
The popular “no logs” VPN service IPVanish appears to be embroiled in a logging scandal whereby user logs were provided to authorities who were investigating a criminal case. While nobody here is defending the actions of criminals, it is important to recognize when a VPN service fails to uphold their “zero logs” policy and commitment to customer privacy.
This yet another case where a VPN service’s “no logs” claims did not stand up to law enforcement actions. IPVanish now joins the likes of PureVPN, HideMyAss, and EarthVPN, which have all provided logs to authorities in various criminal cases – see VPNs are lying about logs for a discussion of these cases.
The facts of the IPVanish logging case
Before jumping into the facts of the case, it is important to note that:
- IPVanish is a US-based VPN service (Five Eyes)
- US authorities (Department of Homeland Security) were targeting a US resident (state of Indiana)
- IPVanish has claimed to have a “strict zero logs policy” for many years (example here)
This specific case involved child abuse and pornography with the US Department of Homeland Security agents investigating an IPVanish user in 2016.
The full affidavit includes graphic descriptions of the material sent by “suspect user” to the DHS agent. You can find the criminal affidavit here (also archived here). However, we will only include the relevant sections below relating to IPVanish and its logging practices.
From page 23 (22 of 28) of the affidavit:
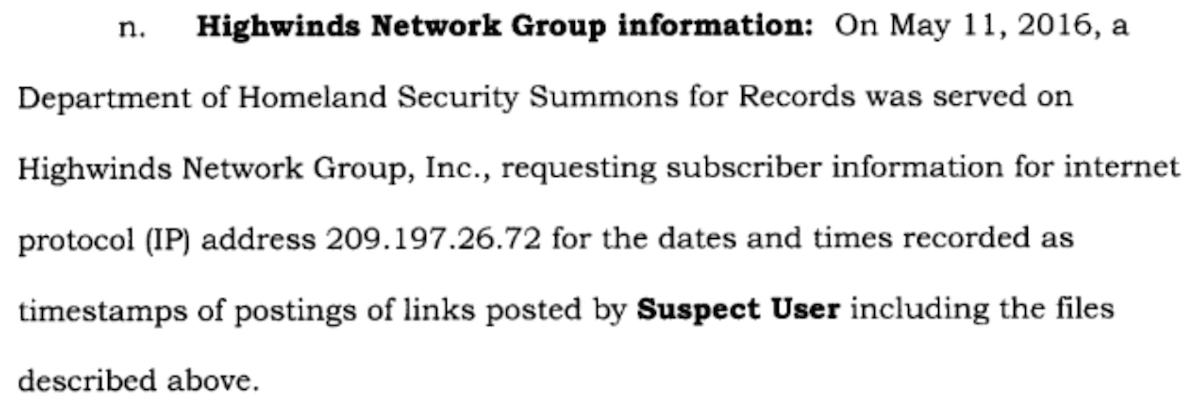
As you can see above, the Department of Homeland Security delivered a “summons for records” to Highwinds Network Group – the parent company of IPVanish. According to these records, authorities did not use a subpoena, search warrant, or a “national security letter” with accompanying gag order. This was merely a summons for user information.
Approximately two weeks later, on May 26, 2016, IPVanish responded to the summons essentially stating that they do not have any user data available because they “do not log any usage information.”
