
As awareness of global surveillance grows, more people are looking for information about the Five Eyes, Nine Eyes, and 14 Eyes surveillance alliances. This guide is regularly updated with new information and gives you everything you need to know right now. We also list recommended privacy services (Email, VPN, and Private Search Engines) that are outside of the Five Eyes.
The terms “Five Eyes” (a.k.a. FVEY), “Nine Eyes”, and “14 Eyes” often appear in the privacy community, especially when discussing VPNs and other privacy tools. So what are these organizations?
In short, these are international surveillance alliances representing various countries around the world. These alliances work together to collect and share mass surveillance data with each other. Beginning with the UKUSA agreement and Five Eyes intelligence sharing, these networks have been spying on people for decades, with established policies going back to World War II, as we’ll discuss below.
The government agencies behind these efforts often work with internet service providers and other large tech companies to tap key infrastructure for the collection of private data (data surveillance). This turns your internet service provider, for example, into a local adversary that is spying on you for state agencies. And no, this is not a theory.
These practices are well-documented in the PRISM surveillance documents and also the infamous Room 641a example with AT&T and the NSA. Fortunately, there are some simple solutions to keep your data safe that we’ll cover below.
In this guide, we’ll explain all the different “X” eyes surveillance alliances and why this topic is important when choosing privacy tools. Here’s what we’ll cover:
- Five Eyes
- Six Eyes?
- Nine Eyes
- 14 Eyes
- NSA and GCHQ cooperation within 5 Eyes
- ECHELON surveillance system
- The importance of avoiding 5 Eyes
- Recommended privacy services that are outside of the 5 Eyes, including
- Secure email services
- VPNs
- Private search engines
So let’s get started!
Five Eyes
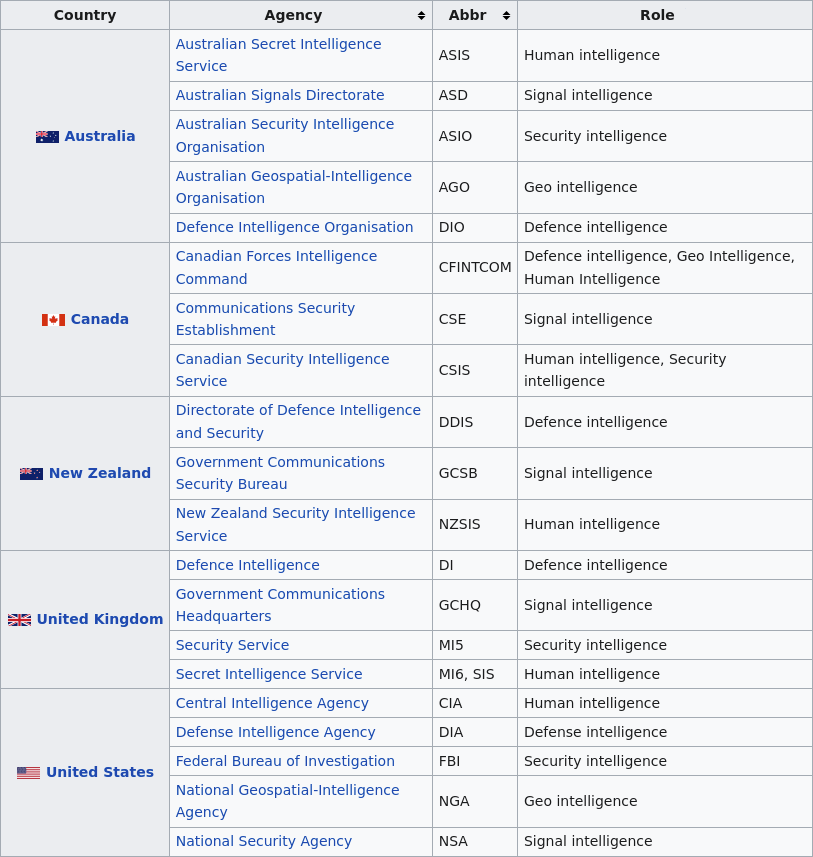
The Five Eyes (FVEY) surveillance alliance includes the following countries:
- Australia
- Canada
- New Zealand
- United Kingdom
- United States
The history of this alliance goes back to WWII and the UKUSA Agreement, which was officially enacted after the war in 1946. This agreement formalized a partnership between the United Kingdom and the United States for gathering and sharing intelligence data.
The partnership continued throughout the Cold War and has only strengthened since the “Global War on Terror” kicked off in the early 2000s. Edward Snowden brought renewed focus to the Five Eyes surveillance alliance in 2013 when he exposed the surveillance activities of the US government and its allies.
Below are the different “5 Eyes” surveillance agencies working together to collect and record your activities.
