s a good idea to avoid Microsoft products, including the discontinued Internet Explorer and its replacement, called Edge. Both those browsers are closed-source, so there’s no telling what’s going on behind the scenes, and they’re also not the best for privacy reasons.
3. Opera browser
Opera started off as a decent browser, developed in Norway. However, in 2016 it was sold to a Chinese consortium for $600 million – and a lot has changed. The following information from Opera’s privacy policy explained how user data was collected and shared when you used Opera products. This was enough to turn us off to this browser:
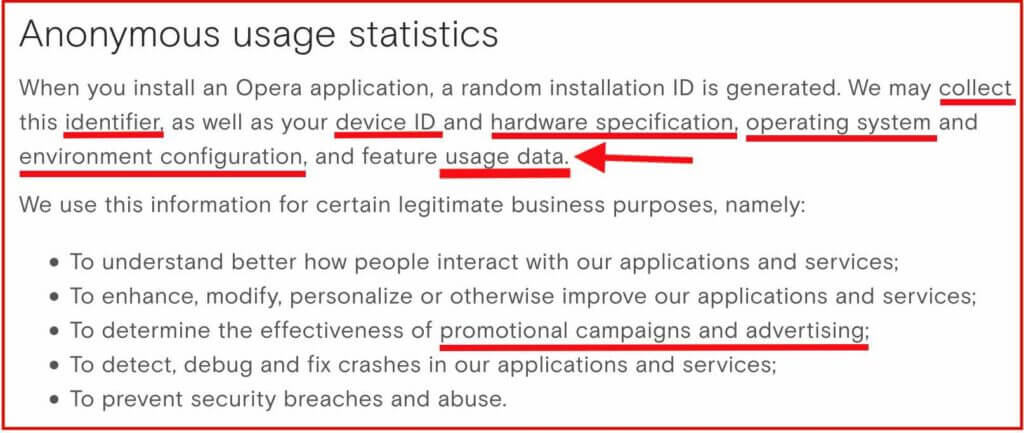
Opera also claims to offer a free VPN through the browser. However, as we covered in the Opera VPN review, it’s not really a VPN and does not offer full system-wide encryption. Additionally, your data is being collected when you use Opera browser and its “free VPN” feature.
4. Epic browser
Epic is a browser based on Chromium, created by “Hidden Reflex” which is based in India. Since 2014, Epic has been claiming they would open source the code, but it remains closed source today. What’s going on behind the scenes? How do they manage Chromium and remove invasive code? Who knows.
Just like with Opera VPN, Epic falsely claims to offer a “free VPN” through the browser, but this is not really true. The browser is merely routing traffic through a US proxy server. As we learned with Opera (and with many other “free proxy” services), proxies are often used for data collection (and they are often not secure). When reading the Epic privacy policy, we find that data from “video download and proxy services” is being collected.
One person who analyzed Epic found it to be connecting to Google on startup. This suggests that Epic is not, in fact, de-googled as it claims.
There are many better Chromium-based browsers to consider.
5. Safari browser
Safari is the default browser for macOS and iOS devices. Overall, Safari is not a horrible choice in terms of privacy and tracking protection – but it also cannot be recommended for a few reasons:
- Apple is a partner in the PRISM surveillance program
- Apple was caught “hoarding” Safari browsing history – even after it was deleted
- Apple was found to be collecting Safari history even when used in private mode
On a positive note, however, Apple does somewhat better with privacy than other large companies. The Safari browser blocks third-party cookies by default and also implements cross-site tracking protection.
6. Vivaldi browser
Vivaldi is a Chromium-based browser with source-code modifications that can be seen here. It is less popular than other browsers, with less active development than Firefox, for example.
Reading through their Privacy Policy, I did find some concerning information about data collection and the use of unique IDs:
When you install Vivaldi browser (“Vivaldi”), each installation profile is assigned a unique user ID that is stored on your computer. Vivaldi will send a message using HTTPS directly to our servers located in Iceland every 24 hours containing this ID, version, cpu architecture, screen resolution and time since last message. We anonymize the IP address of Vivaldi users by removing the last octet of the IP address from your Vivaldi client then we store the resolved approximate location after using a local geoip lookup. The purpose of this collection is to determine the total number of active users and their geographical distribution.
You can read more about Vivaldi here.
Secure and private browsers on mobile devices
Many of the recommended browsers above also offer versions for mobile users on iOS and Android.
With that being said, here are some good options for mobile users:
- Brave
- Bromite
- Firefox Focus
- DuckDuckGo
I also like using standard Firefox on mobile devices with customization and configurations for more privacy.
