
WireGuard is taking the VPN world by storm. It promises big improvements over existing VPN protocols and so far in 2024, we’ve seen more VPN services moving to WireGuard. But can it deliver better speeds, security, and reliability in real-world testing? This OpenVPN vs WireGuard comparison will answer all of your questions.
For a long time, the gold standard of VPN (Virtual Private Network) protocols has been OpenVPN. It is an open-source protocol with good performance and is considered to be very secure and reliable, having passed numerous independent audits.
But you’re here looking for answers and probably wondering if WireGuard is better than OpenVPN. Perhaps you are considering switching from your current VPN service to one that supports the WireGuard VPN protocol (most of the best VPN services now support WireGuard).
We aim to answer all your questions and more in this WireGuard vs OpenVPN comparison. Here’s what we’ll cover in this in-depth guide:
- Background – What is the history behind OpenVPN and WireGuard?
- Speeds – We ran back-to-back tests across four different server locations in the US – and there was a big winner.
- Encryption – Examining the cryptographic algorithms used by WireGuard and OpenVPN.
- Security – Which protocol offers more security?
- Auditability – Which protocol is easier to audit?
- WireGuard makes it into the Linux and Windows kernels
- Privacy – Does OpenVPN or WireGuard do better in terms of privacy?
- Conclusion – Test out WireGuard yourself
Without further delay, let’s get into the comparisons and test results!
1. Background: OpenVPN vs WireGuard
Before we dive into the technicals, let’s quickly examine the background of each VPN protocol.
OpenVPN
OpenVPN is both a VPN protocol and the code needed to implement that protocol. It consists of open-source software developed by James Yonan and published under the GNU General Public License (GPL). Initially released in 2001, it has become the most widely-used VPN protocol thanks to its flexibility, reliability, and ability to cross Network Address Translators (NATs) and firewalls.
WireGuard
WireGuard is a new approach to a VPN protocol that is meant to be, well, better than current options like IPSec and OpenVPN. Perhaps the best way to explain is to simply quote you from the first paragraph of the WireGuard home page:
WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It aims to be faster, simpler, leaner, and more useful than IPSec, while avoiding the massive headache. It intends to be considerably more performant than OpenVPN. WireGuard is designed as a general purpose VPN for running on embedded interfaces and super computers alike, fit for many different circumstances. Initially released for the Linux kernel, it is now cross-platform (Windows, macOS, BSD, iOS, Android) and widely deployable.
The simpler, leaner part of this is crucial. Whereas the code for OpenVPN runs into hundreds of thousands of lines, the code for WireGuard is currently around 4,000 lines. This, combined with the use of state-of-the-art cryptography, generates results that have many people very excited.
2. OpenVPN vs WireGuard Speeds
Many people are switching to the WireGuard protocol for the performance advantages — namely faster speeds.
We have been testing WireGuard over the past few years and can confirm that performance is (usually) excellent. It not only offers faster speeds, but WireGuard is also faster to establish a connection and is also more reliable on mobile devices.
Minimizing variables: The goal of our speed tests was to see how WireGuard performs in comparison to OpenVPN using a real-world test case and minimizing variables. Because speeds can vary drastically between services, we decided to run back-to-back speed tests with a leading VPN that supports both OpenVPN and WireGuard. For this, we chose NordVPN.
We ran all speed tests on a 1,000 Mbps wired ethernet connection using the same test machine (MacBook Pro). With the NordVPN client, we were able to quickly switch between OpenVPN and WireGuard for back-to-back speed tests, thereby minimizing variables.