5 Eyes countries
In addition to these national organizations, there exists the Five Eyes Intelligence Oversight and Review Council (FIORC). According to the FIORC web page on the US Director of National Intelligence website,
FIORC was created in the spirit of the existing Five Eyes partnership, the intelligence alliance comprising Australia, Canada, New Zealand, the United Kingdom, and the United States.
It further states that,
The Council members exchange views on subjects of mutual interest and concern; compare best practices in review and oversight methodology; explore areas where cooperation on reviews and the sharing of results is permitted where appropriate; encourage transparency to the largest extent possible to enhance public trust; and maintain contact with political offices, oversight and review committees, and non-Five Eyes countries as appropriate.
The following non-political intelligence oversight, review, and security entities of the Five Eyes countries are part of FIORC:
- The Office of the Inspector-General of Intelligence and Security of Australia
- The National Security and Intelligence Review Agency of Canada
- The Office of the Intelligence Commissioner of Canada
- The Commissioner of Intelligence Warrants and the Office of the Inspector-General of Intelligence and Security of New Zealand
- The Investigatory Powers Commissioner’s Office of the United Kingdom
- The Office of the Inspector General of the Intelligence Community of the United States
You can get more information about FIORC, including a copy of the organization’s charter, here.
It is no surprise that some of the Five Eyes countries listed above are also the worst abusers of online privacy:
- United Kingdom – Since the passage of the Investigatory Powers Act in 2016, internet service providers and telecoms have been recording browsing history, connection times, and text messages. The data is stored for two years and is available to UK government agencies and their partners without any warrant.
- United States – The US government has been implementing Orwellian mass surveillance collection methods with the help of large telecoms and internet service providers (see the PRISM program). In March 2017, internet service providers were given the legal authority to record user activity and sell this to third parties. Of course, internet providers have been collecting data on their customers for many years, long before this law passed in 2017.
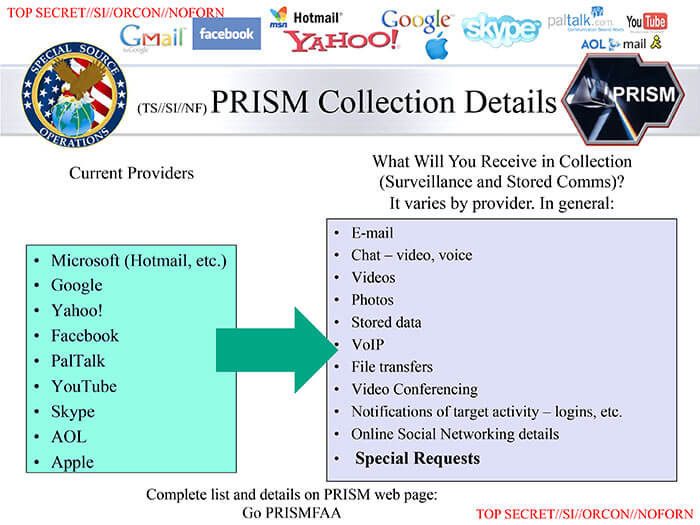
Source: Wikipedia
- Australia – Australia has also implemented sweeping data retention laws similar to the United Kingdom.
Broad authority among 5 Eyes countries
Whether it is the NSA in the United States or the GCHQ in the United Kingdom, the “5 Eyes” is home to the most powerful surveillance agencies in the world. A privacy company sharing a jurisdiction with entities like these is just asking for trouble.
In particular, the intelligence agencies in the Five Eyes countries have tremendous authority to force companies to record and hand over data. In the United States, the Patriot Act ushered in a new level of power for federal data collection, especially through the use of National Security Letters. We see these same trends unfolding in the UK, Australia, and other locations as well.
Six Eyes?
In a 2020 Nikkei interview, Japanese Defense Minister Taro Kono discussed tighter cooperation with Five Eyes, telling an interviewer that,
These countries share the same values. Japan can get closer [to the alliance] even to the extent of it being called the ‘Six Eyes‘.
Reportedly both the United States and United Kingdom have shown some interest in this, perhaps in response to the growing risks of armed conflict with China. While this appears to be just talk right now, we’ll keep an eye on the situation and update our articles as necessary.
Nine Eyes
The Nine Eyes countries include:
- 5 Eyes countries +
- Denmark
- France
- Netherlands
- Norway
The existence of the Nine Eyes alliance is referenced in various sources online and became well-known following the Snowden revelations in 2013. It is just an extension of the Five Eyes alliance with similar cooperation to collect and share mass surveillance data.
14 Eyes
The 14 Eyes surveillance countries include:
- 9 Eyes countries +
- Germany
- Belgium
- Italy
- Sweden
- Spain
As before, the original surveillance agreement was extended to these other countries. The official name of this group of countries is referred to as SIGINT Seniors Europe (SSEUR).
NSA and GCHQ cooperation within 5 Eyes
Various government document releases, which have come out through official FOIA channels, reveal the close relationship between the NSA and GCHQ. Being the two most powerful surveillance entities in the world, with historical ties, it is no surprise that they work closely together.