However, after the investigator followed up on the request, Highwinds Network Group (IPVanish) told authorities to “submit a second summons requesting subscriber information more detailed in nature.“
On June 9, 2016 the investigator provided another request to IPVanish for “any data associated with IRC traffic using IP 209.197.26.72, port 6667.” Twelve days later, IPVanish provided the following data logs on the suspect user to DHS authorities:
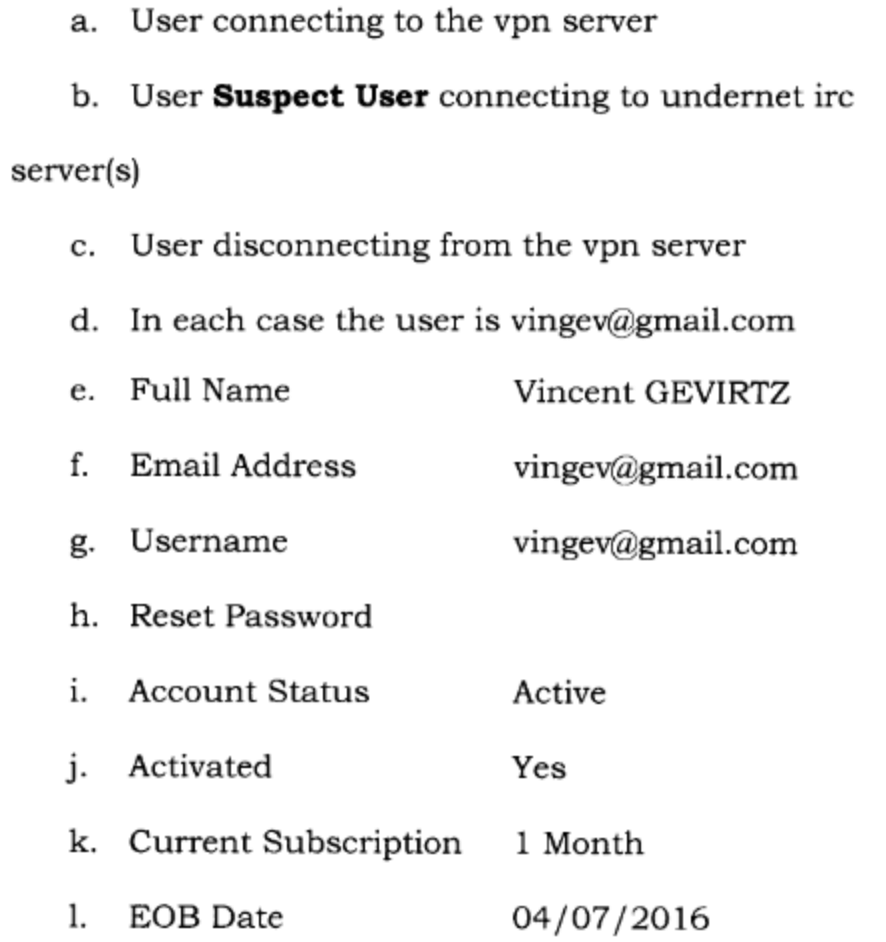
According to the affidavit, IPVanish also provided DHS authorities the following user data:
- source IP address of the suspect user (50.178.206.161)
- dates and times that the suspect user connected to, and disconnected from, the IRC network
The second bullet is significant for this case because it demonstrates that IPVanish is (or was) keeping detailed logs of user activity, which clearly contradicts the “zero log policy” they claim to have.
After getting the connection and usage logs from IPVanish’s parent company Highwinds Network Group, DHS authorities were able to easily identify the user through his Comcast IP address and location in Muncie, Indiana. Comcast then provided additional information on the suspect user to authorities, who then served a federal search warrant on Vincent Gevirtz and his residence in Muncie, Indiana.
IPVanish logging policy
IPVanish has a long history of claiming to be a “zero logs” VPN provider.
Using the WayBack Machine we can see IPVanish’s privacy policy both before the incident (April 2016) and just after the incident (August 2016). During this incident and in both privacy policies you can see that IPVanish was making the following claim:
“IPVanish does not collect or log any traffic or use of its Virtual Private Network service.”
You can even see on their homepage from June 2016 – exactly when this case was unfolding – that IPVanish was claiming to be have a “strict zero-logs policy”:

It’s also interesting to note that IPVanish uses the same “strict zero-logs policy” wording on their homepage today.