This table summarizes the speed test results, conducted across four different locations in the United States. The table is in the order of latency, from the closest location (Seattle) to the furthest (New York).
| City | OpenVPN Speed | WireGuard Speed |
| Seattle | 222 Mbps | 755 Mbps |
| Los Angeles | 226 Mbps | 636 Mbps |
| Chicago | 155 Mbps | 657 Mbps |
| New York | 222 Mbps | 613 Mbps |
The fastest speed achieved was with a NordVPN server in Seattle using the WireGuard protocol (NordLynx). Here is a screenshot of this WireGuard speed test result:
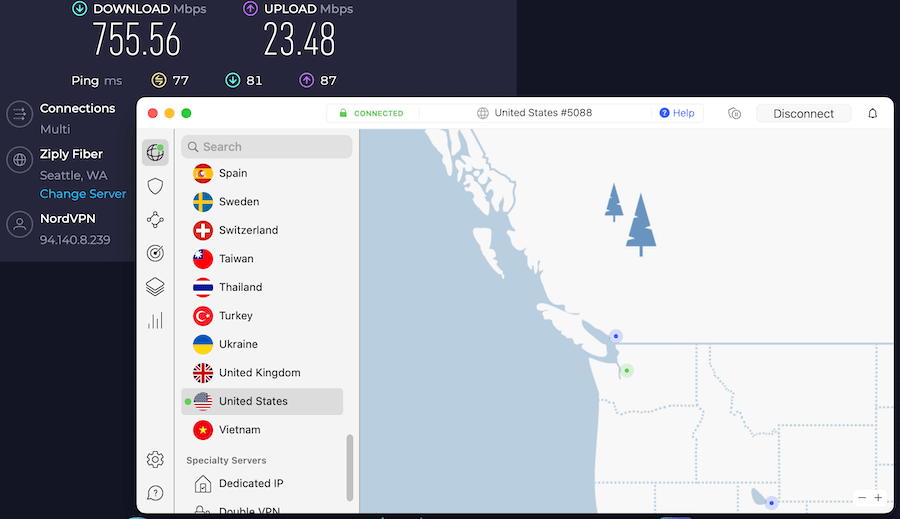
Learn more about NordVPN with WireGuard here >>
So what does all this mean?
WireGuard is consistently faster than OpenVPN in our tests
Key takeaways from testing WireGuard vs OpenVPN speeds:
- On average, WireGuard was about 3.2 times faster than OpenVPN across all the locations we tested.
- WireGuard’s performance advantage over OpenVPN is greater with nearby (low latency) servers in comparison to long-distance (high latency) server locations.
- To get the fastest VPN speeds, use WireGuard on the closest server to your physical location.
We intend to conduct more tests comparing WireGuard and OpenVPN speeds with more locations and will be updating our test results accordingly. Also, note that WireGuard is capable of achieving speeds far beyond what we tested here. As we reported earlier this year, WireGuard hit record speeds in excess of 10Gbit/sec (10,000 Mbps).
Check out the best WireGuard VPNs here.
Additional tests: WireGuard speeds with other VPN providers
Not all VPNs that support WireGuard provide speeds comparable to those above. For example, in the NordVPN vs CyberGhost comparison, both VPNs were tested using the WireGuard VPN protocol, but CyberGhost was significantly slower. Similarly, Private Internet Access also had below-average speeds, even when using the WireGuard VPN protocol.
This suggests that WireGuard has the potential for extremely fast speeds, but as we would expect, there are large differences between VPN services with performance.
Note: We did once see a slower speed with WireGuard than OpenVPN, but this seems to be an anomaly that appeared on Proton VPN and is likely to disappear in our next speed tests of that service. See the UK speed test results in our NordVPN vs Proton VPN comparison for details.
Final verdict on speeds
In speed tests run by our team and others, WireGuard normally delivers much faster speeds than OpenVPN — but this can vary by VPN provider. The faster speeds will be beneficial for anyone needing a VPN for torrenting or any other high-bandwidth activity.
If you want the fastest VPN with WireGuard, I’d recommend checking out NordVPN.
3. Encryption: OpenVPN vs WireGuard
Now we’ll examine the encryption differences between OpenVPN and WireGuard.