A top-secret NSA document from 1985, which was released in 2018 via a FOIA request, reveals that this close cooperation continues today, based on the broadly-written UKUSA Agreement:
The UKUSA Agreement, dated 5 March 1946, has twelve short paragraphs and was so generally written that, with the exception of a few proper nouns, no changes to it have been made. It was signed by a UK representative of the London Signals Intelligence Board and the U.S. Senior Member of the State-Army-Navy Communications Intelligence Board (a predecessor organization which evolved to be the present National foreign Intelligence Board). The principles remain intact, allowing for a full and interdependent partnership. In effect, the basic agreement allows for the exchange of all COMINT results including end product and pertinent collateral data from each pattern for targets worldwide, unless specifically excluded from the agreement at the request of either party.
Another top-secret NSA document from 1997 (officially released in 2018) further elaborates on the close cooperation between the NSA and GCHQ:
Some GCHQ [redacted] exist solely to satisfy NSA tasking. NSA and GCHQ jointly address collection plans to reduce duplication and maximize coverage through joint sites and cross-tasking, despite site closures.
With the reference to “joint sites” above, it’s important to discuss ECHELON.
ECHELON surveillance system
ECHELON is a network of spy stations utilized by Five Eyes countries for large-scale espionage and data collection.

The Guardian described ECHELON as a a global network of electronic spy stations that can eavesdrop on telephones, faxes and computers. It can even track bank accounts. This information is stored in Echelon computers, which can keep millions of records on individuals.
Officially, however, Echelon doesn’t exist. Although evidence of Echelon has been growing since the mid-1990s, America flatly denies that it exists, while the UK government’s responses to questions about the system remain evasive.
Despite these denials, there have been whistleblowers who have confirmed what’s going on behind the scenes. Both Perry Fellwock and Margaret Newsham came forward to document various aspects of ECHELON to the public.
Avoid the 5 Eyes
While there are privacy concerns with the other countries in the greater 14 Eyes alliances, the big one to avoid is the Five Eyes. Therefore, when data security is critical, simply avoid the Five Eyes: US, UK, Canada, Australia, and New Zealand
Some people say concerns about these surveillance jurisdictions are overblown or misguided, and that it really doesn’t matter. You often hear this argument from VPN companies (and their marketers) that are based in the US or Canada, for example. This line of thinking is misinformed and ignores reality.
There are many examples that prove the real-world risks associated with privacy-focused companies operating in Five Eyes jurisdictions. Here are just a few that we’ve discussed before on RestorePrivacy over the years:
- Riseup, a Seattle-based VPN and email service, was forced to collect user data for government agents and was also hit with a “gag order” to prevent any disclosure to their users. (They also could not update their warrant canary.)
- Lavabit, another US-based email service, was forced to provide encryption keys and full access to user emails. Rather than comply, the owner decided to shut down Lavabit email.
- IPVanish, a US-based VPN service, was forced to collect user data for an FBI criminal investigation. This all transpired while IPVanish was claiming to be a “no logs VPN” — and they could not alert their users to what was happening. (See the IPVanish logs case.)
- HideMyAss, a UK VPN service was also ordered by a court to collect user data and hand this over to authorities for a criminal investigation. News about this came out after-the-fact.
VPNs operating in the US, and by extension all of their users, can also be the targets of lawsuits involving copyright infringement. A recent court case involved TorGuard VPN, which was forced to block torrenting on all US servers as part of the settlement agreement. This is why we recommend avoiding US-based VPNs when using a VPN for torrenting.
These are just a few cases that have publicly come to light, but you can be sure there are other examples we don’t know even about.
Secret demands for user data + gag orders = privacy nightmare
As we can see from these examples, when authorities compel businesses to collect and hand over data, they usually serve them with a gag order as well. This is done through National Security Letters and it prevents the business from disclosing any information to their customers.
These laws basically give the government the authority to compel a legitimate privacy-focused company to become a data collection tool for state agencies, without any warning or notification. Even warrant canaries are ineffective in places like the United States.
Ignoring the jurisdiction of a privacy-focused business is foolish and ignores these well-documented risks.
Recommended privacy services (in good jurisdictions)
One of the main purposes of RestorePrivacy is to test, research, and recommend privacy and security tools that meet specific criteria. Given our emphasis on data security and trust, jurisdiction is a key factor we consider.
In terms of jurisdiction, our main concern is avoiding Five Eyes countries. After all, some of the 9 and 14 Eyes countries do indeed have strong privacy laws, especially in comparison to the US and UK.
Secure email outside Five Eyes
Using a secure and private email service in a safe jurisdiction is a no-brainer. Consider this:
- Yahoo was found to be scanning emails in real-time for US surveillance agencies.
- Gmail was found to be giving third parties full access to user emails and also tracking all purchases via receipts in your inbox.