Browser privacy and compartmentalization
One problem that often comes with browser privacy and security is that people want to remain logged in to various accounts, while also browsing the web. But this is problematic. When you stay logged in to Gmail or Facebook, for example, their trackers can record your activity as you browse the web.
One potential solution to this problem is browser compartmentalization. This is when you use different web browsers for different online activities. For example:
- Browser #1 will only be used for accessing your online accounts that require a password. You can stay logged in with only this browser, and it won’t be used for general browsing.
- Browser #2 will only be used for web browsing, with various privacy configurations and no cookies or history being stored on the browser.
- Browser #3 could be completely locked down for maximum privacy and security.
You can also utilize different browsers, configured exactly the way you want, for various purposes, depending on your needs and threat model. The key is to keep the compartmentalization strict and not break the rules/uses for each browser.
Virtual machines – On the topic of compartmentalization, using virtual machines is also a good idea for both privacy and security. You can easily run Linux VMs through VirtualBox (FOSS) on your host computer.
Password managers – It should also be noted that storing your passwords in the browser may be risky depending on the browser you are using, especially since browsers may store passwords in cleartext. A better alternative would be to utilize a secure password manager. We have reviewed many popular options, including Bitwarden, Dashlane, LastPass, and more.
Browser add-ons for security and privacy
In addition to adjusting the settings within your browser, there are also a number of different add-ons or extensions you can install to improve your browser’s privacy and security.
Here are a few different options, but they may not all be supported by the browser you are using:
- uBlock Origin – This is one of the best browser-based ad blockers available that will also protect you against tracking.
- Cookie Autodelete – This will automatically delete cookies that are no longer needed from your browser.
- NoScript – NoScript allows you to customize exactly which scripts run on the websites you visit. Like uMatrix, this is for advanced users and requires lots of customization.
Warning: Be cautious about using third-party add-ons and browser extensions. There are many Chrome VPN extensions that are 100% free, but also very dangerous. Do your research first, since add-ons and extensions could function as spyware and data collection tools for third parties. This is especially true with free VPN services or browser proxy add-ons from questionable sources.
“Private” or “Incognito” browsing mode is NOT private (and why you need a VPN)
Many people falsely assume that using “private” or “incognito” mode in a browser actually provides some privacy. This is a false assumption.
Using “private” browsing mode only stops your browser from storing cookies, history, and passwords. But it doesn’t actually make you any more “private” to the outside world. Even when browsing in “private” or “incognito” mode, you are still exposed:
- Your internet provider can still see every site you visit. And note that internet providers are now forced to log web browsing activity of their customers and provide this data to authorities on request in many countries. In the United States, ISPs log everything and share the data with a huge network of third parties.
- Your real IP address and location remain exposed to all sites, ads, and trackers. This makes tracking and identification easy since your device has a unique IP address linked back to your identity through your internet service provider.
To easily solve these problems, we strongly recommend using a good VPN service. Using a VPN is simple. You just need to sign up for a VPN subscription, download the VPN app for your device, then connect to a VPN server and browse the web as normal. This offers many benefits:
- A VPN will securely encrypt your internet traffic, which prevents your ISP from seeing what you do online. (Your ISP will only see encrypted data, but not what you’re actually up to.)
- When you connect to a VPN server, the VPN server’s IP address and location will replace your real IP address and location. This allows you to appear to be anywhere in the world.
- A VPN will also allow you to access geo-restricted content, such as streaming Netflix with a VPN from anywhere in the world.
Below is a brief overview of our recommended VPNs. They have each come out on top in our testing for the respective VPN reviews.
- NordVPN: A fast, secure, audited VPN with advanced privacy features and a strict no-logs policy, based in Panama (with a 74% off coupon). See our NordVPN review here.
- Surfshark VPN: A no-logs VPN service with a large lineup of privacy and security features, based in The Netherlands. See the Surfshark VPN review.
- ExpressVPN – A fast, reliable, and secure VPN that also works well for streaming, but with above-average prices. See the ExpressVPN review for the pros and cons.
Short on money? There are also some good cheap VPNs that offer excellent features and performance, without breaking the bank. We also have detailed VPN comparisons. Our ExpressVPN vs NordVPN guide compares the top two providers.
Conclusion: Secure browsers and privacy in 2024
A well-configured secure browser is crucial for protecting your data if you want to browse the web with kind of privacy. But there are several good, secure browsers to choose from. So how do you do it?
Finding the best secure browser for you comes down to identifying the one that best fits your unique needs. Since this is a personal decision with subjective criteria, we can’t recommend a single option that is best for all use cases.
