
When it comes to VPN logs, there’s a lot of confusion.
Countless VPN services are making the “no logs” claim for marketing purposes, but in reality, they are keeping some form of logs.
Even worse, we have seen at least three different “no logs” VPNs that were caught logging users:
- Released court documents proved that PureVPN was logging its users for the FBI, all while claiming to be a “zero logs” VPN service.
- IPVanish also claimed to be a “no logs VPN” — but court documents revealed that IPVanish was logging users at the request of US government officials.
- HideMyAss VPN was also found to be logging users for a US criminal case involving hacking. The HideMyAss users went to jail and learned that HideMyAss will log your ass.
In this guide we’ll cover the different types of VPN logs, the reasons for keeping logs, and what you can do to further protect your online privacy.
But first, why should you care about VPN logs? While there are some people who use a VPN for streaming only and only want to unblock content, most people care about their online privacy. Examining a VPN service’s logging policies will help to determine how well the VPN does in the privacy category.
Furthermore, if your VPN is logging data, then this data could also be lost, hacked, leaked online, or even end up for sale on some Dark Web forum. So the savvy VPN user will carefully consider a VPN’s logging policies before signing up. So let’s take a closer look…
Types of VPN logs
There are three different types of VPN logs (also discussed in our main VPN guide).
Usage (browsing) logs – These logs basically include online activity: browsing history, connection times, IP addresses, metadata, etc. From a privacy standpoint, you should avoid any VPN that collects usage data. Most of the VPN services that are collecting usage logs are free VPN apps, which are basically spyware. The data they collect is then sold to third parties, thereby monitoring the “free VPN” service. There have been accusations of this type of logging with some major VPN brands, as described in our Hotspot Shield review.
Connection logs – Connection logs typically include dates, times, connection data, and sometimes IP addresses. Typically this data is used for optimizing the VPN network and potentially dealing with user problems or terms of use issues, such as using a VPN for torrenting, illegal activities, etc.
While basic connection logs are not necessarily a problem, there are some VPNs that keep connection logs, while falsely claiming to be a “no logs” service.
No logs – No logs simply means the VPN service is not keeping any logs. Having a truly no logs policy can be difficult to implement while at the same time enforcing restrictions, such as device connections or bandwidth. This is especially the case when VPNs need to enforce restrictions such as bandwidth or the number of devices being used per subscription.
We have also learned that VPNs may require logging with some VPN protocols, such as the WireGuard VPN protocol. However, as we noted in the NordVPN vs Surfshark comparison, both of these VPNs use a Double NAT system with WireGuard, thus allowing them to not keep any logs or connection data.
The two most popular no logs VPNs right now are NordVPN and ExpressVPN.
Reasons for logging
There are many reasons for maintaining some form of logs – and they are not necessarily bad.
1. Limiting the number of devices
One of the biggest reasons for maintaining logs is to limit the number of devices used with a subscription. Nearly every VPN imposes limits (3, 5, 6…) on the number of simultaneous connections that can be used with a subscription. Enforcing connection and device limitations may require some form of logging (at least when the user is connected to the service).
Exactly how the VPN service is enforcing connection restrictions while still being “no logs” is a question that only your VPN service can answer.
Another example is Perfect Privacy, which has a truly zero logs policy and allows users an unlimited number of device connections. According to Perfect Privacy, no logs = no restrictions (a high standard).
2. Limiting bandwidth
Bandwidth restrictions also require logging. To limit the amount of bandwidth used with a given account, logging is obviously necessary. Therefore if any VPN has bandwidth limits and also claims to be a “no logs” VPN, this should raise some questions. Three examples of this are Trust.Zone, TunnelBear, and Windscribe, a Canada VPN service. All three of these offer “free trials” that are limited to a certain amount of bandwidth.
3. Logging with rental servers (VPS)
Many VPNs utilize virtual rental servers (virtual private servers). A VPS is much cheaper than a dedicated (bare metal) server, but this creates some problems from a privacy standpoint.
The problem is that rental servers will often maintain logs of server activity. Furthermore, local authorities can possibly force a server host to log data. In this case, the “no logs” policies of a foreign VPN company means absolutely nothing – local authorities would go directly to the datacenter to get whatever they need.
