
This 20-part in-depth guide gives you everything you need to know about Virtual Private Networks (VPNs) .
VPN usage continues to surge around the world — and there are many factors that explain this trend:
- Privacy – More people are concerned about digital privacy than ever before. Whether it is corporate data collection or government surveillance efforts, the internet is becoming more invasive by the day. VPNs offer privacy by encrypting your traffic while also hiding your IP address and location.
- Security – Public WiFi is a dangerous place where hackers can target users, intercept traffic, and collect data from users who are not encrypting traffic through a good VPN.
- Unrestricted Access – Websites and streaming services the world over are implementing geo-restrictions and other methods to block/restrict content. Whether a country is carrying out censorship or a certain website is using geo-blocks, a VPN is your ticket for full access, allowing you to appear anywhere in the world.
These are the top three reasons people are using VPNs, but there are others as well. We’ll examine each of these topics in more detail below.
Table of contents – Here are the topics we’ll cover in this 20-part VPN guide.
- What is a VPN
- How a VPN works
- Why use a VPN
- What are the best VPNs?
- Are VPNs safe?
- Are VPNs legal?
- How do I set up a VPN?
- Why a VPN is necessary for online privacy
- Will a VPN make me 100% anonymous?
- VPN protocols and encryption
- VPN logs – different types
- VPN performance and speed
- Using VPN for streaming
- Using a VPN for torrenting
- VPNs on Android and iOS devices
- Using a VPN on a router
- VPNs and Tor
- VPN leaks and kill switches
- How to defeat VPN blocks
- The future of VPNs
What is a VPN?
A VPN is a Virtual Private Network. It allows you to access the internet with more security and privacy, while also giving you the ability to get around censorship or content restrictions. In this guide we will discuss the following VPN terms:
- VPN client – Software that connects your computer/device to a VPN service. The terms ‘VPN client’ and ‘VPN app’ are used interchangeably.
- VPN protocol – A VPN protocol is basically a method by which a device creates a secured connection to a VPN server.
- VPN server – A single endpoint in a VPN network to which you can connect and encrypt your internet traffic. Most VPNs have hundreds (or even thousands) of VPN servers around the world.
- VPN service – For our purposes here, a VPN service is an entity that provides you with the ability to use their VPN network. Usually, a VPN service provides custom VPN apps (clients) for different devices and operating systems, but not always. Access is usually sold via a subscription. The terms ‘VPN service’ and ‘VPN provider’ are used interchangeably.
Now we will get into the basics of how a VPN actually works.
How a VPN works
A VPN works by creating an encrypted connection between your computer/device and a VPN server. Think of this encrypted connection as a protected “tunnel” through which you can access everything online, while appearing to be in the location of the VPN server you are connected to. This gives you a high level online anonymity, provides you with added security, and allows you to access the entire internet without restrictions.
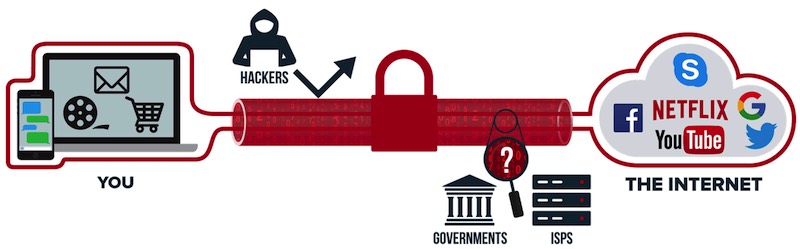
Without a VPN, everything you do online is traceable to your physical location and the device you are using via the device’s IP address. Every device that connects to the internet has a unique IP address – from your computer to your phone and tablet. By using a VPN, you will hide your true location and IP address, which will be replaced by the VPN server you are using.
Most VPN providers maintain servers all around the world. This gives you lots of connection possibilities and access to worldwide content. Two VPNs that both have a large server network around the world are ExpressVPN and NordVPN.
How many VPN servers are necessary?
The answer to this question all boils down to what you are doing with your VPN. Some VPNs will have thousands of VPN servers located all over the world, such as with NordVPN and Surfshark. Other VPNs may have a small network with VPN servers in only about 20 different locations.