- Advertisers were allowed to scan Yahoo and AOL accounts to “identify and segment potential customers by picking up on contextual buying signals, and past purchases.”
Alternatives – Here are some of our favorite secure email services that we tested:
- Proton Mail – Best for strong encryption (33% off coupon)
- StartMail – Private email hosted in The Netherlands (50% off coupon)
- Mailfence – A secure and customizable email service
- Tutanota – Secure Email for Any Device
- Mailbox.org – Affordable private German email service
- Posteo – Reliable anonymous email service
- Runbox – Private email in Norway
- CounterMail – Swedish email with strong security features
- Kolab Now: Swiss email, compliant with GDPR, HIPAA, and PCI
- Soverin – Basic private email service
We also have a guide on encrypted email services here.
VPNs outside the Five Eyes
As mentioned above, internet service providers are actively collecting data for government agencies around the world. They do this by either actively snooping on connections or simply recording all your DNS requests. Additionally, advertisers and other third-parties will track and record your online activity that is tied to your unique IP address.
A good VPN service is absolutely essential for basic online privacy, especially when ISPs are logging everything. A VPN encrypts all your traffic between your computer/device and the VPN server you are connected to. Not only does this make your traffic and online activities completely unreadable to your ISP and other third parties, it also hides your IP address and location.
We have an in-depth list of the best VPN services that are located outside of the Five Eyes countries.
Note: Some people are worried about logs and data collection with VPNs. Fortunately, there are a few verified no logs VPNs that have undergone independent audits to confirm their no-logs policies:
- NordVPN was audited to PwC AG in Zurich, Switzerland to confirm essential privacy-protection measures and the no-logs policy. NordVPN has committed to annual third-party audits, while also undergoing independent security audits and penetration testing carried out by Versprite.
- Surfshark passed a no logs audit last year and has also passed numerous third-party security audits, similar to NordVPN.
- ExpressVPN has been audited twice by PwC to verify its no-logs policy. Additionally, ExpressVPN has passed security audits conducted by Cure53.
- ProtonVPN has also passed a third-party no logs audit conducted in 2022.
Private search engines outside Five Eyes
Most of the big search engines, such as Google, record all your search queries and then link this to your identity and data profile, so you can be hit with targeted ads. Unless you want to give Google and its partners all your search activities, consider using alternatives.
Here are some private search engines you may want to consider:
There are a few search engines based in Five Eyes countries that we still recommend. These include:
- DuckDuckGo (United States)
- Mojeek (United Kingdom)
- Brave Search (United States)
For additional tools and tips, see the main privacy tools page.
Trust and jurisdiction
In the end, jurisdiction is just one of many factors to consider when selecting reliable privacy tools for your unique needs. How much it matters depends on your own circumstances, particularly your threat model and the types of adversaries you are looking to protect yourself against.
For those seeking higher levels of privacy and security, jurisdiction is indeed important, especially when you consider the growing power of governments to force companies to hand over data and log users.
Trust is also a major factor you should consider. After all, a VPN can operate in a “good” overseas jurisdiction, yet still lie to customers and provide data to government agencies. Take for example PureVPN, a “no logs” service based in Hong Kong that gave US authorities connection logs for a criminal case.
This is where trust is key. Fortunately, to strengthen trust, more privacy-focused businesses are undergoing independent audits and third-party verifications. In addition to the VPN audits we mentioned above, we also see this trend with password managers and occasionally with secure email services.
Are these the only international intelligence alliances?
Most definitely not. In addition to the Five Eyes (FVEY), Nine Eyes, and 14 Eyes (SIGINT Seniors Europe), there are other organizations we know of. Examples include the SIGINT Seniors Pacific, the Quadrilateral Security Dialog (the Quad), and the Club de Berne. There may also be other such organizations that we still don’t know about.
Will Japan become a “Sixth Eye”?
Japan has publicly suggested that they would like to work more closely with the Five Eyes, and perhaps some day become a Sixth Eye. As of now it appears to be only talk, but growing tension between Japan and China seems to be moving Japan toward ever stronger connections with the Five Eyes countries. Only time will tell if we’ll be talking about Six Eyes instead of Five Eyes soon.
Conclusion
The Five Eyes is the most powerful surveillance alliance in the world. While it arguably works well to protect its member countries (USA, UK, Canada, Australia, and New Zealand), it makes those countries less than ideal jurisdictions for pro-privacy companies and products.
Ultimately, we also need to acknowledge that everyone has different needs, use cases, and threat models. This means that selecting products and services is a very subjective matter, and only you can find the best fit for your needs.
Good luck and stay safe!
This guide on the 5 Eyes, 9 Eyes, and 14 Eyes was revised and updated on April 27, 2024.

You are wrong about the french private search engine “Qwant”.
It is not private at all but powered by Bing…
Yes we noted here that Qwant uses Bing search results, but that is not at all uncommon for private search engines.
