Both Tor and VPNs are privacy tools with pros and cons, which we’ll closely examine in this VPN vs Tor guide. So which one of these tools is best for you? That depends on your own unique needs and threat model.
Helping you select the best option for your use case is the goal of this guide. Here are the areas we’re going to examine in comparing Tor vs VPN:
- Speed
- Encryption and security
- Anonymity
- Cost
- Browsing, streaming, and torrenting
- Ease of use
- Versatility
- Trustworthiness
1. VPN vs Tor speeds
With speeds, there is a huge difference between VPNs and Tor.
VPN: With VPNs, I can often get around 500 to 750 Mbps Mbps when using a good VPN service. VPN performance has gotten a major boost in the past few years thanks to the WireGuard VPN protocol. WireGuard offers faster speeds, better reliability, and upgraded encryption. Below is a speed test with NordVPN using the WireGuard VPN protocol with a US server, hitting speeds over 750 Mbps:
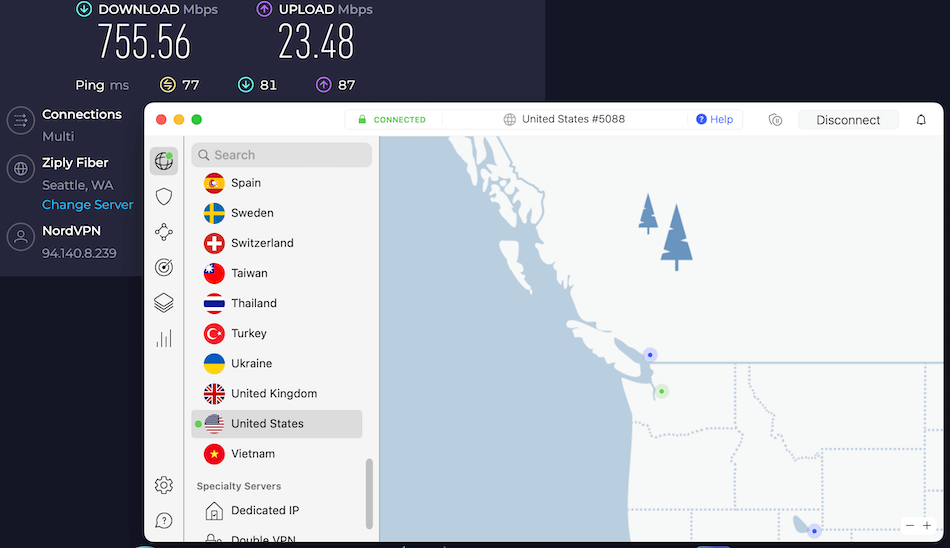
With speeds exceeding 750 Mbps, NordVPN is the fastest VPN we have tested so far.
Now let’s look at Tor.
Tor: Although Tor speeds have slightly improved over the years, it is still much slower than VPNs. Tor suffers from high latency because your traffic is routed over three relays. In testing Tor, my speeds average around 5 Mbps, but I can sometimes get 9-10 Mbps if the relays are good, such as below.
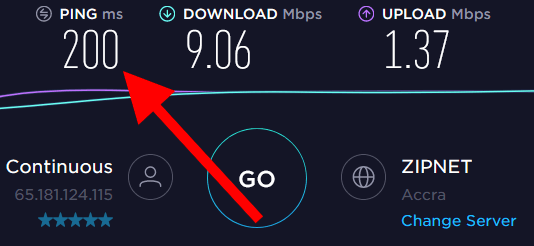
With this speed comparison, the VPN was almost 50 times faster than Tor. Also notice above the latency is very high with the Tor network. This results in sluggish performance and websites being slower to load. Streaming HD videos will also be challenging.
VPNs easily wins the speed category and are much faster than Tor.
Speed winner: VPN
2. Encryption and security: VPN vs Tor
Tor: Tor uses a layered system of encryption that incorporates perfect forward secrecy. Traffic is passed through three relays, all of which are encrypted:
- Guard relay – The first relay in the circuit, which can see your IP address.