The number of servers required is subjective. However, as long as the VPN allows you to do everything you need, you will be good to go.
After purchasing a VPN subscription and downloading the software for your device, you can instantly connect to any of these worldwide servers.
Now that you know how a VPN works, let’s cover the reasons for using one.
Why use a VPN?
Why are so many people around the world using VPN services?
It really depends on your situation, but there are ten different reasons to use a VPN:
- Surf the internet without revealing your real IP address and geo-location (online anonymity).
- Add an extra level of security by encrypting your internet connection.
- Prevent your Internet Service Provider (ISP), third parties, network admins, and governments from spying on your online activities (encrypting your traffic) – and we have a report on ISP logging for more info.
- Unblock websites and access content that is restricted to certain geographic locations.
- Torrent, P2P download, and stream media safely and with more privacy.
- Bypass censorship and gain access to geo-restricted content.
- Save money on flights and other online purchases by changing your IP address (your virtual geographic location).
- Protect yourself from hackers and security risks on public WiFi networks, such as in cafés, hotels, and airports.
- Protect your private data, such as bank passwords, credit cards, photos, and other personal information when online.
- Surf the internet with peace of mind.
Now that we’ve covered why a VPN is used, we’ll move on to another question that many people have about VPNs.
What are the best VPNs?
We have an entire guide dedicated to the best VPN services.
To save you time, however, the table below lists our picks for the top three VPNs that will work well for all types of use cases. As noted in our report, these VPNs all:
- User-friendly apps for all major devices and operating systems
- Very secure with built-in leak protection settings and strong encryption
- Excellent performance (fast speeds that we regularly test)
- Great for streaming and torrenting
- 24/7 live chat customer support
- A full 30 day money-back guarantee on all subscription plans
Finding the best VPN all boils down to matching up your unique needs with the VPN that meets your requirements. There is no one-size-fits-all “best VPN” for every user. Nonetheless, there are a handful that do well in nearly all categories and come out on top in our rankings and guides.
To learn more about these VPNs, and also a handful of honorable mentions, check out our best VPN list here.
Are VPNs safe?
As a general rule of thumb, VPNs are safe to use – as long as you are using a high-quality VPN service. But therein lies the catch.
There are currently over 200 VPNs on the market – even more when you consider all the random free VPN apps in the Apple and Google Play stores. Unfortunately, most VPN services – particularly the free VPNs – have flaws, bugs, and problems that pose a threat to your security and privacy.
In other words, there are very few high-quality VPNs that will keep you safe and protect you against data leaks on all your devices.
For example, one alarming study found that 84% of free Android VPN apps leak user data. While most people know that free VPNs should be avoided, there are still millions of people using these dangerous apps.
As I explained in my overview of free VPN services, there are many reasons to avoid free VPNs altogether:
- embedded malware (quite common with free VPN apps)
- hidden tracking (many popular VPN providers hide tracking in the apps to collect your data)
- third party access to your data
- stolen bandwidth
- browser hijacking
- traffic leaks (IP address leaks, DNS leaks)
- fraud (identity theft and financial fraud)
There are also a number of different VPN scams to avoid – from dubious “lifetime” VPN subscriptions to bogus features and fake reviews. As a general rule of thumb, you typically get what you pay for when it comes to VPN services.
Note: And if you are on a budget, you can always check out a cheap VPN and avoid the dangerous free VPNs.
Are VPNs legal?
Throughout the Western world the answer is generally yes, VPNs are perfectly legal to use for the purposes of online privacy and security. In fact, businesses every day use VPNs – and that will not change any time soon.
However, there are a few exceptions in places like the United Arab Emirates, where VPN use is currently restricted. Some Middle Eastern countries, such as Saudi Arabia and Iran, frown on the use of VPNs because they allow people to get around internet censorship efforts.

But even still, the laws in these countries generally do not outlaw the VPN itself, but rather the use of a VPN to bypass the state censorship efforts.
This is also the case in China, where the government has been fortifying its “Great Firewall” to block VPNs and websites. Nonetheless, you can still use the best VPN for China to get around these issues. Russia has also attempted to “ban” some VPNs – but these measures often fail, simply because VPN traffic can be hidden to look like regular HTTPS traffic. There are a few VPN providers that do quite well with obfuscating VPN traffic in their apps.