Thank you so much Sven for your excellent work and most helpful Intel. I am an author and writer, having battled against the globalist cabal since 2013 following the Cyrus bank robbery, which initiated my book, The Financial Jigsaw Parts 1 & 2 (Part 2 is being serialised at present). All my work is available FOC (no copyright), dating back to 2018: https://www.theburningplatform.com/author/austrian-peter/
I take the view that the surveillance industry is welcome to read my work – it helps distribution – after all, there are White Hats within all these industries. I do use a German ISP – IONOS which I assume is secure, but all these guys leak one way or another IMHO. Have you an opinion on this ISP, please?
Best regards
AP
Hi Austrian Peter, sorry I do not have much of an opinion on ISPs, other than the fact that they have a very bad track record of collecting data for various agencies, at least over here in the US. I would just assume your ISP is logging your browsing activity, and act accordingly with a VPN, unless you want them to see what you’re up to online.
Dear Mr. Sven Taylor,
Just writing because I wanted to make sure for copyright purposes you got permission to use the Washington Post slide.
Thanks,
John
Insulting Consulting
Hi John, the original source of the image was Wikipedia. I have now updated the image and added the source as Wikipedia. Thanks
How secure is the search facility within Surfshark, please?
Searx (open source, no jurisdiction) (really bad)
MetaGer (Germany)
Swisscows (Switzerland) (an extremely vicious fake privacy search engine that blocks Tor and other ‘safer’ browsers).
Qwant (France)
duck and mojeek, same with duck being better technically.
All compromised, all censoring search results like google, yahoo, bing (because based on them), all heavily biased, none of them really pruvacy respectful or safe.
You’d be safer using a Russian or Indian search engine than any western one to circumvent fake news, censorship and western surveillance.
You know it’s true
Even Startpage is into some dishonest bull**it, despite being one of the best UX and maybe even privacy designs around.
Is there a reason for leaving out Mullvad VPN? They are usually highly regarded…
It’ll be added with the next update. We have it on our best VPN list here.
Is https://cock.li good email?
it’s almost impossible to avoid 5-9-14 eyes… 75% of internet traffic goes to or through the USA. unfortunately!!!!
for B.
you should use both protonmail and protonvpn
Protonmail not private anymore so all their services. Strange fact. Protonmail uses java on Tor. For what ?
Duck Duck GO isnt safe or secure. there are back end ties that are very shady , how can you have them in this list?
please define “very shady back end ties”
They made an agreement with Microsoft to give them windows users data.
What are the Chinese, Russian, or Iranian alternatives? Clearly the only countries that might be trusted.
No, it’s not clear at all: There is nothing obvious or logical about your conclusion. How many countries exist, in your estimation? And what are you going to do when 90 percent of the world’s internet traffic is sold?
https://www.vice.com/en/article/y3pnkw/us-military-bought-mass-monitoring-augury-team-cymru-browsing-email-data
How can you trust China when all they do is tightly surveil: their own citizens and now all over the world? The issues with Tick Tock were the most recent I’ve heard about.
The wotls divided : USA and their allies, China, Russia – everybody put surveilance. It is not about security. It is about control. (Ed Snowden).
The world is divided : USA and their allies, China, Russia – everybody put surveilance. It is not about security. It is about control. (Ed Snowden).
Are NordVPN (with its own page on the World Economic Forum’s homepage) and ExpressVPN (with its purchase by Kape seen here: https://www.timesofisrael.com/israeli-cybersecurity-firm-buys-expressvpn-for-close-to-1b/) still reliable guards of our privacy? Yes they are large, have a lot of servers, and have polished user interfaces but these aren’t comforting ties for companies you do business with to protect cyberprivacy.
Indeed!
NordVPN – the US based business? Go figure how that can lawfully evade the Five Eyes.
NordVPN is legally based in Panama, with much of the team is also in Lithuania. Nothing about Nord is “US based”.
I’m looking to start using a Gmail and G-suite alternative. My question is the following: If I start using ProtonMail does it make sense to also buy a subscription to SurfShark, or should I just use ProtonVPN?
You’d probably be fine with either option – it all comes down to preferences.
I have read through many of the linked articles at RestorePrivacy website. I noticed that when you mention countries which are more, or less, secure/advantageous than others when choosing a VPN, there is no mention of Ireland. When you use the term “United Kingdom” or “UK”, are you including Ireland under that umbrella, even though they are not part of the UK?
Thanks,
T.D.
Proton, although on the surface seemed like a great anonymizer….actually was forced by the swiss govt to give the identity of an activist who using proton….
Somewhere between 2020 and now the swiss revoked their neutral status as a nation……so they are not as squeaky clean as you may think…
C that _is not_ true. Please be accurate, as your comments do not help people progress their privacy.
Proton did not reveal an identity, they were forced by Swiss courts to log a specific users activity whose location and name were already know. And handover messages.
Proton could not and did not hand over any messages as they are technically unable.