OpenVPN Cryptographic Algorithms
OpenVPN uses the OpenSSL library to provide encryption. OpenSSL supports a number of different cryptographic algorithms, including:
- AES, Blowfish, Camellia, ChaCha20, Poly1305, DES, Triple DES, GOST 28147-89, SM4 and more for encryption and authentication
- MD5, MD4, SHA-1, SHA-2, MDC-2, BLAKE2, and more for hashing
- RSA, DSA, X25519, Ed25519, SM2 and more for key derivation and agreement
- UDP or TCP as the Transport Layer protocol
- Perfect Forward Secrecy to protect user data
This range of algorithms makes OpenVPN agile. That is, the code can negotiate the use of different algorithms depending on the circumstances. This makes OpenVPN very flexible, but greatly increases the complexity of the code. OpenVPN’s complexity can slow down execution, which is one of the main reasons people are looking to WireGuard as a possible replacement.
WireGuard Cryptographic Algorithms
The WireGuard philosophy differs greatly from that of OpenVPN when it comes to cryptographic algorithms. Whereas OpenVPN is flexible with the algorithms it uses, each WireGuard version uses one fixed set of algorithms.
The current version of WireGuard (v1.0), uses the following:
- ChaCha20 for symmetric encryption
- Poly1305 for authentication using RFC7539’s AEAD construction
- Curve25519 for Elliptic-curve Diffie–Hellman (ECDH) anonymous key agreement
- BLAKE2s for hashing (RFC7693)
- SipHash24 for hashtable keys
- HKDF for key derivation (RFC5869)
- UDP as the Transport Layer protocol
- Perfect Forward Secrecy (PFS) to protect user data
WireGuard also differs from OpenVPN in that OpenVPN uses certificates for identification and encryption. WireGuard uses public key encryption for those tasks. Secure key generation and management are handled in the background, and there is an option to pre-share a key for an additional layer of security.
Verdict on cryptographic agility
Depending on your perspective, this can go either way. OpenVPN can run many different ciphers and protocols, but this agility brings with it more complexity, a larger attack surface for hackers to exploit, and possible susceptibility to downgrade attacks.
Each version of WireGuard runs one set of ciphers and protocols. This leads to less complexity (and far less code), a smaller attack surface, and immunity to downgrade attacks. It will, however, force all endpoints to upgrade to a new version of WireGuard if a problem is discovered in any of the ciphers or protocols used in the current version.
4. Security: OpenVPN vs WireGuard
Is OpenVPN secure?
OpenVPN has no known security vulnerabilities. The code has been audited numerous times and has the backing of many security experts.
Is WireGuard secure?
WireGuard is very secure. It uses faster, state-of-the-art secure ciphers and algorithms. Its small codebase makes it easier to audit while offering a smaller attack surface for anyone trying to hack it. But perhaps most importantly WireGuard,
“…intentionally lacks cipher and protocol agility. If holes are found in the underlying primitives, all endpoints will be required to update. As shown by the continuing torrent of SSL/TLS vulnerabilities, cipher agility increases complexity monumentally.”
— Jason A. Donenfeld, Developer of WireGuard
Forcing all endpoints to move to a new version of WireGuard may cause some headaches. However, since the new version will not include the compromised cipher or protocol, it ensures that no one continues to use the insecure code. It also eliminates the possibility of a downgrade attack forcing the endpoint to drop back to using the compromised code.
Verdict on Security
There are no known security flaws in either protocol. If security is your topmost priority, the conservative option is OpenVPN. It has simply been around much longer than WireGuard, gone through more third-party security audits, and has a far longer track record than WireGuard. However, as WireGuard matures, its updated encryption algorithms and minimal codebase make it all the more attractive.
5. Auditability: OpenVPN vs WireGuard
To know if you can trust a VPN protocol, it needs to be auditable. Auditability is one of the key reasons that open-source software is preferred by most privacy advocates.
But just because code is open source doesn’t make it easy to audit. OpenVPN is auditable. But with hundreds of thousands of lines of code, actually doing an audit requires a team of experts and a lot of time.
WireGuard is also open source and auditable. But with somewhere around 4,000 lines of code, it is much more amenable to an audit. A single engineer could conceivably do the job in a short while.
“Can I just once again state my love for it [WireGuard] and hope it gets merged soon? Maybe the code isn’t perfect, but I’ve skimmed it, and compared to the horrors that are OpenVPN and IPSec, it’s a work of art.”