In truth, you need more than a secure browser that is configured to protect your privacy. To that browser you should add a quality VPN that will encrypt your traffic and hide your IP address.
You should also consider using a good ad blocker. Many ads include tracking code that companies can use to collect your browsing data and serve you targeted ads. If you aren’t blocking ads, your activities can be tracked by third-party advertising networks, which is not at all ideal.
Note: There are some VPNs that have built-in features to block ads and trackers. See our guide on VPN ad blocking for more info.
In terms of privacy, you may also want to protect yourself against browser or device fingerprinting and WebRTC browser leaks, which can expose your identity even when using a good VPN service.
This secure browser guide was last updated on May 15, 2024.

Metager is not longer free
“The reason is that Yahoo terminated our contracts unilaterally and without any notice on Monday. Upon request, we were merely informed that Yahoo would no longer be operating the business in Germany. …”
“…What happens now? MetaGer’s supporting association, SUMA-EV, will continue to exist. It will also still be possible to buy a key for the token-financed search and search with MetaGer. With this model, MetaGer will still be able to query paid search engines and deliver the results without tracking as usual. ….”
Starting at 5 Euros for 500 queries
https://suma-ev.de/en/eine-aera-geht-zu-ende/
{I still can’t get my head around the bit coin stuff!}
George f C your phrase is cherished by me, means as much to me, as any truth and honesty from another being in this life. So little times in life is it stressed to the importance of integrity and respect for those who are truthful and fair.
Is it because, crypto currency has been seen as the present symbol of deception and cunning to swindle people out of their hard-earned money?
There is an old film, encouraging individuals to prioritize fairness and honesty in their dealings with others. Delivers a crucial moral lesson: “You can’t cheat an honest man.” This phrase becomes a recurring theme throughout the movie.
https://en.m.wikipedia.org/wiki/The_Flim-Flam_Man
Honesty as heart felt gives me a sync portal towards karma to feel what I don’t understand yet.
Bump In The Road
HI George from Canada, a point of mine was answered and that answer shouldn’t be anyone’s accepted concept for todays techonlogy!
Since PC’s are less dominant now.
So it once may have been excepted as the core concept for any early forerunners of free or paid tech. When most everything like your add-on computer applications, either being a service or tool in nature started out free. To get your interest and grow in their product offerings, research and developments for its sustainability.
Sure you had the core tech in an OS acting as a bridge, facilitating connections between global brands, with retailers and customers.
That you paid to use this OS either buying a new computer or updating an OS as time passed.
So your answer (as a general) concept for my “Users-use at your own risk” point.
SAYING – “Brother… what else is new? One always does.”
See it’s the model or mode of the internet’s use that has changed. Shifting from the static PC-centric systems to the dynamic, mobile-friendly infrastructure it is today.
Today, many common applications have moved from acting as local clients on your computer or mobile device to running from the internet. This trend has so many advantages that it’s unlikely to slow down.
Or be offered as free tech again.
https://www.businessinsider.com/guides/tech/what-is-a-cloud-application
Your *users trust* is being traded for CONVENIENCE anymore. This has a consequence for old users having blindly trusted any software or service from a PAST history in their use of it.
People born after 2000, most likely were born into technologies grip and don’t understand the digital bucket they use. Especially from the ground up to restore the holes of privacy loss as pre-AI technology had opened up in their world.
So not knowing the emerging trend of having to “Verify before Trust” must be the users digital golden rule going forewards.
[https://bahaiteachings.org/human-brain-which-part-contains-conscience/]
I don’t see TECH – short for “technical,” referring to scientific and mathematical principles applied to practical problems. Working to aid users privacy, and now that AI is interacting at the center of devices using the internet. Can anyone see good things or just more flimflam to come lightening fast with AI at the core.
= ) this is for everyone’s benefit
This link says a lot, @Eddie Snowdon comment of an encapsulated view of our world of technology, business, cybercrime and world players.
https://cyberinsider.com/mastermind-behind-major-ransomware-operations-arrested-and-extradited/
Cloud computing has introduced virtualized persistent storage solutions, offering a range of benefits and characteristics that improve storage management, scalability, and resource utilization.
Cons of Virtualization:
– High Initial Investment: While virtualization reduces costs in the long run, the initial setup costs for storage and servers can be higher than a traditional setup.
– Complexity: Managing virtualized environments can be complex, especially as the number of VMs increases.
– Security Risks: Virtualization introduces additional layers, which may pose security risks if not properly configured and monitored.
