
As the use of cloud services and containers continues to grow, threat actors have started recognizing them as a new attack surface. Since cloud resources come with inherent scalability and complexity, for threat actors, it is a unique opportunity to launch sophisticated attacks.
Recent research by Sysdig has uncovered a cloud-native crypto jacking operation, which the researchers have named AMBERSQUID. Interestingly, the operation targets the AWS services, typically considered secure, such as the AWS Fargate and Amazon SageMaker. Since these services are not commonly used, they often remain overlooked from the security perspective.
Moreover, the AMBERSQUID attack is stealthy and could exploit the cloud services without triggering the AWS requirements needed to approve more resources. This typically happens if the threat actors only spammed any other service, such as the EC2.
Since the attack remains unidentified until the containers run in production, the research uncovers the vulnerabilities within the system. Also, it highlights the importance of implementing end-to-end security instead of only opting for preventive security measures. The hidden nature of AMBERSQUID can cost the victims up to $10,000/day, causing a significant strain on an organization’s financial stature.
According the the report, the attack uses Indonesian languages and usernames in the script and the researchers attribute the AMBERSQUID to Indonesian hackers who also often conduct freejacking and crypto-jacking attacks as a source of income.
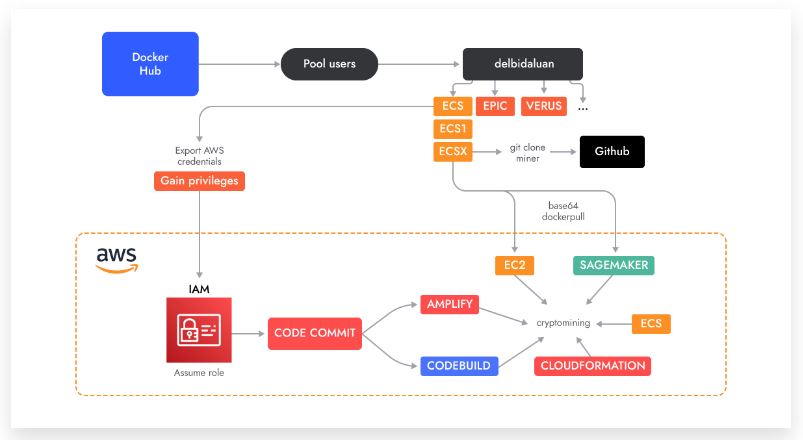
What is the AMBERSQUID? Technical details and challenges.
Sysdig researchers first discovered the AMBERSQUID after analyzing over 1.7M Linux images, helping them understand the kind of malicious payloads hidden within the container images on Docker Hub. These dangerous container images were stealthy and didn’t raise any alarms due to the statistics scanning for known indicators or malicious binaries.
Only after the container was run did its cross-service activities become apparent to the team. The original container that initiated the research for the cryptojacking scheme was found on Docker Hub, but the scope of the attack expanded across several accounts, most of which started with very basic container images running a crypto miner and then later switched over to AWS- services.
An Insight to the Operation
The operation first started at Docker Hub in May 2022. It developed through August, after which the threat actors continued to push crypt minor images through different accounts until they created their own GitHub account in March 2023. The threat actors downloaded minors from popular Github repositories to make their attack more stealthy and imported them into layers of Docker images. The repositories did not have a source code but did have inside downloadable archives called “test” packed with UPX and malformed so that they couldn’t be quickly unpacked.
The researchers also discovered the GitHub account that the attacker was using to store Amplify application source code and the mining scripts under different versions of code to prevent being tracked by the GitHub search engine, such as:
- toolbar repository, release 2.0.0 used by delbidaluan/tidex
- romy repository, release 2.0.0 used by delbidaluan/ecsx and delbidaluan/cpoolx
- profile repository, release 1.0.0 used by delbidaluan/epicx, delbidaluan/zephx and delbidaluan/abipdnx
Before creating these GitHub accounts, the attackers had created crypto miner binaries without any obfuscation.
The Sysdig research team told RestorePrivacy that they finalized the images ending with “x,” precisely the epic idea with over 100K downloads. Here are all the AWS services that the attack targeted in various ways:
- AWS Artifacts
- Code Commit
- Amplify
- Elastic Container Service (ECS)/Fargate
- Codebuild Scripts
- CloudFormation
- EC2 Auto Scaling
- Sagemaker
The threat actors have brought these services together to form the attack. With this, they were able to bypass Amazon’s security barriers and remain hidden. For each platform, the threat actors made sure to delete the CodeCommit repository by running the delete. sh. script. This helped ensure that the attack remained hidden.
Exploring the impact on the victims
The AMBERSQUID attack is stealthy and can cost up to $10,000/day for the victims. Now, assuming that the default scripts do not operate at full power and only affect a few regions of the AWS services, each service could potentially cost the victim more than $300/day, totaling up to $2244. Moreover, recovery from such an attack would also cost a significant amount of money since the attack targets multiple services. Therefore, having an effective incident response plan that would involve finding and killing all the minors in the exploited service. Such a plan is costly and can significantly dent the financial structure of the victim.
The cryptocurrency wallets used in the whole attack are Monero, Bamboo, QRL, Zephyr, Verus and Tidecoin.
Possible security measures to consider- Final Words
With cloud services, there is bound to be a rise in cloud security issues. Especially as most organizations overlook cloud services while implementing defense strategies. Moreover, with cloud attacks being stealthy, they have the potential to wreak havoc, like in the case of AMBERSQUID.
The main component of these attacks that makes them so deadly in nature is that they are even undetected by VirusTotal. The head of research, Alessandro Brucato, told RestorePrivacy that the best way out is to ensure end-to-end security. As per the findings of the Sysdig 2023 Cloud Threat Report, 10% of images remain undetected by static scanning alone.
Since there is no sure way to detect whether you are a victim of the attack, it is essential to look at the usability perspective. Users need to monitor how much of the tool is being used closely. If there is excessive use of the service, then there is a chance of a cryptojacking operation underway.
It is crucial to have an effective defense strategy and take preventive measures. One such security measure is limiting access to the service and monitoring the use of these services. Apart from that, it is also essential to have good inventories to ensure everything is going smoothly within a system. Another crucial thing to consider is building an effective incident response plan. This would allow the organization to take immediate action against such attacks and prevent significant monetary losses.

 State Spyware Extensively Using Ads as Distribution Channel
State Spyware Extensively Using Ads as Distribution Channel
Leave a Reply