— Linus Torvalds, Principal developer of the Linux kernel, August 2018
We have to give the nod to WireGuard when it comes to auditability.
6. WireGuard in the Linux and Windows kernels
WireGuard was also designed with the Linux operating system in mind. More specifically, with being incorporated into the Linux Kernel.
According to WireGuard: Next Generation Kernel Network Tunnel, there were five reasons to include WireGuard in the Linux Kernel:
- Short and simple code to make auditing and reviewing the code enjoyable
- To be extremely fast
- It must avoid resource-intensive allocations in response to incoming packets
- It must integrate as natively and smoothly as possible
- It must be buildable as an external kernel module that doesn’t require changes to core Linux code
The result is a fast, efficient VPN protocol running on OSI Layer 3, the Network Layer. On this level, WireGuard has more direct access to network routing tables and data packets, which helps with speed and simplifies authentication and attribution of data packets.
WireGuard’s presence in the Linux Kernel is one of the big reasons for its higher performance relative to OpenVPN and other protocols that run in the operating system’s user space, with its additional overhead.
WireGuard has also made it into the Windows kernel, as of August 2021.
7. Privacy comparison: OpenVPN vs WireGuard
Does OpenVPN protect my privacy?
VPN protocols provide security; they don’t necessarily provide privacy. What determines your privacy when using a VPN is actually the policies of the VPN service. In particular, whether or not a VPN service keeps logs is what determines your privacy when using one.
That may sound odd if you have heard that WireGuard has a privacy problem. We’ll go into more detail later, but that problem comes down to an aspect of the design of WireGuard that can maintain a user’s IP address on the VPN server for extended periods of time.
The design of OpenVPN does not require keeping any such user data on the VPN server, so it doesn’t compromise your privacy.
Does WireGuard have a privacy problem?
WireGuard was designed for speed and security. It was not specifically designed for people like us, who look to their VPN service for both security and privacy. However, in order to give users the benefits of WireGuard, VPN services have come up with WireGuard solutions that add strong privacy protections without sacrificing what makes WireGuard special. Here’s the problem:
WireGuard stores user IP addresses on the VPN server
As part of its cryptokey routing algorithm, WireGuard maps the public keys and allowed IP (Internet Protocol) addresses. This simplifies certain aspects of WireGuard, but by default, it results in user IP addresses remaining stored on the VPN server until the server is rebooted. Storing your IP address on the server like this could be considered logging your IP address and is incompatible with the concept of a no-logs VPN. This static IP address could also be exposed by a WebRTC leak.
How can WireGuard’s privacy problem be fixed?
VPN services have come up with a few different solutions to WireGuard’s privacy problem.
NordVPN developed a double-NAT system for their WireGuard implementation, which they call NordLynx. The system,
…creates two local network interfaces for each user. The first interface assigns a local IP address to all users connected to a server. Unlike in the original WireGuard protocol, each user gets the same IP address.
Once a VPN tunnel is established, the second network interface with a dynamic NAT system kicks in. The system assigns a unique IP address for each tunnel. This way, internet packets can travel between the user and their desired destination without getting mixed up.
The double NAT system allows us to establish a secure VPN connection without storing any identifiable data on a server. Dynamic local IP addresses remain assigned only while the session is active. Meanwhile, user authentication is done with the help of a secure external database.