One example of this was a man in the Netherlands who was arrested despite using a “no logs” VPN provider. The police simply went to the server host (i.e. the landlord) and got all the data they needed to find and arrest the man (who was accused of making bomb threats).
4. National spying agencies force companies to log
Spying agencies, such as the NSA and GCHQ, have been known to force companies to log and/or hand over private customer information. Big tech companies in the US have been facilitating NSA spying since at least 2010 – see the PRISM Program. The Investigatory Powers bill in the UK mandates all data be logged and maintained for 12 months. Targeting a particular company or server network is especially easy.
Even worse, logging requests may be accompanied with a “gag order” – making it illegal for the company to disclose what they’re being forced to do. We noted this exact case, for example, in our IPVanish review.
5. Troubleshooting problems and optimizing VPN performance
Logging connection data is often justified by VPN providers for fixing problems with their service and optimizing their network. While running a fast, secure, and reliable VPN service does not necessarily require logging, most VPNs will at least maintain some minimal connection logs to keep everything working well.
Contradictory claims and false promises
The biggest problem right now is that more and more VPNs are using the “no logs” phrase as a marketing slogan, when it is in fact not true at all. Typically they’ll make a “no logs” claim boldly on their homepage, and then carefully disclose all the data they “keep” when you read the privacy policy and terms.
Here’s is a previous example from our PureVPN review:
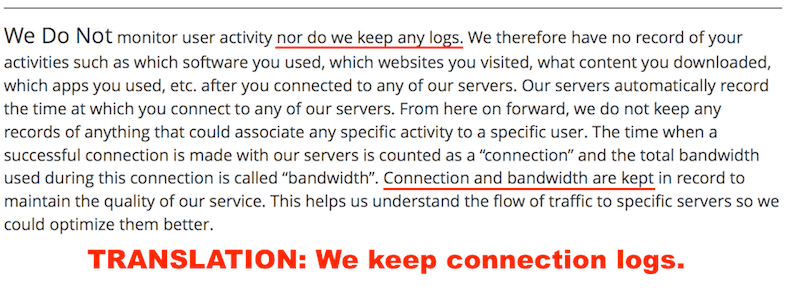
While connection logs are not necessarily bad, making false or contradictory statements only adds to the confusion when selecting a VPN. Circumstances like this are one reason we prefer third-party audited VPNs such as ExpressVPN vs PureVPN and other VPNs that merely claim to keep no logs, without any outside confirmation.
VPN logs are a grey area
The reality is that it’s nearly impossible to ever verify if these “no logs” claims are true.
Further adding to this confusion is that some VPNs have convoluted definitions of what “no logs” actually means. And of course, there’s no standard that can be used and no widely-accepted definition.
Foreign jurisdiction – Making matters even worse, many VPNs operate in overseas jurisdictions and can never be held liable for dishonesty and false advertising. If a VPN service in Hong Kong lies to customers in the United States, there’s not much that can be done.
Foreign (overseas) businesses will never be held liable for violating false advertising laws and deceiving customers. There are simply beyond the law. While this is often good for privacy, it is also a drawback for accountability.
This is why trust is so important.
If you find a VPN that makes contradictory or misleading statements about their policies, it raises questions about their honesty and trustworthiness.
When “no logs” claims are verified
On a positive note, there have also been a few examples where legal cases have verified the validity of a VPN provider’s “no logs” claims. Let’s take a look at a few of those examples:
ExpressVPN server seized in Turkey
The most recent of example of a VPN provider’s “no logs” claims getting backed up by real-world events is with ExpressVPN. Last year they had one of their servers seized in Turkey, where police were attempting to obtain customer data for an investigation. However, due to ExpressVPN’s no logs policies, authorities were not able to get any information from the server, simply because no data was available.
ExpressVPN issued a statement on their website, here is a brief excerpt:
As we stated to Turkish authorities in January 2017, ExpressVPN does not and has never possessed any customer connection logs that would enable us to know which customer was using the specific IPs cited by the investigators. Furthermore, we were unable to see which customers accessed Gmail or Facebook during the time in question, as we do not keep activity logs. We believe that the investigators’ seizure and inspection of the VPN server in question confirmed these points.