- Middle relay
- Exit relay – The last relay in the circuit where your traffic exits onto the regular (unencrypted) internet. A malicious exit relay could potentially see your data and modify traffic.
By default, traffic with Tor is routed through these three hops before exiting the Tor network circuit.
With Tor, encryption only works within the browser. This is a huge drawback in comparison to VPNs.
By only encrypting browser traffic, everything else on your operating system remains exposed and could reveal your real IP address and location to third parties. This means that documents, torrent clients, updates, etc. are exposing your traffic and real IP address to the unencrypted internet. You don’t have this problem with a good VPN.
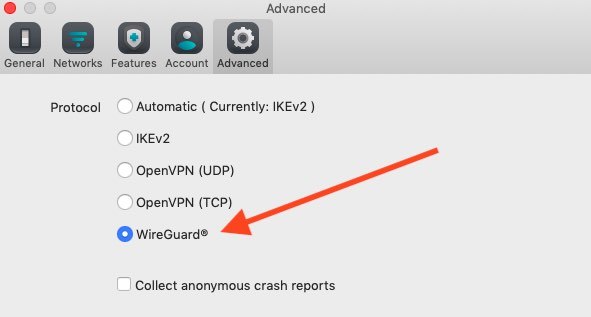
VPN: Most VPNs secure traffic via OpenVPN or IPSec protocols with the connection also being encrypted with perfect forward secrecy. OpenVPN is the most common protocol, usually secured with an AES 256-bit cipher, which is universally considered very secure. WireGuard is also entering the scene, which uses a ChaCha20 cipher. Most VPNs allow you to easily select the ideal VPN protocol (and corresponding encryption cipher) directly in the VPN application. Here is an example of protocol selection with Surfshark VPN:
Most VPN providers only route traffic through one hop. However, like Tor, there are a few multi-hop VPN services, which can route traffic over 2-4 hops. Two examples of this are with NordVPN and Surfshark that offer double-VPN servers.
There are also VPNs that have VPN servers that exit onto the Tor network, also known as “Tor-over-VPN” servers. We see these with both ProtonVPN and NordVPN.
Unlike with Tor, a VPN encrypts all traffic on your operating system. This offers a higher level of protection since it is not restricted to only a browser.
Encryption winner: VPN
3. Anonymity: VPN vs Tor
Anonymity closely ties in to the previous section on security and how strong the underlying encryption is against exploits that could de-anonymize the user.
Tor: With Tor, there have been various cases over the years showing that it can be exploited. Specifically, a court case in 2017 proved the FBI can de-anonymize Tor users and determine their real IP address and activities:
In this case, the FBI managed to breach the anonymity Tor promises and the means used to collect the evidence from the dark web make up a sensitive matter. The technique is valuable to the FBI, so the government would rather compromise this case rather than release the source code it used.
There is also other evidence illustrating how government actors can identify Tor users, thereby rendering Tor useless as a tool for anonymity.
Tor has been proven to be vulnerable to various exploits over the years.
VPN: Unlike with Tor, I have not seen any evidence of governments being able to break strong, correctly-configured VPN encryption, such as OpenVPN with an AES-256 cipher. There is evidence that weaker VPN protocols, such as IPSec and PPTP, are vulnerable to exploits, but OpenVPN and WireGuard appear to remain secure when implemented correctly.
When governments have targeted specific VPN users, they have done so not by cracking the encryption, but by pressuring the VPN service to log specific users. Here are a few examples we’ve covered here on Restore Privacy:
- FBI pressured IPVanish into logging data of a specific user for a criminal case.
- FBI pressured PureVPN into logging data of a specific user for a cyberstalking case.
These logging cases illustrate the importance of selecting a trustworthy service, preferably a no logs VPN, that operates in a safe jurisdiction.