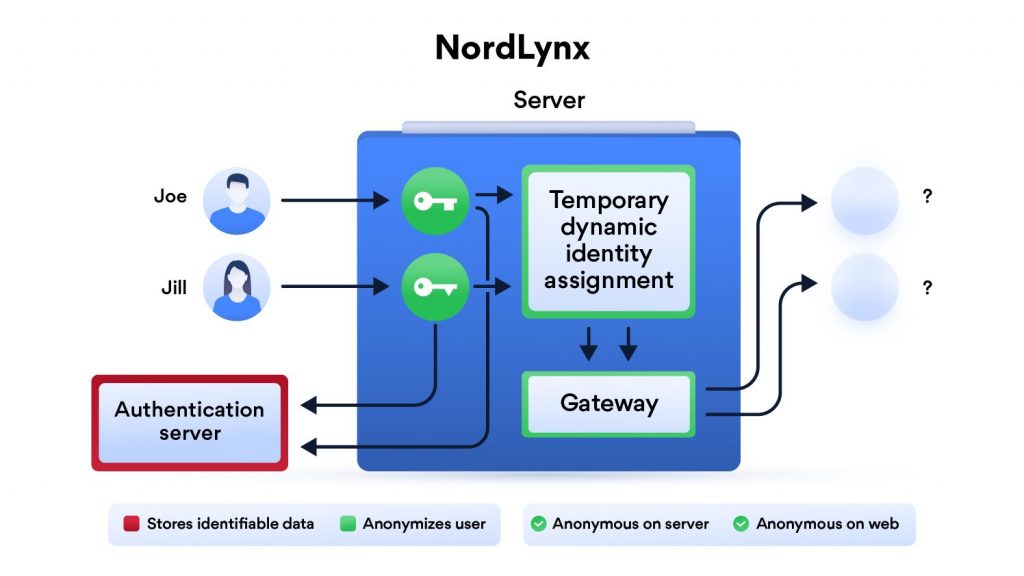
More info on NordVPN and NordLynx is here >>
This solution is now available across all NordVPN clients, which is what we used for all tests in this guide.
Other services such as Mullvad and OVPN have addressed the WireGuard privacy issue by erasing the records that map IP addresses to encryption keys as soon as there has been no communication between the VPN client and server for three minutes. Keeping the data only as long as it is necessary greatly reduces the risk of personal data being revealed.
Additional protection in cases like these is to ensure that you are not experiencing any WebRTC leaks. Here’s a link to our complete guide to fixing WebRTC leaks.
Final Verdict on Privacy
This is one area where OpenVPN has an advantage. The default design of WireGuard requires user IP addresses to remain on the VPN server for extended periods of time. If privacy is a top concern, we recommend that you only use solutions that address this potential privacy issue.
NordVPN’s NordLynx is the solution we are currently using, but Mullvad and OVPN also have practical solutions available as well. We fully expect that as other VPN services roll out their WireGuard solutions, they too will deal with the IP address privacy issue.
Note: See our guide on the best VPNs for WireGuard for more info.
Conclusion: Test WireGuard for yourself
We weren’t always fans of the WireGuard VPN protocol.
When it first came out, there were lingering concerns about privacy, IP address logs stored on the server, and the new and experimental nature of the protocol. It simply did not seem like a great solution for people who use VPNs with privacy in mind. But a lot has changed in the past year:
- Many VPNs have found good solutions to support WireGuard while still ensuring user privacy.
- WireGuard has officially been released (no longer experimental code) and is gaining traction with more VPN services.
- WireGuard has now been incorporated into the Linux kernel, a major landmark.
- Lots of tests have proven the significant performance advantage that WireGuard enjoys over existing VPN protocols.
WireGuard has a lot to offer VPN users, in many different use cases. If you have considered using WireGuard, give it a shot to see the advantages yourself. Two leading VPNs that support WireGuard are NordVPN and Surfshark.
While there are a handful of VPNs that support WireGuard, our current top-recommended VPN for WireGuard is NordVPN. It delivers on speed, security, privacy, and many other areas, as discussed in our NordVPN review.
Tip: Test WireGuard for yourself and use the coupon below for the best savings.
NordVPN’s Cyber Deal is live:
Get 69% Off NordVPN two-year subscriptions plus 3 months extra:
(Coupon is applied automatically; 30 day money-back guarantee.)
Feel free to share your experiences in using WireGuard in comparison with OpenVPN below.
This WireGuard vs OpenVPN guide was last updated on April 10, 2024.

I’ll bite-
How are you justifying WireGuard test results that are between 22% (613 Mbps to New York) and 51% (755 Mbps to Seattle) faster than your maximum data throughput of 500 Mbps as valid? ISPs can burst some but I’ve never seen 50% above your rated download speed. This implies to be either cached, compressed, or accelerated test results and would not be indicative of the real world.