Note: VPNs are routinely used by businesses around the world for network security. Therefore you will likely never see an outright “ban” on all VPNs because they are a necessary tool for both businesses and individual security.
But can’t people use VPNs to do bad things?
Of course, but you should think of VPNs like steel. Steel can be used for good purposes, such as bridges, buildings, and transportation. But it can also be used to build bombs, guns, and tanks, which harm people. Completely banning steel because it is sometimes used for bad purposes would be insane and stupid.
The same is true for encryption and VPNs. Banks, businesses, and any website that deals with sensitive data must use encryption technology to keep people (and their data) safe. VPNs and encryption are necessary tools that we all need to be using, even if a few people misuse this technology for their own reasons.
Disclaimer: I’m not a lawyer and none of this is legal advice. Consult the laws of your country to verify what is and is not legal!
How do I set up a VPN?
The exact instructions for setting up a VPN depends on the device you are using and the VPN service you will be connecting to. Most VPN providers – especially the ones recommended on this site – offer simple installation guides for all major operating systems and devices.
Here’s a general outline for how to set up a VPN:
- Choose a good, trustworthy VPN service
- After purchasing a VPN subscription, download the VPN software for the device / operating system you will be using.
- Once the VPN client is installed on your device, log in to the VPN service using your credentials (through the VPN app).
- Connect to a VPN server and enjoy using the internet with privacy and freedom.
Windows, Mac OS, Android, and iOS users also have the option of using the built-in VPN capability on their operating systems. This uses the IPSec/IKEv2 or IPSec/L2TP protocols, rather than OpenVPN, which requires the use of apps. You will need to import the VPN configuration files from your VPN provider if you want to go this route.
The most common way to use a VPN is through a VPN client (VPN app) offered by your VPN provider. As we noted in our guide on the best VPNs for iPhone, some devices have built-in VPN support. However, a dedicated VPN app is still probably the best option as it gives you all the features.
Why a VPN is necessary for online privacy
A good VPN can provide you with both online privacy and security.
Without a VPN, your internet service provider (ISP) can easily monitor and record your online activities: sites you visit, comments you make, social media interactions, preferences etc.
Many countries now require internet providers to log user data and browsing activities. A VPN is the best solution to protect yourself against these privacy violations.

When using a VPN, your internet provider can only see that you’re online and connected to a VPN server. That’s it. With a VPN, your data is encrypted and secured, which makes it unreadable to third parties.
With a VPN, public WiFi hotspots are once again safe to use, thanks to secure encryption that protects your data. Using public WiFi without a VPN is risky because hackers can exploit public wireless to steal your identity, credit cards, bank accounts, passwords, etc. A VPN will encrypt and protect this data from third parties and hackers.
Will a VPN make me 100% anonymous?
The short answer is no.
Given all the different ways someone can be de-anonymized online (particularly through browser fingerprinting), a VPN alone will not give you 100% anonymity. In fact, with the vast resources of surveillance agencies, such as the NSA, it is probably very difficult to ever achieve 100% online anonymity.
On a positive note, however, there are simple steps you can take to further increase your online anonymity:
- Use a secure browser that protects against browser fingerprinting (your browser can reveal lots of information to third parties).
- Use a good ad blocker. Advertisements are basically tracking in disguise, collecting your activities online, profiling you, and then using that data to target you with better ads. There are also some VPNs with ad blocking.
- Use a VPN to hide your IP address and location, while also encrypting your traffic.
Regarding VPNs with ad blocking, this is a feature were are seeing with more providers. For example, both NordVPN and PIA now offers this feature.
These are the three basics that everyone should be doing. However, we list more tools and solutions on our privacy tools page.
VPN protocols and encryption
Most commercial VPN services offer a variety of different VPN protocols you can use with the VPN app.
What exactly is a VPN protocol?
A VPN protocol is a set of instructions to establish a secure and encrypted connection between your device and a VPN server for the transmission of data.