Exploitation in the wild (the big difference)
This is the big difference between Tor and VPN is how each has been exploited. With Tor, the FBI is able to break/exploit Tor and identify Tor users. (Their methods for doing this are sometimes not clear, and in some cases “classified” — but there are new cases and examples that emerge every few years.)
With VPNs, the FBI could not break the encryption, but instead had to pressure the VPN service itself to target a specific user and log data. The solution to this problem is to use a trustworthy VPN operating in a safe privacy jurisdiction.
Anonymity winner: VPN
4. Cost: VPN vs Tor
Cost may be a deciding factor for some people.
Tor: One big advantage with Tor is that it’s free. The Tor Project is a non-profit funded by various sources, but mostly the US government (we’ll discuss this more below).
VPN: One drawback of VPNs is that they can be rather expensive.
Costs can vary from about $2 per month all the way up to $10 per month. On a positive note, there are also some cheap VPN services that are more affordable. There are also free VPN apps available, but studies show these to be bad choices that are often riddled with flaws and adware.
Cost winner: Tor
5. Browsing, streaming, and torrenting: Tor vs VPN
I’ve been testing VPNs and Tor for 6+ years and here’s my impression.
Tor: When using Tor, you will definitely notice a performance tradeoff. Latency (ping) will be much higher and so will your bandwidth speeds.
- Browsing: Regular browsing will be more sluggish as traffic is routed through three Tor network relays.
- Streaming: Due to high latency and slow speeds, streaming will not work well. Tor has gotten faster over the years, but streaming videos is still problematic, especially in high definition.
- Torrenting: You should not use Tor for torrenting, as stated by the Tor Project. Even if you configured a torrent client to route traffic through the Tor network, torrent speeds would be horrible. (Better to use a VPN for torrenting instead.)
Overall, Tor is best used for browsing, not streaming or torrenting. But even with regular browsing, the Tor network can be sluggish.
VPN: If you are using a good VPN, you should not notice any negligible difference in relation to your non-VPN speeds.
- Browsing: Browsing should be just as fast (little to no difference).
- Streaming: Streaming should also be good (I regularly stream Netflix with a VPN).
- Torrenting: VPNs may decrease torrenting speed somewhat, but it shouldn’t be huge. And you should always use a good VPN for torrenting due to copyright issues.
Browsing, streaming, and torrenting winner: VPN
6. Ease of use: Tor vs VPN
Both Tor and VPNs are easy to use.
Tor: As long as you are using the unmodified Tor browser, then Tor is easy to setup and use.
- Download the Tor browser bundle.
- Click the button to connect to the Tor network.
You can also connect to the Tor network through the Brave browser.
However, manually configuring Tor on another browser can be challenging. Setting up apps to go through the Tor network can also be difficult. And you may run into issues when trying to use Tor on mobile devices, but there are options for that as well.
VPN: VPNs are also easy to use.
- Sign up for a VPN subscription.
- Download the VPN client for your device.
- Connect to a VPN server.
Below I’m connected to a double-VPN server configuration with NordVPN:
In some cases, setup can be slightly more complex, such as installing VPNs on a router or manually configuring a VPN on your operating system (such as with Linux). However, most of the popular VPN services, such as ExpressVPN and NordVPN, offer apps that are very easy to use.
Ease of use winner: Tie (both are easy to use)
7. Versatility: Tor vs VPN
In the context of versatility, I’m looking at the ability to adapt or be used for different functions.
VPN: VPNs can be used in many different ways, aside from simply encrypting traffic on a desktop computer:
- Most operating systems have VPN functionality built in, such as with the IPSec or WireGuard protocols.
- VPNs can be easily used on mobile devices with various protocols that are better adapted to intermittent connectivity. For example, WireGuard is ideal for mobile use.
- VPNs can be combined with different features. For example, some VPNs have ad-blocking features. For example, we see this with both CyberGhost and NordVPN.
- There are a handful of different VPN protocols available for different use cases, with new ones in development, as we discussed above.