Your testbench isn’t reproducible thus the results should not be trusted. There is no mention of:
1. Your ISP. Some are notoriously bad while others known to accelerate speed “tests” especially to Ookla (Speedtest.net) sites.
2. Your physical location in relation to each test site. Are you geo near New York in which case those are poor results? Are you geo near Seattle and on the same backbone as Ziply Fiber in which case that could justify the 51% bump?
3. Your non-VPN speed tests to the same locations on the same test servers.
4. The source of the “500 Mbps” limitation. Is it your ISP, router, switch, MacBook, or something else?
No matter how you slice it no VPN is *faster* than plain Ethernet traffic at 500 Mbps without doing something to your traffic.
Hi FCC User, yes, you are correct, and that was a typo that we should have caught months ago. In an old version of this article, we ran all tests on a 500 Mbps connection. However, after upgrading our test lab to 1,000, we ran all new tests and updated this guide with the results. But we clearly forgot to update the old references to 500 Mbps for the baseline. ISP is Vyve, location is in the northwest USA (physically closest to Seattle servers). Sorry for the confusion, and thanks for pointing that out! It’s fixed now.
I think when you write articles like this you should remember who and what your audience is. I assume most people, like me, see your address, http://www.restoreprivacy.com and conclude that internet privacy is at the forefront or your articles and from that we can fairly safely say that ordinary consumers are the majority of your reader base. That’s not to say that a wider view of a product should be ignored. Most consumers who are concerned by privacy will weigh a product’s privacy performance rather highly and then look to the other major issues in running a VPN, ease of setup/maintenance and throughput speed. You address the speed issue well but not a mention of setup, anyone who has setup an OpenVPN will scarcely believe you can have a Wireguard VPN setup and running with change from 5 minutes.
On the issue of privacy it appears to me you see the issue as being one of someone discovering that you have a VPN account whereas as I would see it as an issue of people being able to see what I am downloading which cannot be determined from the Wirguard server, please correct me if I am mistaken. So basically your comments on privacy could best be described as moot?
Wireguard is not “extremally easy”. It is easy in only one, simple usecase – simple connecting two peers using simple addressing and communicating to each other. I was quite surprised that I can’t find any a bit more complicated usecase examples other than “lets connect two directly reachable hosts over the internet and do ping/ssh”. When it comes to use Wireguard for L3 transport, eg. using it as a plain tunnel (which it should be extra obious!) it fails miserably. It breaks few network design/usage scenario principles, where it should be straight forward – giving a system interface (wg0) should give you all possibilities to route, nat, ipv6, etc. etc. but … it doesn’t. Routing in WG is a pain (their AllowedIPs is an abomination of access-list, routing tables, split tunnels and route injecting) OpenVPN and IPSec is superior in that, still.
You have a speed comparison table at top of page. UDP is known to be faster than TCP and therefore good for streaming. OpenVPN can use either TCP or UDP. Which one was used for your test?
I learned a lot here. I always suspected AES had some vulnerabilities or backdoors. I would like to know if ChaCha2-Poly1305 is more secure. I only know that it is not deoendent on hardware for encryption the way AES and many others are.
We used OpenVPN UDP for our tests for the best performance possible.
There are disadvantages in the area of data minimization (according to Art. 5 (1) c GDPR) or anonymization: both logging and a fixed IP address are required for the client
Security
Here WireGuard is (still) at a disadvantage compared to protocols such as OpenVPN and IPsec. With cryptokey routing, the server and client receive a static IP address, which is stored in the server’s configuration file. This basically allows conclusions to be drawn about the user’s identity, which inevitably clashes with the no-log policy of many VPN providers. However, resourceful manufacturers like NordVPN or Surfshark have already found their own ways to get around this Achilles heel. We will introduce you to some of the services below!
I wouldn’t use wireguard and with openvpn 2.5+ with hidemy.name I have about 96/24mbs, but I only have an 80/20 LTE tariff! What’s the point of being quick if it’s not safe?
p.s. Express VPN also has WireGuard it is called Lightway
Kind regards
No, Lightway is not WireGuard.