This case confirmed ExpressVPN’s logging policies and overall commitment to securing customer data.
Perfect Privacy server seized in Holland
Another example of this is Perfect Privacy having their servers in Rotterdam seized. As with ExpressVPN, no customer data was affected due to a strict no-logs policy. This is explained further on their website here.
In addition to a completely no logs, zero-knowledge policy, Perfect Privacy also operates all of their servers in RAM disk mode. This ensures that nothing is stored on the actual server, and if power is ever cut, there will be no data available (further explained in the Perfect Privacy review).
While Perfect Privacy is a great VPN, it is pretty expensive at around $9 per month. For alternatives, you can see these best cheap VPNs.
VPN logs audits
In some cases, VPNs have undergone third-party audits that have verified no logs. For example, we have the case of NordVPN and Proton VPN, which have both been audited and verified to be no logs. There are also VPNs that have passed security audits, but have not yet undergone a no-logs audit.
See our no-logs VPN guide for more information about VPNs that have been proven to be “no logs” with real-world test cases.
Other cases
In another case, Private Internet Access was called into court regarding an FBI investigation. In court, they publicly stated that they do not have any logs or customer data to provide to authorities. While this does not really verify anything, it does add further validity to their “no logs” claims.
And lastly, there have also been a few cases where law enforcement agencies have shown “no logs” claims to be false. One infamous case was with PureVPN logging customer data and handing this over to authorities, despite claiming to have a “zero logs policy” on their homepage. See the article about PureVPN keeping logs for more info on this topic.
VPN logs FAQs
Now let’s dive into some frequently-asked-questions concerning VPN logs.
Put simply, VPN logs are just the data that VPN providers collect from the operation of the VPN service. This data can come in many forms, including server stats, timestamps, last connection time, connection duration, user IP address, websites and IP addresses visited, and other data. Unless the VPN is a strict no-logs service, anytime you connect to the VPN service itself, you will probably be generating logs that are being collected by the VPN service provider. From a privacy perspective, we strongly recommend choosing a reputable no-logs VPN service that has been independently verified.
Whether or not your VPN keeps logs will vary depending on the VPN service you are using. To determine whether or not your VPN keeps logs, you can carefully read your VPN’s Privacy Policy and determine exactly what logs are kept and for how long.
It’s important to keep in mind, however, that some VPNs may not even be complying with their own privacy policy. We saw this, for example, with PureVPN logging users while still claiming to be a “no-logs” service.
In most cases, VPN logs are stored on some kind of administration server under the control of the VPN service itself. Most VPN services should not be keeping any logs on the VPN servers. This could put user data at risk from third-party server seizures. The best VPN services will run all servers in RAM memory without any hard drives. This ensures that no data can ever be physically saved on a VPN server.
Anytime you connect to a VPN service, the VPN will be able to see what sites you are visiting through the VPN. Conversely, when you have a secure connection through a VPN, your ISP will not be able to see any websites you connect to because all of the data will be encrypted between your device and the VPN server. However, if there are any VPN data leaks, particularly DNS leaks, this can expose your browsing history to third parties, even if you are using a VPN. This is why it’s critical to periodically test your VPN for any issues or problems.
Conclusion on VPN logs
With VPN logs, the main thing to look for is honesty and transparency. If you see that the “no logs” claims on the homepage do not align with the VPN’s privacy policy, then that indeed is a problem.
In terms of the big picture, other important considerations are jurisdiction and test results.
These factors are all taken into consideration with the rankings on the best VPN service report.
We also have a VPN coupons guide that is regularly updated with the latest deals.
Related Articles:
- ExpressVPN Coupon
- CyberGhost vs NordVPN
- NordVPN vs PIA (Private Internet Access)
- Free Trial VPN Services
This VPN logs guide was last updated on May 7, 2024.

Ty for this information. I hv a brain injury. + many surgeries.my life everything hacked. Today tragedy! I can’t take this. Apple is sending another phn. How did this happen. Swapped out sim. I hv vpn proton mail. Pls advise Ty hugs and safe practice for all!
I also have proton vpn paid! Ty