– Learning New Infrastructure: As Organization shifted from Servers to Cloud. They required skilled staff who can work with cloud easily. Either they hire new IT staff with relevant skill or provide training on that skill which increase the cost of company.
– Data can be at Risk: Working on virtual instances on shared resources means that our data is hosted on third party resource which put’s our data in vulnerable condition. Any hacker can attack on our data or try to perform unauthorized access. Without Security solution our data is in threaten situation.
Summary,
Virtualization is an important technique in cloud computing that makes efficient use of physical resources by creating many virtual instances. It lowers costs, improves hardware utilization, provides high availability, simplifies disaster recovery, saves energy, and enables rapid setup and cloud migration. However, it involves significant initial expenses, complexity, and potential security threats. Despite these problems, the advantages of cost reductions, operational efficiency, and flexibility make virtualization crucial in modern cloud computing.
https://www.geeksforgeeks.org/virtualization-cloud-computing-types/#
https://www.geeksforgeeks.org/pros-and-cons-of-virtualization-in-cloud-computing/
[Only for compainies or a sm. business – not for their users]
Oh really !
I see this as another symbol of deception and cunning not only to the Virtual community concept, but everyday web use.
Howard Rheingold study, compared with Mark Granovetter’s ground-breaking “strength of weak ties” article published twenty years earlier in the American Journal of Sociology.
https://en.m.wikipedia.org/wiki/Virtual_community
The abstraction of physical storage from applications and mapping logical storage into physical storage.
Hyper-converged infrastructure (HCI): Combines compute, storage, and network resources into a single, virtualized platform, often used in cloud environments, or a creation of a separate computing environment within the same host.
Hosting data on third-party resources (has a grand attack surface) which can lead to putting the data at risk, it has the greater chance of getting attacked by any solo hacker or state actors very easily.
Shakespeare – Prince Hamlet – Act 3, Scene 1 (slightly altered):
To Chrome, or not to Chrome, that is the question!
My stab at humor aside, more basic to the question is “proprietary” versus “open source.”
proprietary: ‘used, made, or marketed by one having the exclusive legal right to’ – so ‘exclusion’ (as opposed to ‘inclusion’) is an integral part.
open source: ‘having the source code freely available for possible modification and redistribution’ but more generally ‘publicly available for use by the community at large’ -so ‘inclusion’ (as opposed to ‘exclusion’) is an integral part.
For further reading, a recommended thread I stumbled upon:
https://www.quora.com/What-is-a-proprietary-operating-system
A web search for proprietary web browsers versus open source browsers was also quite illuminating to me.
That’s why I have switched from MacOS to Linux; a brilliant alternative!!!
Firefox, and all its forks, suite my needs better, ergo, I favor them.
(Footnote: Some new FF based ones are maybe of interest to you: Floorp – from our Japanese brothers and sisters – https://floorp.app/en
and Zen Browser (scroll down for description on this page)
https://github.com/anfragment/zen
to mention just a couple.)
Cheers!
P.S. “A rational person can find peace by cultivating indifference to things outside of their control.” – Naval Ravikant
Thanks George from Canada, friend and brother … so which is better?
Maybe 1 update, or with a version change. Open Source offerings could derail to a proprietary based purpose.
A PC as hardware that are now being completely reimagined in entirety of the device as all smart-tech – from its silicon to the operating system, the application layer to the cloud – with AI at the center.
If AI is at the center what does that do to our understanding of “proprietary” versus “open source” for all smart-tech devices?
Just forging a trip to a software developers TOS and PP pages, we are left imaged to the understanding of the ground up view. Ex: take a tree, trunk the main software package – limbs and branches where our privacy is shared.
Below ground view will be the foundational roots where your privacy is lost. . .through, partnerships and other sub-companies needed to support the trunk, guised in the legalise there.
P.S.
If one considers the source of indifference in a rational sense, peace is cultivated at their control, for little expence.
Somehow and strangely, the quote didn’t make it to the original.
“To Chrome, or not to Chrome, that is the question!”
Oh, another point about proprietary versus open source. Either route of many eyes or a select few eyes on the code. Paid or free every bit of it is Users – use at your own risk!
Digitial data, electrical, cell, bluetooth, wi-fi, from any smartDevice connecting to the internet is a risk to you, thats neither good for your privacy, security, assets. You will not find anybody claiming your 100% safe from any link of a site, given theirs or your hardware, firmware, software, in a connection made.
A closed lock or unbroken key icon in the browser, should insure a secure connection between the browser and server. But how dependent is this connections requirement to your software and browsers being up-to-date with the latest security patches?