You can read clarification here:
https://proton.me/blog/climate-activist-arrest
How about [https://privatevpn.com/features/p2p-vpn] ? They are based in Sweden. They seem to be really good and do not require anything from Microsucks. They work with Linux, smart phones, etc. Sadly, I do not see anything mentioning audits. Here is their FAQ: [https://privatevpn.com/support/faq/]
UPDATE for readers:
NordVPN is running a Christmas sale with 3 months free.
DuckDuckGo not recommended, because the default settings are too tracking-centric.
If you look at “all settings”, you will find that one quarter of the total of 23 settings, needs to be toggled off, in order for it to do no analytics or tracking of what you’re doing.
Granted, ddg needs to finance themselves somehow.
But it’s merely replacing trackers by becoming the tracker.
You security folks all lulling users into a false sense of security by recommending it, and making simple statements that it’s safe, implying out of the box, is wrong.
I read in your article that mass surveillance would be to protect against terrorism but this represents 15% of surveillance activities, the rest corresponds to economic espionage. I found this information on the following link :
https://fr.wikipedia.org/wiki/R%C3%A9v%C3%A9lations_d'Edward_Snowden
DuckDuckGo is owned by Google. How can you say it is even remotely private?
No, DuckDuckGo is not owned by Google.
Why does “a duck duck go” search sometimes throw me to a YouTube or Google search engine?
You are penning from a point of ignorance. Do your research on Search Engines. Search Engines are, basically, built two different “ways”, albeit, not a definitive: “pure” and “aggregator”. “Pure” are software-built “from scratch” and are wholly proprietery engines. “Aggregators” simply are software-code-written to search other existing Search Engines anonymously for you and return the hits/results to you, basically providing anonymous proxy searching services to/for you. DDG is an “AGGREGATOR” and thus searches GOOGLE anonymously FOR you and returns those results TO you. YOUTUBE is owned by GOOGLE and that is why you get those results. Do your own research and stop looking for quick answers from others.
DuckDuckGo is hosted on YAHOO! servers. This presents a concern.
CTemplar is no more. So sad.
Theres a guy who got his own ISP, wonder how far hes from true person… The tighter crazy internet laws the closer internet to its collapse, then what?… forced grafen oxide nanochips injected into all sheeple. The idea of a spinning ball thru vacuum works well for more then 100s of years.
If FBI or MI5 or some official agency or some state appointed official agency is scanning my emails and if I have nothing to hide then I have nothing to worry.
What bothers me is that crooks don’t hack my system and use that data for misrepresentation in banks, credit card companies, stores etc.
5 eyes or 15 eyes, how much can a common individual fight back. He / She is worried on a daily basis about his /her job / business / limited financial assets / kids / medical problems / life.
Governments and those obsessed with power love people with your attitude…
nothing to hide what does it matter???
eventually things change and you do become the enemy and everything you did is still there… it has nothing to do with what you think is right and wrong. They will come for you anyway.
Even hiding is a pipe dream even a VPN blah blah blah… we let them go to far its in everything. Only chance you have is a cave and hunting off grid outside that they can get anything from anywhere… NSA already caught doing it to basically every world leader.
Absolutely Joe how true.
Glad I am of my latter years and not be involved in the train crash coming, engineered by the WEF
At this point if I hear anyone say they listen to the WEF then I just leave the conversation mentally.
You are making the same mistake as most people. Crooks CAN and DO work for FBI, CIA, MI5, and any “official” state agency! Just because you CAN’T THINK about why one would target you, does not stop that person from having a reason and capability to target you. READ world history. States are very OFTEN the malicious foes of good people.
You have nothing to worry about because you are a nobody. The day you start speaking against their corruption, you will realize the true need for privacy oriented services. Just look up about Mansi Soni Case.
“If I have nothing to hide then I have nothing to worry.” Unfortunately, that is dangerously, tragically, catastrophically false. If you read and watch enough law enforcement activity, you’ll soon discover that LEOs are convinced of their “instincts,” and are very often wrong. Their imagination and preconceived notions lead them to read illegal activity into innocent behavior, and their confirmation bias takes over from there. Far too many innocent people have suffered life-altering prosecution, incarceration, and even death, because some LEO or other thought he could see nefarious behavior where none actually existed. That is why, in the United States at least, LEOs are legally required to advise suspects of their right to remain silent, and lawyers advise people to do so. Having a secure and private VPN is the digital equivalent of choosing to remain silent. It doesn’t mean you’re doing anything wrong. It just means you’re rightfully concerned about some government agent *thinking* you’re doing something wrong, and then sticking to his guns despite evidence to the contrary.