Tor: Tor is not as versatile as VPNs, although it still can be tweaked and configured to a degree.
Tor is not built in to major operating systems, such as Windows, Mac OS, Android, or iOS, but there are a few Linux operating systems that incorporate Tor (see Whonix and Tails).
Versatility winner: VPN
In comparison to Tor, VPNs are more versatile and more comparable (with various devices and operating systems).
8. Trustworthiness: Tor vs VPN
Trust is a major factor when selecting privacy tools, but it’s also subjective. Nonetheless, here’s my take:
Tor: While some in the privacy community consider Tor to be trustworthy, there are many red flags to consider. Here’s an overview of my findings on Tor that raise questions about its trustworthiness:
- Tor is compromised (and not anonymous). There have been various examples and court cases over the past few years confirming this fact. The FBI (and presumably other government agencies) can now de-anonymize Tor users.
- Tor developers are cooperating with US government agencies. This is another bombshell that was uncovered by a journalist who sifted through thousands of pages of FOIA requests. In one example, Tor developers tipped off US government agents about Tor vulnerabilities that could be exploited to de-anonymize users.
- No warrant is necessary to spy on Tor users. A judge ruled that the US government is perfectly lawful in exploiting Tor to uncover Tor users’ real IP addresses.
- Tor was created by the US government (contractors with the Naval Research Lab and DARPA).
- Tor is still funded by the US government to the tune of millions of dollars.
- Tor is a tool for the US government, specifically the military and intelligence branches. They need regular users on the Tor network so these agents can be camouflaged (as Tor developers have explained).
- Anybody can operate Tor nodes, including hackers, spies, and government agencies.
- Malicious Tor nodes do exist. One academic study found over 100 malicious Tor relays.
On a positive note, Tor is open source and the code can be examined by anyone. This, however, does not necessarily make it “secure” or impervious to exploits.
VPN: VPNs are also not a silver bullet in the trust category.
- There have been a few VPNs caught lying about logs, such as PureVPN and also IPVanish.
- Free VPN services are fraught with controversy, including hidden malware, ads, and data collection. (But this is true of many free products today.)
- Some VPNs are also flawed and may leak IP addresses and DNS requests. These leaks can be fixed via firewall rules (or just using a good VPN service that doesn’t leak).
OpenVPN, the standard protocol used by most VPN services, is open source and has been publicly audited. There are also various third-party open source VPN apps, such as Tunnelblick (Mac OS) and OpenVPN GUI (Windows).
Some VPNs have undergone third-party security audits. See for example with ExpressVPN, ProtonVPN, TunnelBear and NordVPN.
Source of funding
Sources of funding may also influence trustworthiness.
VPN: Paying subscribers are the source of funding for VPN companies, which are generally private businesses. If VPN services do not do a good job for their subscriber base, they will go out of business.
Tor: Various branches of US government (and their subsidiaries) are the largest funding source of Tor, having contributed millions of dollars to the Tor Project over the years.
When Tor was ready for deployment, the Naval Research Lab released it under an open source license with guidance coming from the Electronic Frontier Foundation. Even today, the US government agencies, such as DARPA, State Department, and National Science Foundation remain large sponsors of Tor.
The Tor project admits that donors will get to “influence the direction of our research and development.” Therefore according to the Tor Project, the US government is influencing the research and development of Tor.
Distribution of trust
VPN: With VPNs, you can distribute trust by using more than one VPN at the same time (chaining VPN services). You can easily do this by using VPN1 on your router and VPN2 on your computer. You can also chain two or more VPNs using virtual machines. Most people, however, do not chain VPNs and therefore all trust falls on the VPN provider (in most cases).
To further protect your anonymity with VPNs, you can:
- Chain VPNs and effectively distribute trust across different VPN services. In this scenario, VPN1 could see your IP address and VPN2 could see your traffic, but neither VPN could see the full picture.
