
A new ransomware as a service (RaaS) operation named ‘GhostLocker’ was launched earlier this month, calling affiliates to join.
The new operation was announced by GhostSec, a hacktivist group and, member of the ‘Five Families’ collective, which also comprises SiegedSec and Stormous.
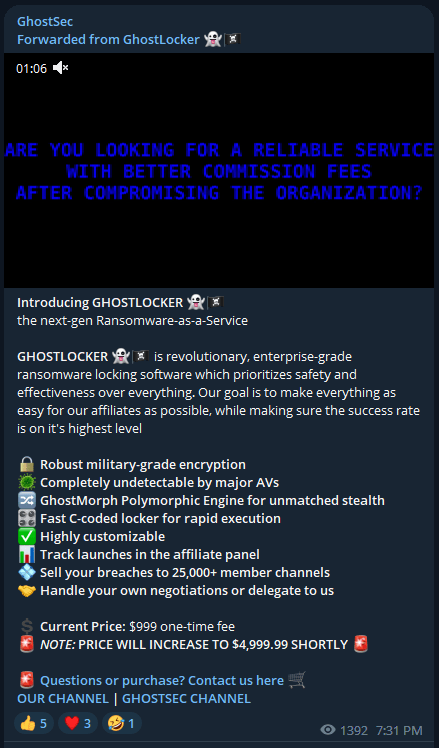
The statement released on Telegram touts military-grade encryption, completely undetectable payloads, and centralized negotiation managed by the primary RaaS operators, who claim to be “professionals” in the field. Affiliates are only required to execute the breach and are assured 15% of the proceeds. The project also offers an insightful web panel for affiliates, giving them an overview of their operational success, a sneak peek into the negotiations with the ability for intervention, and more.
For starters, GhostLocker v0.1 was opened to only 15 affiliates, who are requested to pay $999 to join. The RaaS operators claimed that this price would be later increased to $4,999, an entrance fee to filter out less capable/serious affiliates.
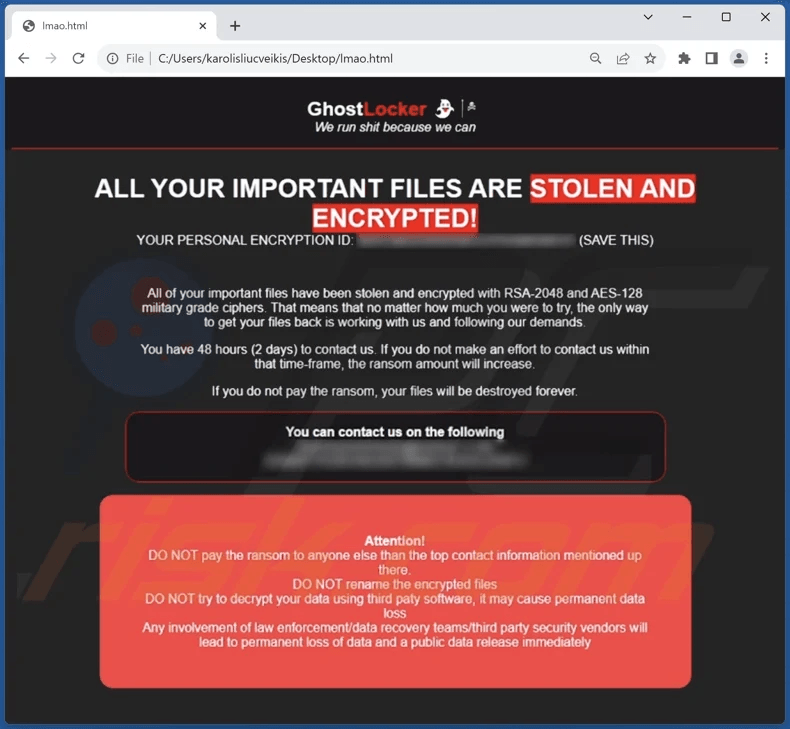
No cybersecurity firms have yet dissected GhostLocker, so the claims about encryption strength and the lightness of the binaries haven’t been independently confirmed. A ransom note sample shared by a restoration service claims that the encryption is based on RSA-2048 and AES-128 ciphers, theoretically unbreakable, while victims are given 48 hours to respond to the threat actors’ demands.
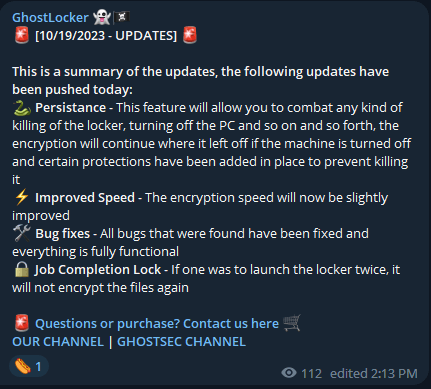
Today, the authors of GhostLocker released the first major update for the strain, adding a persistence mechanism for the locker that prevents victims or security tools from killing its process, improving the encryption speed, and adding a safeguard to avoid redundant encryption jobs. This reduces the chances of this being a publicity stunt, and the project will likely enjoy continuous development.
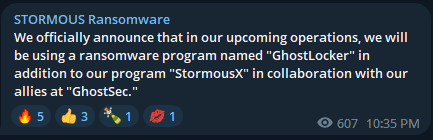
Already, the Stormous ransomware group, which made unverified claims of hacking NVIDIA and stealing customer data and source code last year, have announced on their Telegram channel that they will be using GhostLocker alongside their own program, “StormousX.”
Double-edged knife
Incorporating ransomware into a hacktivist’s arsenal can magnify their message and bolster their financial standing. Employing ransomware to target organizations that oppose their core beliefs offers a more impactful approach than executing DDoS attacks, and it provides a lucrative financial incentive.
However, ransomware blurs the line between hacktivism and common cybercrime, threatening to hurt the credibility and reputation of these groups that claim to have a higher moral group. If their actions are driven by profit as much as principle, their message can be diluted or even wholly disregarded.
A recent report by KELA on how hacktivist groups fund their operations shed more light on the subject, involving common cybercrime tactics like data and malware sales, demanding ransom from breached organizations, selling hack guides, renting their DDoS botnet firepower, and offering hack-for-hire services.

 Users of Multiple VPNs Targeted by BbyStealer Malware Campaign
Users of Multiple VPNs Targeted by BbyStealer Malware Campaign
Nice and good research. Could you send me the sample for Malware Analysis?