
Researchers from the Max Planck Institute for Informatics conducted a study analyzing VPN traffic to evaluate the overall security of the VPN ecosystem.
The resulting technical paper raises serious concerns, especially for the SSTP and OpenVPN protocols, like the presence of many VPN servers vulnerable to known cryptographic flaws, such as the ROBOT attack.
Scanning VPNs
The challenges of detecting VPN traffic in the wild are far too substantial for WireGuard and AnyConnect protocols, so the scientists focused on IPsec/L2TP, OpenVPN, SSTP, and PPTP.
By conducting internet-wide searches involving connection requests (probes) on a range of 530 million IPv6 addresses and the entire IPv4 address range, the team found 9,817,450 responses that can be identified as VPN servers.
Arxiv.org
Roughly seven million of the VPN servers detected to use the IPsec protocol, 2.4 million use PPTP, 1.4 million rely on OpenVPN, and just 187k use SSTP.
Out of the 1.4 million OpenVPN servers, about 70% were detected over UDP, and 30% were using TCP, which is considered a fallback option.
Security Findings
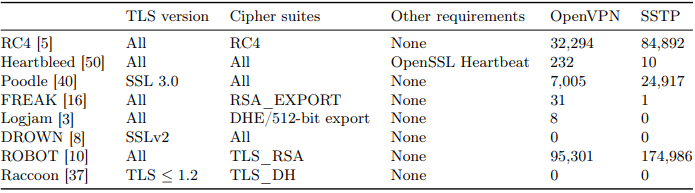
The paper claims that roughly 90% of the SSTP detections are vulnerable to ROBOT (Return of Bleichenbacher’s Oracle Threat) attacks. This cryptographic attack exploits a weakness in the RSA encryption standard.
This would allow an attacker to decrypt the content of TLS traffic by sending specially crafted requests to the target server. For this reason, the paper suggests avoiding SSTP altogether, as it’s based on an outdated version of SSL.
For OpenVPN, the team found 32,294 servers vulnerable to RC4 attacks, 232 servers vulnerable to Heartbleed, 7,005 servers vulnerable to Poodle, 31 vulnerable to FREAK, eight vulnerable to Logjam, and 95,301 vulnerable to ROBOT.
Arxiv.org
This means that 134,891 OpenVPN servers are vulnerable to dangerous attacks, or about 9.64% of those detected using the particular protocol.
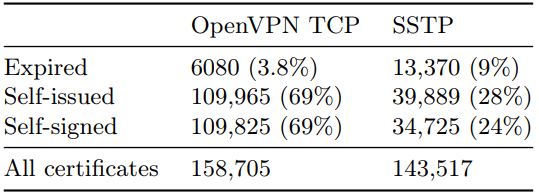
In addition to the mentioned flaws, the researchers found that many VPN servers use self-issued and self-signed certificates, with around 4.7% of them being “snake oil” TLS certificates, which means they’re invalid and have no real practical purpose.
It should also be noted that a significant percentage of OpenVPN servers (3.8%) and SSTP servers (9%) were using expired certificates, potentially allowing attackers to intercept and manipulate the communication between clients and servers.
Arxiv.org
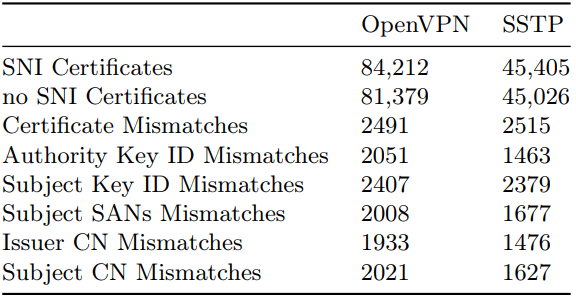
Finally, the study found that many VPN servers did not provide an SNI extension in their TLS handshake, which makes it difficult for clients to verify the server’s identity, opening up the way to server spoofing and exposing man-in-the-middle attacks.