I can only speak out of experience. I am an end user, I used Express-vpn for years. But it got slow from Peru towards the Netherlands. I had problems watching streaming Dutch TV. They not support Wireguard. I then move over to Surfshark with Wireguard on the same router (Netgear with now Openwrt) and everything works again like a dream. A speedtest showed roughly twice the speed.
> OpenVPN has no known security vulnerabilities. The code has been audited numerous times and has the backing of many security experts.
I would recommend revising this statement. The security of OpenVPN is highly dependent on the specific configuration of an OpenVPN server. For example, on some distributions, the default OpenVPN configuration may be insecure with outdated defaults (e.g. TLS 1.1 or 1.2).
One could argue that less configuration options reduce surface area for vulnerabilities and attacks.
There is a difference in the code having vulnerabilities and how the end user configures the system. 🙂
UPDATE for readers:
NordVPN is running a Christmas sale with 3 months free.
AES 256 CBC, GCM can be cached timed attacked downgraded to either 192, or 128, bit encryption and used a not so secret index with backdoors for you know who, AES is only random 2^68 at best before birthday collisions occur, Wireguard at least 2^80 open VPN has up to 400,000 lines of code IPSec 600,000 and several venerability’s Open Vpn does use a Dynamic IP address Wireguard at static one that’s why you pair it with Nord Lynx double NAT or CyberGhost restful API an 4096 bit RSA key for secondary authentication and a daemon with can dynamically assign IP addresses where Wireguard cant plus 4096bit ECDH Diffie Hellmann keys for perfect forward secrecy AES is also 24 years old so it is not so secure anymore but was great at the time Interestingly some Cryptography experts say AES 128 bit may be more secure than AES 256 due to fewer Birthday collisions.
Steven meet punctuation, punctuation meet Steven.
I bet you two will have a lot to talk! 🙂
Hey bro I speak 6 language’s English in hard bro and not my first language cut me some slack I’m only trying to give you guys info so you can make an informed decision your self’s.
Doesn’t excuse you from making your text at least more readable, like c’mon you learned 6 languages you should at least be able to write text with punctuations right? Don’t tell me all the other languages you learned don’t have any.
Thanks for the information though. On this part it’s a good take.
Wireguard App design is for monkeys
It has practically “no settings!” for http and proxy
AES 256 CBC, GCM can be cached timed attacked downgraded to either 192, or 128 bit encryption and used a not so secret index with backdoors for you know who, AES is only random 2^68 at best before birthday collisions occur, Wireguard at least 2^80 open VPN has up to 400,000 lines of code IPSec 600,000 and several venerability’s Open Vpn does use a Dynamic IP address Wireguard at static one that’s why you pair it with Nord Lynx double NAT or CyberGhost restful API an 4096 bit RSA key for secondary authentication and a daemon with can dynamically assign Ip addresses where Wireguard cant plus 4096bit EDCH Diffie Hellmann keys for perfect forward secrecy AES is also 24 years old so it is not so secure anymore but was great at the time.
and what about SoftEther?
Its already 2022, but WiredGuard doesn’t offer to publish routes for split tunnel purposes? Correct me on this regard Sven.
The reason they don’t is this creates a potential back door through the unencrypted tunnel an unnecessary risk the encryption could be bypassed the original version of IKEV1 was only encrypted one way eg… one direction any could be completely bypassed that’s why IKEV2 was released Microsoft got caught out bigtime that’s why I don’t use it only Wireguard paired with additional security measures.
I agree, SPI firewalls from companies might block unknown outgoing UDP packets.
I use TCP on port 443 so that it looks like an HTTPS connection, alle firewalls allow this combination of outgoing configuration, since they cannot see the difference between een https connection and my openvpn connection.
Something that I also miss is a comparrison of CPU load between these two protocols.
Is wireguard heavier on the cpu or is openvpn heavier on the cpu?
And does Wireguard support hardware acceleration for cryptographic calculations like openvpn? Because that makes a huge impact on the CPU
Any info on ipvanish implementation of wireguard?
Yep, they have added WireGuard and we’ll be adding them to the list with the next update.