IPVanish CEO responds on reddit
After this case made it to r/piracy subreddit, a user by the name of “lavosby” – claiming to be the IPVanish CEO – issued the following response:
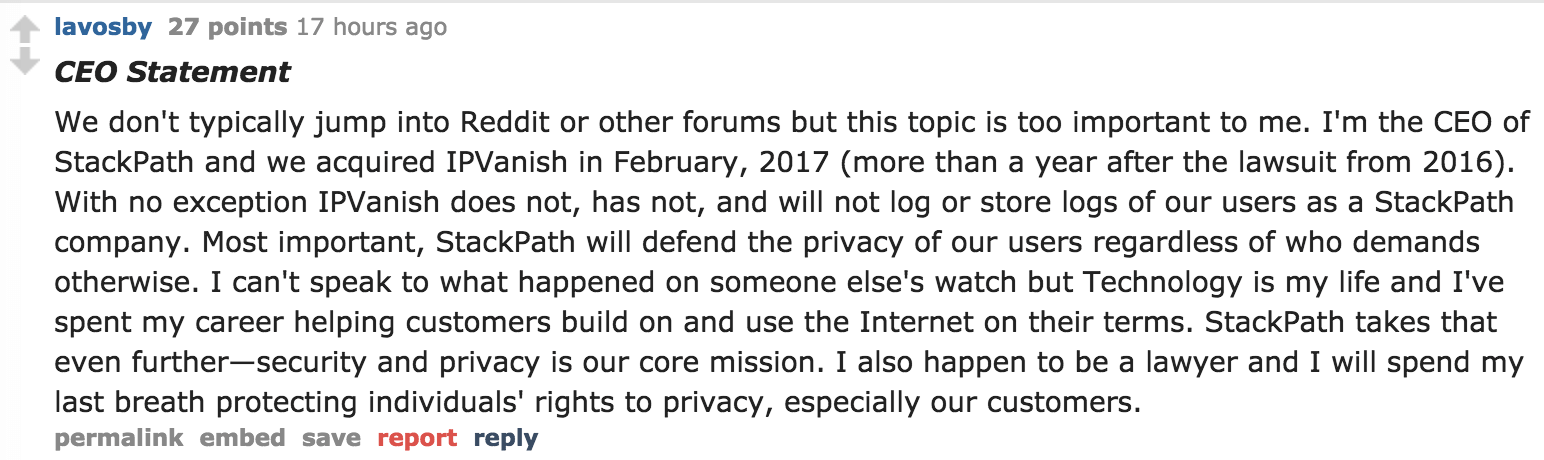
Later in the same thread, the user “lavosby” explained that IPVanish was acquired on February 2, 2017 by Stackpath. Indeed, I found this blog post verifying how Highwinds was acquired by Stackpath in 2017. It now appears that both Highwinds and IPVanish are operating under Stackpath.
In explaining these logging events, lavosby stated:
“We can only surmise, this was a one time directed order from authorities.”
Of course, there is no way to verify if this was true or if IPVanish is truly a “no logs” VPN service today.
What we can verify, however, is that IPVanish was claiming to have a “strict zero-logs policy” at the exact time they were logging user data and handing it over to US authorities.
After requesting a response from IPVanish, they provided Restore Privacy with this statement:
That court case was from 2016 – long before StackPath acquired IPVanish in 2017. IPVanish does not, has not, and will not log or store logs of our users as a StackPath company. We can’t speak to what happened on someone else’s watch, and that management team is long gone. In addition to not logging, StackPath will defend the privacy of our users, regardless of who demands otherwise.
Who can you trust?
This case once again illustrates the fundamental issue when choosing a VPN service: trust.
Unfortunately there have been a few different cases where VPNs have been found to be flagrantly violating their “no logs” claims while providing customer data to authorities. So can you trust any VPN service?
Well, there have also been a few VPNs that have had their logging claims verified by criminal cases. Here are three brief examples of these cases:
- In 2016 Private Internet Access (based in the US) had their “no logs” claims tested in an FBI case involving a fake bomb threat. PIA publicly stated before the court that they did not have any logs that they would be able to provide for the investigation.
- In 2017 Perfect Privacy (based in Switzerland) had two servers seized in Rotterdam. Thanks to no logs and all servers operating in RAM disk mode, no customer data was affected. (The exact reason for the server seizure has not been publicly disclosed by Dutch authorities.)
- In 2017 ExpressVPN (based in the British Virgin Islands) had servers in Turkey seized. Authorities were not able to obtain any user data. ExpressVPN also issued a public statement explaining that they are not be able to provide any data to authorities due to their no logs policy.
These cases also illustrate the importance of choosing a VPN in a good privacy jurisdiction (outside of the 5 Eyes and 14 Eyes countries). After all, US authorities have the ability to force any company to log user data while at the same time hitting them with a gag order to prohibit any kind of disclosure.
As you can see from the affidavit above, US authorities continued putting pressure on IPVanish until they agreed to turn over user data. US authorities have also been successful in obtaining data from overseas VPN providers, as seen in the case with PureVPN.
Closing comments
The point of this article is to highlight the facts surrounding this IPVanish logging case and to illustrate some of the problems with “no logs” claims in the VPN industry.
Please note – this article is not defending or condoning the suspect at the heart of this IPVanish logging case. As a parent, I’m very thankful to the authorities who investigate and prosecute these types of criminals. But as a privacy enthusiast, I’m also concerned that VPNs are misleading people when it comes to logging practices and data protection.
This article will be updated as more information becomes available.
Updated June 6, 2018 with official statement from IPVanish.

[https://www.ipvanish.com/no-log-vpn-policy/]
Update again.