To @ BITR
Wow! Well… what you write is 1) conceptually quite challenging to me as I have a pretty limited intellectual bandwidth, and 2) your scope of technical understanding on this subject is a light-year ahead of mine! {I still can’t get my head around the bit coin stuff!}
However, and I could be completely off the mark on this, the main points you are making appear to be philosophically speculative and laced with an undercurrent of suspicion. Yes/no/maybe? Am I misinterpreting?
Could some open source project turn proprietary? Sure it could. Will it? Hopefully not. Will an AI be used for nefarious purposes? Good chance; in some quarters. Can one step outside of the lighting fast onslaught of technical developments? Not if you want to stay “plugged in”! {Some try by going off-grid or super simplifying their lifestyle or becoming neo-luddites.}
https://en.wikipedia.org/wiki/Neo-Luddism
IMO, anything that Mankind has invented, or will invent, can be used well or poorly. (Our collective history is soaked with examples.) When greed, malice, selfishness, corruption, baseless entitlement, mindless consumerism, perversion, fear (etc., etc., etc.) rule the day… we are done for. Dystopian future? Could happen. One hopes not.
But you had also brought up the point of “use at your own risk”. Brother… what else is new? One always does. I think the key difference is whether one is aware of risk and goes at it with a view of an optimistic outcome, or, withdraws from risk and folds like a cheap suit.
Anyway…’nough said… just my 2 cents worth… and it’s Miller time!!! 😉
Hi George from Canada.
Sir, please don’t think of me as anything but a thinker, a good friend and brother here. With a hands-on (practical) appliction in the construction field, enough so, to problem solve and troubleshoot my immediate constituents.
If a lable is needed, choose one that – I do relate to something (such as a news story or a series of real events). As likened to a parable in providing an instructive example or lesson to the great corrupting effect of massive tech deployments in our very life.
My tech know-how would fill a sewing thimble maybe 1 and 1/2 times. If I may be clear, in the 70’s, I help run one of the few computers in the military communication system. It being the 70/45 UniVac processer with two 1600 IBM terminals and 64K words memory only, a bank of 7 and 9 track magnetic tape drives, 3 printers, card punch and interpreter, multiple vdt monitors, storage in MSU and disk drives, and I was responsible on mids watches to change out the crytpo cards.
Simular to this image https://upload.wikimedia.org/wikipedia/commons/thumb/1/16/UNIVAC-FILE-COMPUTER-BRL61-0944.jpg/640px-UNIVAC-FILE-COMPUTER-BRL61-0944.jpg
Who’d of thought, something that spread-out one day would fit in your pocket. My later house of 35 years as my home, only had 1,040 sq.ft. to it, and was close to the univac’s layout size needed.
Your #’ed points of 1 & 2 have us both tied to the same set of tracks on a dark night, trying to judge our time left by the exact distance of the trains light.
Point being, we (us all) stand to be ran over and overran by AI. Beings todays business attitude of any tech or internet business, as the current trend of compaines choosing Business Over Security Practices. Suck (slang) in their lead for any moral judgments relating to their customers data today.
Your a good thinker too my friend ! So a useful aid to myself, is to think of things I’ve known with things I have nothing known of, as the inter-connected circle symbols. As imaged in the Olympic flag, if you look close everywhere a circle crosses another circle is a bridge, doorway, path to that understanding you own – – apply that knowledge to your unknown circle’s subjects via the intersections of overlap…ing facts.
If subjects are unknown, that by forming a question puts your thoughts into an order. An order of logic, that given to the reversed/expaneded, etc use of mind views, leads to finding the correct answers you’ve sought.
Sorry folks this ran long ya-all, we need a forum here at RP.
It’s not like the people that want to be plugged-In have many options, even to a say in where the technology they need to use is going.
Remember the technology fazes of internet progression? Now we go through device tech progression.
The titans plan in putting AI at the center is for more revenue streams by every smart-tech device.
See the simular topic link replies at
https://restoreprivacy.com/privacy-tools/#comments
and any comments links.
Where Mike and I spoke some mid Aug.
Sounds like we lost our privacy, freedom to chose, and now or at some point have to subscribe to use the expensive tech we own of preferred brands for driving AI adaptation.
Hello, George from Canada, Hard Sell here.
Remember me? You asked me once to not leave long comments… Man has the world ever changed since then! (GenAI) evolved or is trying too.
George I do appreciate your words.
THIS IS A REPOST; of the same matter where people come to RP and flame on other people’s comments here!
