A new campaign exploits the ExpressVPN brand to trick people into downloading fake installers containing Redline, a widely distributed information stealer.
Victims infect themselves with the malware by launching it, thinking they’re about to install the popular VPN tool and end up losing sensitive data to cybercriminals.
The campaign was discovered by Cyble Research & Intelligence Labs researchers, who shared their findings exclusively with RestorePrivacy.
Impersonation Campaign
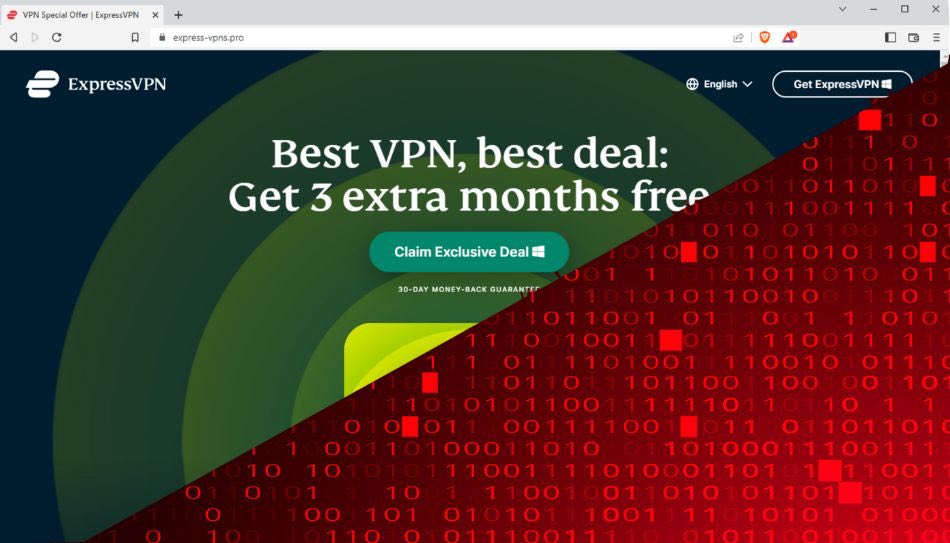
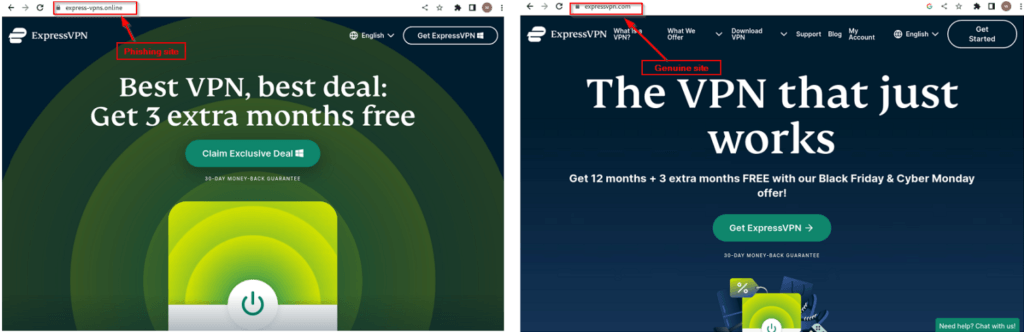
The ongoing brand impersonation campaign uses typosquatting domains made to appear close to ExpressVPN’s actual domain, “expressvpn.com.”
Typosquatting is a technique involving the registration of domain names that are similar to those of the impersonated brands, usually featuring additional characters or letter swaps.
Six examples uncovered by Cyble while investigating this campaign are:
- express-vpns[.]cloud
- express-vpns[.]fun
- express-vpns[.]biz
- express-vpns[.]online
- express-vpns[.]pro
- express-vpns[.]xyz
Victims end up on these sites via phishing emails, malvertising, SEO poisoning, instant messages, or posts on social media and forums.
The appearance of the sites is very close to the real ExpressVPN site, and they even include the three-month free offer the software promoted as part of its Black Friday deal.
Cyble
The threat actors made sure to use valid SSL certificates to make their scam sites appear trustworthy to humans and security tools.
Dropping Redline
Clicking on the embedded button to claim the exclusive deal initiates a ZIP download from a Discord app URL.
The file, “Setup.zip,” contains an artificially oversized executable (setup.exe) to evade analysis and AV scans.
Cyble
Running the executable injects Redline onto a digitally signed compiler program so that it runs directly from memory as a trusted process, preventing security tools from raising any alarms.
Next, the stealer fetches its configuration from the command and control server, which contains guidelines on what data to target on the infected computer.
Redline can steal account credentials, autofill data, cookies, and credit cards stored on Chrome-based browsers and Firefox. It can also target cryptocurrency wallet plugins, cold wallet accounts, VPNs, Discord, Steam, and more.
Redline is a MaaS (malware as a service) information stealer sold to cybercriminals on the dark web for a monthly subscription fee and is currently one of the most widely deployed malware of this kind.
To minimize the chances of dealing with a Redline infection, ensure that you’re always downloading software from official vendor sites, and avoid following links sent via email, SMS, IMs, etc.
Additionally, check downloaded installers on your AV tool before launching them, and validate that the file size looks right for the type of the application.

 Encryption Vendor for Sony, Lexar, and Sandisk Leaked API Keys
Encryption Vendor for Sony, Lexar, and Sandisk Leaked API Keys
Sven Sir indeed users remain the weakest link to their own online security and privacy.
If I am not hiding my digital footprint and internet trail online, then data collected about me will end us being in the hands of malicious actors and nefarious governments who would target me via a well designed social engineering attack to install a malware on my device. About 60% to 70% such attacks by malicious actors are for financial gains that is to steal my banking password and credit card details and empty my bank account.
Above links are suspicious in itself and a well informed person can see they are trying to imitate express VPN website. But gullible and unsuspecting users might easily fall into the trap.
This is where having a good antivirus helps, on both Android and Windows, but specially on Windows as Windows Defender is not enough.
Personally I use ESET and Nord VPN with NextDNS via Yoga DNS. And it works very well.
For example in this case NextDNS and ESET Parental Control successfully blocked access to above links and performed better than Firefox’s own threat protection.
NextDNS’S blocking feature for Newly Registered Domains which blocks domains registered within last 30 days is very very useful and blocks most of the online threats as most malicious websites and links are mostly newly created which have a high chance of infecting users initially before they are detected in a matter of days or weeks or by that time they are removed.
What happened to clone vpn?