Here are the most popular VPN protocols in use today:
- OpenVPN – OpenVPN remains the most popular and most secure VPN protocol that is used on all types of different devices. OpenVPN is an open-source project developed for multiple types of authentication methods. It is a very versatile protocol that can be used on many different devices, with a variety of features, and over any port with UDP or TCP. OpenVPN offers excellent performance and strong encryption using the OpenSSL library and TLS protocols.
- WireGuard – WireGuard is a newer VPN protocol that aims to offer improved security and better performance in comparison to existing VPN protocols. By default, WireGuard has some issues with privacy, although most VPNs supporting WireGuard have overcome these issues (see for example with NordVPN and Surfshark). Now a word on speeds. In our WireGuard vs OpenVPN speed tests, WireGuard was about 57% faster than OpenVPN on average.
- IKEv2/IPSec – Internet Protocol Security with Internet Key Exchange version 2 (IPSec/IKEv2) is a fast and secure VPN protocol. It is automatically pre-configured in many operating systems, such as Windows, Mac OS, and iOS. It works well for re-establishing a connection, especially with mobile devices. One downside with IKEv2 is that it was developed by Cisco and Microsoft and is not an open-source project, like OpenVPN. IKEv2/IPSec is a great choice for mobile users who want a fast, light-weight VPN that is secure and can quickly reconnect if the connection is temporarily lost.
- L2TP/IPSec – Layer 2 Tunneling Protocol with Internet Protocol Security is also a decent choice. This protocol is more secure than PPTP, but it does not always have the best speeds because data packets are double-encapsulated. It is commonly used with mobile devices and comes built-in on many operating systems.
- PPTP – Point-to-Point Tunneling Protocol is a basic, older VPN protocol that is built-in on many operating systems. Unfortunately, PPTP has known security vulnerabilities and is no longer considered a safe protocol for privacy and security reasons.
Each VPN protocol has its own pros and cons. OpenVPN is the most popular and widely-recommended, because it is secure, open-source, and also offers good performance. But it also requires the use of third-party apps. L2TP/IKEv2 is also a secure protocol with excellent performance and it can be used natively on most operating systems (no apps required) – but it’s not open source.
If you are looking for speed and updated security, WireGuard remains an excellent choice. The best VPN for WireGuard is currently NordVPN, which supports WireGuard directly in all of the VPN apps.
For WireGuard speed comparisons, you can also check out our NordVPN vs CyberGhost report.
VPN Encryption
AES (Advanced Encryption Standard) is one of the most common cryptographic ciphers in use today. Most VPNs utilize AES encryption with either a 128-bit or 256-bit key length. AES-128 is considered secure, even with the advances in quantum computing.
Here is an interesting quote from VPN.ac on AES and encryption and vulnerabilities:
OpenVPN 256-bit AES is kind of overkill, rather use AES 128-bit. We don’t expect anyone to go for AES cracking while there are weaker links in the chain, such as the RSA keys: how are they generated (good or poor entropy, online/offline generation, key storing on servers etc.). Therefore, AES-128 is a very good choice over AES-256 which is mostly used for marketing claims (“bigger is better”).
Aside from AES, there are other VPN ciphers, such as Blowfish and Camellia, although they are rarely offered by VPN services.
WireGuard uses an interesting assortment of encryption algorithms, as we explained in the main WireGuard VPN guide:
- ChaCha20 for symmetric encryption, authenticated with Poly1305, using RFC7539’s AEAD construction
- Curve25519 for ECDH
- BLAKE2s for hashing and keyed hashing, described in RFC7693
- SipHash24 for hashtable keys
- HKDF for key derivation, as described in RFC5869
Moving beyond security, let’s now examine VPN logs and privacy.
VPN logs – different types
When it comes to privacy, it’s good to pay attention to logs and logging policies.

Here are the different types of VPN logs:
- Usage (browsing) logs – These logs basically include your online activities: browsing history, times, IP addresses, metadata, etc. Reputable VPN services do not collect any usage logs. With shady free VPN apps, however, you will often find they are collecting usage logs (and selling the data).
- Connection logs – Connection logs typically include dates, times, connection data, and sometimes IP addresses. Usually this data is used for optimizing the VPN network and potentially dealing with user problems or ‘terms of use’ issues. The key here is reading the fine print to see how the data is secured and how regularly it is deleted.