[ Alex Lekander August 2, 2024
Ah come on guys, can’t we all get along and play nice? ]
— Comments should be for questions and answers, otherwise to give help or useful words in your actions of noticing or perceiving something posted.
RP will not post comments for someone who is deliberately inflammatory to another commenter or staff here.
That last part, Alex might add to the ‘Leave a Reply’ instructions. To ensure RP comments alway adds some value and insight here.
If not, any comments should be of a annotator commenter’s style, such as,
fact checking, researching, adding links and seeking additional answers in helping, or explanations in the (birds-eye) view to help someone understand Alex’s topic better.
(-1st everybody’s post being shown are fair thoughts from those perspectives you’ve expressed.
-2nd everybody’s mind is an island having needs and wants from their experiences of life, gaining insight, trust and wisdom that supports your own unique perspective.)
Glad you here still George from Canada ! ! !
https://biblehub.com/matthew/7-2.htm
to @= ) friend!
That’s pretty classy… to give me shit by quoting Scripture!!! Nicely done!!! 🙂
It was my open hand of friendship as well to aid the meaning of your prior words, not a bash…!
People will read into it…what they want to see, by how they see things and their decision how they feel about it.
Same as they hold up a mirror to see the world – but it’s their own faces that tend to get in the way.
HELPFUL Comments are always welcome, as they can be like cog teeth of a wheel transmitting successive positive motive from a broader perspective as each thought vibrates the international scene known as us humans.
Peace
George with my best intensions please accept these joyful sounds as a peace offering. My hand is out as I feel you are a friend and brother on RP. Everyone here should be friends and if not brothers and sisters, as Alex wishes in his efforts of RP. [Alex, please allow the off topic links – thank you = )]
https://m.youtube.com/watch?v=4mfbM_w6pPM
https://m.youtube.com/watch?v=0ew5ENu-FJI
https://m.youtube.com/watch?v=Mlz2YjM4Ii0
https://m.youtube.com/watch?v=PPsevhQkn68
https://m.youtube.com/watch?v=K1LABvPI6aU
Peace @Hard Sell. I hear you brother!!! Decency always floats to the top!!! 🙂
i cant believe that brave is being touted as the best privacy focused browser.
my personal experience shows that it is great for projecting an illusion of privacy, whilst doing much to invade privacy.
its the wosrts kind of “privacy” browser.
@Dide mann Why do you think Brave is the worst? I’ve used Brave for years and I think it works great. What do you suggest as an alternative? If you don’t like Brave then there’s always Mullvad’s, Firefox or LibreWolf.
@Mike, Why do you suffer from survivorship bias? I agree Brave being promoted as the best privacy browser is ridiculous (unhinged). Any browser that promotes cypto can’t be good. And that’s really the point. Only a modified FF browser or Torbrowser can be said to be best privacy browsers (none of which are Chromium based).
It’s difficult to consider your comment seriously if you don’t say what your “personal experience” of Brave shows; “projecting an illusion of privacy”?… “doing much to invade privacy”?… “the wosrts [sic] kind of “privacy” browser”? Please explain.
to @ Bobuntu and @Mike and others:
@Dide Man is , IMO, simply trolling; defined as “the act of leaving an insulting message on the internet in order to annoy someone.” Further reading – https://en.wikipedia.org/wiki/Troll_(slang)
Along with the other folks that pop up on this and other forums with comments like “Brave is just garbage,” “how could you people (fill in the blank),” and all the other useless, snide, meaningless opinions/comments they dish out; cloaked in anonymity and operating like spitting cobras in the dark, spraying their venom in all directions.
I don’t see any intent from these people to learn, educate or inform… just to stir up chaos devoid of reasoning.
Hello
I have been all that concerns brave for 3 or 4 years.
My conclusion (but it only engages me): do not use it
Sorry its in French (but you can translate)
https://forum.malekal.com/viewtopic.php?p=549470
Hi RP community
I’ve found an add-on for Firefox called JShelter.
Installing it to FF shows ‘your browser fingerprints are randomised’ when testing with ‘Cover your tracks’ site.
Just like Brave browser!
Is this result true, or some tricks of that add-on for CYT site to generate such result?
If it is truly randomise FF’s fingerprints then this is very good news for users who avoid chromium based browser and can get Brave’s randomised fingerprints with additional specialities of FF.
What are your views?
Never heard of it. How does it do against fingerprint.com?
well I’ve tried with that testing site, but found I’m not capable enough to interpret and make a conclusion from the technical data showing there.
If you please share your your opinion, we’ll be benefited.