- Pay for the VPN anonymously thereby ensuring there is no “money trail” (Bitcoin, cryptocurrencies, or with gift cards purchased with cash). The need to pay for VPNs anonymously, however, is overblown as this has zero bearing on the effectiveness, security, or encryption of the VPN – even if your adversary knows what VPN you are using.
- Use only verified no-logs VPN services
Tor: The problem with Tor is that it is an entire ecosystem you must trust. The ecosystem itself is a single point of failure. And even if you are relaying traffic over different hops, you are still trusting one system, and that doesn’t always work.
The core system that manages the code base, relays, and onion servers must be all trusted by the Tor user. You also need to trust that relay operators, through which your traffic is running, are being honest, which is not always the case.
Unfortunately, there is no vetting mechanism for Tor node operators, which has proven to be a problem (malicious nodes, snooping nodes, etc.)
Trust winner: VPN
Conclusion: Are VPNs or Tor better?
As noted in the introduction, both Tor and VPNs are privacy tools with pros and cons. You should select the best fit for your unique situation.
For most users, a good VPN will probably be the best option because it will provide a high level of privacy and security without a negligible loss in performance. VPNs can also be used easily on a large array of devices and operating systems, with various VPN protocols and configuration options available. The main thing to keep in mind is finding a trustworthy VPN provider that offers the features and security you need.
Tor may be a good choice for certain use cases, especially if you are short on funds and need a free tool for specific tasks. But don’t forget, only traffic within the browser is getting encrypted — everything else remains exposed.
You can also combine Tor with VPNs. We discuss this in our main guide on Tor here.
Further Reading:
Is Tor Trustworthy and Safe? (here on RestorePrivacy)
Tor and its Discontents: Problems with Tor Usage as Panacea
Users Get Routed: Traffic Correlation on Tor by Realistic Adversaries
Tor network exit nodes found to be sniffing passing traffic
On the Effectiveness of Traffic Analysis Against Anonymity Networks Using Flow Records
Judge confirms what many suspected: Feds hired CMU to break Tor
This VPN vs Tor comparison was last updated on May 8, 2024.

So, what’s your take on this specific section of the page from Whonix that argues why you shouldn’t use a VPN with Whonix (which, in turn, uses Tor as its browser): https://www.whonix.org/wiki/FAQ#Should_I_Set_Up_a_VPN_with_Whonix?
I don’t understand a lot of the technical justifications regarding this (such as the accusation of traffic fingerprinting), but if I understand your reviews of NordVPN, for example (which I use), it sounds like Nord prevents this.
I agree.
Nope, not BS. For Huckle, It was good detective work, no techno-magic; nothing to do with Javascript.
Officers with Task Force Argos in Australia knew the creator of the site used an unusual greeting – the word “hiyas”. After exhaustively trawling chatrooms and forums in the open internet, they found a Facebook page of a man who used the same greeting. Although the Facebook page was fake, they identified a picture of a vehicle and that led them to a man called Shannon McCoole – a childcare worker in Adelaide. When officers went through his door, he was actually online running the site.
They took detailed photographs of McCoole’s hands. On his finger was a freckly which matched exactly one seen in many of the images of abuse. (from From http://www.preda.org/2016/how-child-abuser-richard-huckle-was-caught.)
Tor has not been cracked. But like a VPN, it can be bypassed. People using it have compromised themselves by their behaviors outside, or by investigators comparing on-line accounts to when a suspect’s IP is active, or by using the same phone number on another account, etc. Do your research.
This article seems a bit slanted against TOR. True, there are situations where a VPN is satisfactory, and a VPN will encrypt other internet traffic from you PC which passes outside of the browser, but if your are stealing documents from the government or your employer and leaking them, or your government doesn’t allow free speech, and you don’t like prison, the don’t trust ANY VPN to keep you safe when they are presented with a subpoena. Also, I don’t agree that configuring a VPN is as easy as using TOR. For Browser activity, that’s remains the most secure.