Arxiv.org
Although the study was subject to practical limitations, it has proven that SSTP is highly insecure and OpenVPN can be very risky in the current landscape. There’s still much work to be done for some VPN products to fulfill their marketing promises. One of the latest developments in the VPN protocol landscape is WireGuard, which offers upgraded security and better performance over legacy protocols.
For more details on all security/privacy findings and the VPN hitlist with the probe-generating modules that can be used to reproduce the results, check out the technical paper on Arxiv.org.

 Redirect Campaign Infects Almost 11,000 Sites with Malware
Redirect Campaign Infects Almost 11,000 Sites with Malware
Can you guys review Mullvad VPN if it isn’t already on the list of VPNs to review/isn’t already being reviewed? Thanks so much for your work Sven and Heinrich!
So this means Open VPN protocol became vulnerable to attacks or the way it’s applied by the VPN companies is compromised? It’s always been touted as “the gold standard”, before Wireguard.
Hi @Bronco, a great question! I was going to see if I could have a look into the paper and then noted Heinrich described it as a technical paper but still though I could look at the conclusion. I didn’t search with enthusiasm because I wasn’t sure I would be able to comprehend it.
I did find this link:
https://www.mpi-inf.mpg.de/departments/inet/research/vpn
And if that link refers to the paper Heinrich refers to it would give a little insight to your question. My reading is that the researchers were testing for “vulnerabilities” and I take that to mean ‘known vulnerabilities’.
Also, Sven states lower that ~none of RP recommended VPNs were listed in the report.
So I infer that it is not the protocol but the implementation that has been called out here;
Still, the paper would not imply that the RP recommended VPNs are not vulnerable to the attacks that were tested, as the methodology states that it was a two step approach where the researchers first sort to identify the servers then to test against that set of identified servers, so if the servers weren’t identified they wouldn’t have been tested.
Great question – that is my inference.
GL,
it’s not the protocol that’s vulnerable but the implementation used by the VPN provider. Per the article:
” 1.4 million rely on OpenVPN …. ”
“This means that 134,891 OpenVPN servers are vulnerable to dangerous attacks, or about 9.64% of those detected using the particular protocol”
If it were an inherent flaw with the protocol, then all 1.4 million cited in the study would be affected instead of 9.64%
Heinrich,
Interesting article. Restoreprivacy.com has been my go to for privacy matters for many years.
This article is another example of getting info that others aren’t offering. Great job.
As this site reviews and recommends many security related products/services, does this report impact any of those previously reviewed products? Example: Express VPN.
Again, Thx for keeping us informed.
ExpressVPN and our other top recommendations were not identified for security issues in the paper, so no major changes at this time with the recommendations.
Hi Sven,
Do any of the RP recommended VPNs use these these potentially vulnerable protocols?
Regards,
Well most VPNs still offer OpenVPN, but it is being eclipsed by WireGuard as the protocol of choice.
Hello, could you please discuss the topic of security and privacy when using ChatGPT? Thank you.
Hi Liu XIngshen, the ChatGPT privacy is very readable and is here:
https://openai.com/privacy/
If have been reading here at RP and enjoy the articles you will find the above straight forward.
If you have questions about it you can post them in the chat and someone may answer them.
ChatGTP requires a phone number to sign up, so if you provide your real one they will have your real identity.
If you are really privacy concerned I would use similar techniques suggested in the RP guide on fingerprinting:
https://restoreprivacy.com/browser-fingerprinting/
And after reading the policy and understanding a little at a high level of how powerful the technology is, I would.
Also, having used the service briefly, it is very powerful, it learns from your previous inquiries and is really powerful at guessing answers you want in subsequent inquiries,
And Microsoft just tipped in 10 billion:
https://www.bbc.com/news/technology-64374283
GL,
Currently, there are no options to bypass ChatGPT’s mobile phone number requirement.
Thanks for the shameless/shill plug of ChatGPT. Continue to use it and give up your privacy. Then again, you probably already have no or care about privacy anyway, so that’s a moot topic.