This is the add-on link-
https://addons.mozilla.org/en-US/android/addon/javascript-restrictor/
Do you really prefer Brave over Vivaldi ??
That’s a joke and it must be clear if you spent more time digging deeper into both browsers.
@Martin I prefer Brave because it’s primary focus is privacy, as opposed to Vivaldi that is focused more on power users. That doesn’t mean Vivaldi is bad. I became familiar with and learned to appreciate Vivaldi after having read this Cloudwards review and it is rated as one of their top browsers.
https://www.cloudwards.net/vivaldi-review/
I have praised Vivaldi many times and like a lot of it’s features (like its ad-blocker). I also think that it deserves a lot more respect or recognition in the privacy community too. The host of TechLore (Henry) has expressed a similar sentiment in which he even interviewed Vivaldi tech’s CEO last year (link below):
https://youtu.be/TvIKMl1Ldi0?si=okjwlV1uF6v7pH5r
But for my personal preference, I like Brave. If you enjoy Vivaldi, more power to you! At least you’re not using Chrome. Good luck!
Alex, I hope you and yours are safe and well.
With yearly Wildfires, bound to happen in many places in the United States, especially during droughts, but are most common in the Western United States and Florida regions.
My good wishes extend to your readers in the US as well, to their air quality and Health.
https://fire.airnow.gov/
The EPA and USFS have developed the AirNow Fire and Smoke Map to provide information on current fire and smoke conditions.
Hi BITR, yep, here in the northwest we already have wildfire smoke hazing up the skies. Fortunately it has not gotten too bad yet in my area and we can still enjoy the outdoors and summer without getting smoked out. Thanks for that map, it’s very useful this time of year! 😎
= ) my friend!
I’d stay away from Brave…
https://support.brave.com/hc/en-us/articles/360051406452-How-does-IPFS-Impact-my-Privacy
What do you use or suggest? Is there a safe browser that is light, fast, and only needs minimal tweaking?
Been using Brave browser now for about a year and it just keeps getting crappier as time goes on. What happened to the good old days when Firefox was a really good browser. All browser nowadays are garbage!
As technology continues to advance, web browsers will evolve to meet the changing needs of users and the web ecosystem.
How the web works
[https://developer.mozilla.org/en-US/docs/Learn/Getting_started_with_the_web/How_the_Web_works]
Yes, understanding these-
[https://www.youtube.com/watch?v=7_LPdttKXPc]
And
[https://www.youtube.com/watch?v=x3c1ih2NJEg]
Will it answer your question “What happened to the good old days when Firefox was a really good browser?”
WebAssembly is named to evoke the concept of assembly language, a term which dates to the 1950s. The name suggests bringing assembly-like programming to the Web, where it will be executed client-side — by the website-user’s computer via the user’s web browser.
All major browsers allow WebAssembly if Content-Security-Policy is not specified, or if “unsafe-eval” is used, but otherwise they behave differently. Chrome requires “unsafe-eval”, though a worker thread can be a workaround.
[https://en.m.wikipedia.org/wiki/WebAssembly]
Qutebrowser and luakit are good still.
When Brave, Vivaldi or Firefox download from FF-updater, these apps shows their own signing as revealed if scanned with ‘App Manager’.
But when these browsers downloaded from Play store, they shows ‘Play App signing’.
And ‘App Manager’ shows a message – “This app contains certain markers that indicate that it might be using Play App Signing. With this scheme, the signing keys are stored in Google’s servers, and Google is responsible for signing the app. Note that matching signing information is the only way to verify that the app has not been modified by any person other than the developer (and in this case, Google too).”
My quarry is, is ‘Play App signing’ acceptable or concerning for privacy?
Should we use these browsers from FF-updater where they are downloaded from the dev’s sites directly?
Android allows app install (APK) from Google Play Store, alternative store or directly from web.
Play Store sign means Google verified its legitimacy, dev sign means the dev itself verified its legitimacy. Either way is fine, the general public should just use Play Store to avoid malware or fake apps.
“Either way is fine, the general public should just use Play Store to avoid malware or fake apps.”
Apps in the Google Play Store can still be infested with malware and trackers. It is no safe bet just because they are in the store.
It’s safer at least. Play Store runs a safety check called Play Protect by default..
Critical and sensitive apps like banking or government services should only be downloaded from Play Store.
Yes sir, logical.
And what about the chances of ‘modifications’ applied by Google over dev’s built to fulfill their tracking?
This is my main concern.
@shr
No, I don’t think Google will do that.