In the study of logic we learn that he who proposes a piece of logic, an argument, must be the one to justify that with evidence. Especially when it comes to Government spying in a democracy. This never, EVER, happened. Just fear, emotion, and in the case of the cu*t Australians voting to backdoor encryption, no more decisive argument won it than: “let’s just get it passed before Christmas”. The anti-demcratic scumbags. However there IS a lot of evidence for the surveillance powers being abused. It’s called Edward Snowden and the contents of Wikileaks. Which Julian Assange is in prison for rightfully enabling journalists to see this and bring it to public attention. This is 20 years after Duncan Campbell from Scotland started writing publicly about ECHELON and CARNIVORE and questioning why the NSA had staff at Menwith Hill on a USAF base leased from the RAF I believe.
Meanwhile, bad things keep happening to the West and our quality of life lowers more each year. Coincidence? Who is the REAL traitor?
On VPNs, an absolute brain-to-brick-wall thing I’ve been coming up against, over and over and over and over again, is the fact that every single damned one of them – with their ostensible goal being privacy, recall – requires that the user download and install the latest malware-in-the-OS-code crap from Microsoft, just to install the software to run the VPN at all.
Given that Microsoft’s Orwell 10 requires every user, right at Square One, to acquiesce to 100% monitoring right down to keystrokes – yes indeedy folks, a keylogger written right into the OS code itself – requiring that users have that… thing running their systems is kinda-sorta a massive short-circuit to the whole “privacy” thingy, isn’t it? If I’m forced to expose my nethers to the tender mercies of Microsoft, Ink just to get the damned thing running, what’s the point?
And the protestation “Oh, in Orwell 10 you can disable those ‘features,'” is like someone selling you a house, keeping a key to the front door, and informing you “Oh, well I *promise* not to go in while you’re gone, if you tell me not to. Have a nice day.” Do *you* trust your email correspondence, your bank card numbers, your medical data, etc. to the idea that all of those little dweebs in their cubicles in Redmond, WA are just perfect little angels who would never ever ever do anything untoward with your data? *I* don’t.
[And with computers being one of the most gargantuan market sectors on Earth over the last two decades, I’m really wondering why we still, as of 2022, have exactly two (2) OS manufacturers, when there should be hundreds, locked in feverish competition. Ok, three if you include Linux. The product is “too complex?” So are insurance policies, oil refineries, microprocessors, cars, symphonies, airplanes, drugs, etc., and there are dozens of manufacturers of each. So… a “No you can’t” edict from the NSA or some other gov’t agency, ’cause they don’t care to be forced into forcing more companies to write their backdoors into their code? But… three. Why? But I digress.]
So anyway, is there anybody out there who produces a VPN that will install and run independently of the Microsoft Borg? I had Anonymizer for years until it abruptly got shut down, and every VPN subsequent to that has apparently become a Microsoft whore as an unquestioned, reflexive thing, maybe like a sneeze.
Just configure the VPN on your router so all of your network traffic is getting sent to the VPN proxy. If you want need some traffic to not be in the VPN then find a provider that supports split-tunnel VPN. Such as your work laptop needing a consistent public IP, that is riding a end to end VPN back to your company anyways. Check out pfSense or OpenWrt for router/firewall firmware. Also if you don’t giant OPSEC hazzard that is windows, then consider moving over to a Linux based operating system.
Not sure what you’re talking about. It’s not the VPNs’ fault that Smallandlimp has become yet another spying service. I’ve been running PIA VPN on Linux Mint for several months with no problems, and there are at least a few other VPNs who have software for Linux. Macoroni
This made me laugh, especially the “Microsoft Window’s Orwell 10”
part lol. I shared it w a buddy.
But ya you’re spot on👌
Now remove Windoze 10 and remind yourself that the Intel ME is both closed-source and still running outside of your control making a mere keylogger at OS level look amateur. AMD are idiots for not refusing to make an alternative without similar backdoor. Suggesting they compete or are coerced by the NSA and such.
Any comment on VPN Unlimited?
Here is the VPN Unlimited review.
Hi thank you so much for this article
what about trusted crypto wallets?
thanks
What is the point of crypto currency. It is a nothing like the currency we all use, based on nothing.
When are people going to wake up to the fact that currency is on borrowed time to be replaced by digital currency to be replaced by social credits to be replaced by Orwellian total control!!!
At least I hope VPNs keep me hidden for as long as possible so I can just live my life and be left alone!!!
I thought it would take 20 – 50 years but with the manufactured non existent global pandemic and the trashing of western economies and a control power grab under the green agendas (WEF and WHO) I recon this is 10 years away.
Back to bartering , paying with tangible assets (gold etc) and living in a cave if you want to escape this Totalitarian world coming up.
I am just glad I will be in my box by then!!!!!!
A reminder there is a very obvious, yet heavily over looked country that should be in the ‘5 eyes.’ But the 5 eyes are closed and busy doing business with them.
That would be israel
based on what you write so?
Intrestingly, my non-solicited adverts that appear on my mobile are in Hebrew. I live in Cyprus and I strongly suspect that Israel agencies have some Cyprus state condoned access to Cyprus signals traffic. I never use Israeli or Cyprus VPN located servers.
Hello. Question.
The article suggests at times in avoiding Five Eyes. Does that not include the other Eyes since they both also contain Five, or is it just okay to avoid Five but still go with 9 and 14 despite them containing 5?
Thanks.
I recommend avoiding 5 Eyes: US, UK, Australia, Canada, and New Zealand. Based on my research, the other “Eyes” are not concerning. But it all depends on your threat model and the adversaries you are trying to avoid.
Thank you very much. This opens me up on trying some of the more secure email services then that are in the 9 and 14 like Posteo or Mailfence. This just-not-the-5s opens me up to trying to find a new provider over Gmail that gives me what I need.
Thank you for your comments.
Hello,
I am curious — if we live in a 14-Eyes country, and this means the GOV agencies can monitor the inputs of data going over our VPN connections and then the server connection is also in a cooperating country monitoring the output — couldn’t that mean it would be easy to analyze the traffic and identify the user?
This is what I have read on some places and am wondering about this “attack”?
— Thanks
No, VPN servers are encrypted and under the control of the VPN itself, even if they sit in a data center in a “14 Eyes” country, that doesn’t matter. Unless of course the VPN has botched their server security, or left the server unencrypted, the server will be secure and user data will not be available, even if the server gets seized. There was a case last year when Windscribe VPN left a server in Ukraine unencrypted and it got seized. This was an example of bad security and a VPN that intentionally chose not to follow “industry best practices” and left its server (and users) exposed. We do not recommend Windscribe VPN.
The biggest threat to VPN users is when the VPN itself is forced to log users. As pointed out above, this happened with IPVanish when the US forced the “no logs” VPN to log customers for the FBI — and this has also happened with other US-based VPN services and email providers, going back to at least 2013. This is why we emphasize the importance of jurisdiction (outside 5 Eyes) when choosing a VPN service.
Windscribe being, what, Canadian was a non-starter for jurisdictional trust, unlike the people at grassroots level which is a different matter.
Thanks for the list. I hear the terms thrown around a lot but never gone into in depth. Security is important to me, I’m tired of big corporations and big government spying on my and watching my every move and though. Especially dangerous in today’s society where you can get canceled for the comments of 10+ years ago or arrested for just being in the vicinity of a crime when it goes down. Google is by far my biggest concern however, their spyware is so baked into everything they create and they’re planted themselves in the schools now. Kids don’t have textbooks anymore, now they have Chromebooks that require them to have google accounts in order to use, and the teachers require them to have their real info on those accounts. It’s very scary where we are heading as a society now that big brother is inserted right between kids and their education, all the way from preschool.
This worry me a lot as well. DK here. Cheap Chromebooks and edu suite for “free”. We are seen as weird people, it feels like. What do you mean by real info? Kids have linux on their pc’s. Browser and search engines updated from this page 🙂 we talk a lot about data, but difficult, because they want to play roblox etc and have to use drive in school. No education for kids or teachers. 9 year old had to tell that s in https is secure, not site. I don’t know what to do. I’m just a normal user as well and there are so many questions i want to ask.
Are there any webmail services search engines outside the 9 eyes?! except swisscows
I do not see China or Russia mentioned anywhere. I would think they are as bad as any of the 5 Eyes.
Hi Sven,
I enjoy your site and check it often to stay on top of security and privacy news.
I thought you might be interested in this story: [https://www.lifesitenews.com/news/canadian-ethics-committee-votes-10-0-to-investigate-trudeau-governments-spying-on-33-million-cell-phone-users/]
Concrete proof of government spying!
Thanks for sharing, and not surprising.
Thoughts on expressVPN? I need a very fast VPN, and I don’t know if any of these non-five-eye ones meet the standard like express does. When I set it up, I researched and found they had been tested and validated to meet strict privacy requirements by third parties.
Just curious if you have looked into the validity of third party validation, high speed consideration from non five eye providers, thoughts in general.
Thank you for the article.
Hey there, yes we have done lots of speed tests on a 500 Mbps line, and the fastest by far was NordVPN. I have also seen a few Youtubers post speed test videos of Nord hitting speeds over 800 Mbps with some US servers (tested on a fiber connection). And for comparison, NordVPN has also consistently outperformed ExpressVPN in our head-to-head speed tests.
For the fastest speeds, you should:
1) Use a good VPN provider.
2) Use the WireGuard VPN protocol (this is NOT supported by ExpressVPN, because they use Lightway)
3) Connect to a nearby server
My recommendation would be NordVPN. It has also passed no logs VPN audits and third-party security audits conducted by Versprite in 2020 and 2021.
Surfshark is another decent option that supports WireGuard, but it’s not quite as fast as NordVPN. Either way, you’ll have a 30 day refund window to test it out and see if the VPN gives you the speeds you need. And here’s a link for 74% off NordVPN.