Alex, wouldn’t the safest bet be downloading the ‘apk’ and then scanning it with 70+ antivirus products, 10+ dynamic analysis sandboxes and a myriad of other security tools to produce a threat score and relevant context to understand it.
VirusTotal inspects items with over 70 antivirus scanners and URL/domain blocklisting services, in addition to a myriad of tools to extract signals from the studied content. Any user can select a file from their computer using their browser and send it to VirusTotal.
VirusTotal offers a number of file submission methods, including the primary public web interface, desktop uploaders, browser extensions and a programmatic API. The web interface has the highest scanning priority among the publicly available submission methods.
[https://www.virustotal.com/gui/home/upload]
Yes, agreed if you can get the APK from a reliable source, but that can also be problematic. People searching for APK files often end up on sketchy APK download sites and end up downloading dangerous/malicious files along with the APK.
What is the point of keeping silent about the existence, for example, of such a browser and talking about those that are practically impossible to trust? https://f-droid.org/en/packages/com.stoutner.privacybrowser.standard/
@raps
The dev and app is undoubtedly trustworthy.
The problem is this browser built on android webview, which leaks every private data to Google.
Yes with webview dev tools provided with browser can be hardened for privacy little, but this is not enough.
Dev promised to implement privacy webview from version 4, long time before but no update yet.
Many sites simply don’t recognize webview browser and don’t open.
Here more explanation https://divestos.org/pages/browsers
Might look at [https://www.theverge.com/2021/6/30/22557390/google-apk-app-bundles-package-format-play-store]
Most Android implementations allow users to manually install APK files. But, only after they turn on an “Unknown Sources” setting that allows installation from sources other than trusted ones like Google Play.
shr, your concern of this-
“This app contains certain markers that indicate that it might be using Play App Signing. With this scheme, the signing keys are stored in Google’s servers, and Google is responsible for signing the app. Note that matching signing information is the only way to verify that the app has not been modified by any person other than the developer (and in this case, Google too).”
specifically,-
“that matching signing information is the only way to verify that the app has not been modified”.
*** A more popular approach is to generate a hash of the copied file and comparing that to the hash of the original file. [https://en.m.wikipedia.org/wiki/File_verification]
To search for a file that has a given md5, sha1 or sha256 just type in the hash under consideration in the main search box. [https://www.virustotal.com/gui/home/upload]
The problem mitigates a little if you have root rights and an afwall app. For example, Internet access has only VPN, and a few of the applications you need, have access to the Internet only through VPN. It is even better if you have a de-Gugoled android or disable the garbage apk in the system. My scenario is that only VPN has access to the Internet, and two browsers and messenger have access to the network only through VPN, the rest of my applications do not require access to the network. The rest of the system almost “sleeps” and hardly knows that the device has Internet access. Almost, because If you seriously consider such a scenario, it is still far from ideal, there are many questions, leaks both software and hardware. But this is a very good setting, which even extends the battery life, because. In fact, only a dozen applications work at the same time and not 400 pieces built into the system from the store. You can always go further by removing cameras, microphones, sensors, etc. etc. And don’t use Android at all. The above settings are quite flexible and allow you to use all the Android functionality easily, including or disabling what you need. It is worth noting that in some cases, you will need to allow access to the VPN network for the download application built into the Android application, because. Some applications use it, for example, to download offline maps by navigator, after downloading, we can cancel access to the network. With AFWALL, we can also use a minimally configured device, most of the system will still not know about the existence of access to the Internet, but it is still better to ban some aggressive applications from changing the network settings on your own.
What sound experience! raps
You’ve just described dumbing down a smart phone for users privacy. In essence a flip phone.
Save the aggravation, money and buy and use flip-phones.
Flip phones, by design, are not constantly connected to the internet, reducing the opportunity for data breaches and tracking.
Flip phones do not collect user information, as they are not designed to interact with the internet or access online services.
What location tracking through the cell tower(s) triangulation, reguarding flip phones information is typically not sold or shared with third parties. Flip phones typically run on simple, proprietary operating systems that are not designed to collect user data.
Flip phones offer more privacy than smartphones due to their limited connectivity, lack of data collection, and simple operating systems.
Whereas smartphones offer a wide range of apps that can compromise user privacy. Even with privacy-focused alternatives like LineageOS and XPrivacy, smartphones still present a higher risk of data exposure due to the sheer number of apps and services they support.
Ground your use of moble data networks and use only land cables for you internet useage needs.
Is unplugging the biggest leak!
What about Arcsearch?
https://apps.apple.com/app/id6472513080
I know that Arc uses OpenAI so I suspect the search engine probably comes from Bing or Google.