- No logs – While there are many VPNs that claim to be ‘no logs’, there are only a few that have been verified to be truly no logs VPN services in real-world tests and/or through third-party audits.
Minimal connection logs that are secured and regularly deleted are not very concerning – but it all depends on the user and threat level.
Also, keep in mind that there are some VPN services that will falsely claim to be “no logs” on their homepage, but then carefully disclose the data that is collected in their privacy policy. There have been cases where authorities obtained user data from “no logs” VPN providers. Two examples of this are with PureVPN (logging case) and IPVanish (logging case).
VPN performance and speed
When you’re using a VPN, a lot is going on behind the scenes. Your computer is encrypting and decrypting packets of data, which is being routed through a remote VPN server. All of this takes more time and processing power, which will ultimately affect your internet speed.
To ensure the fastest speed while using a VPN, it’s best to connect to the closest VPN server that fits your needs. For example, if you’re in the UK and want to watch blocked videos that are available to people in the United States, choosing a VPN server in New York is better than a Los Angeles server.
VPN speeds are a factor we always test for in our VPN reviews. Top-quality VPNs will offer consistently fast speeds throughout their server network. You should not be able to notice any performance tradeoff with regular browsing or streaming videos. That being said, due to encryption and increase latency, you will still take a drop in speed.
Even with VPNs that claim to be “fast” with all servers, there can be huge speed fluctuations, as we saw in the ProtonVPN vs NordVPN comparison.
On a positive note, many VPNs are rolling out solutions to give you the fastest VPN speeds possible. For example, NordVPN’s implementation of the WireGuard VPN protocol with NordLynx recently broke our speed test record. This was the fastest VPN speed we recorded, which we got with a NordVPN server in Seattle using WireGuard:
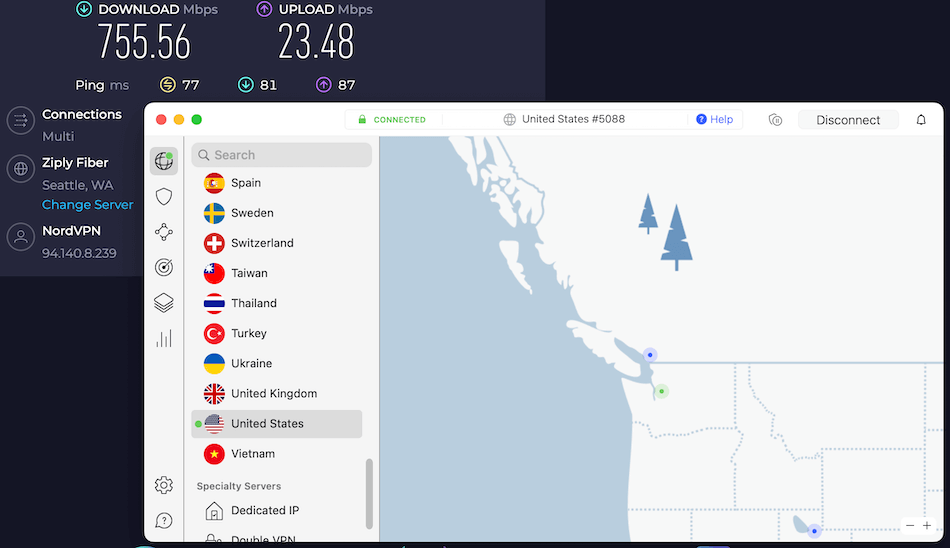
Here are a few tips for maximizing your VPN speed:
- Get a premium VPN service with good performance, such as NordVPN.
- Connect to a nearby server that is not congested with other users (lots of available bandwidth).
- Try changing VPN protocols if the first two options do not work. In our tests, we’ve found the WireGuard protocol to be significantly faster than all other VPN protocols.
VPN speeds may also be limited by the device you are using, your network, or your internet provider throttling VPN connections. Therefore you may want to tinker with variables to find the best solution for speeds with your VPN.
And even if you are using WireGuard, speeds can vary greatly between VPN providers, as noted in the CyberGhost vs NordVPN guide.
Using a VPN for streaming
Aside from online privacy and security, VPNs are also used by thousands of people around the world for streaming. There are many reasons to use a VPN for streaming.
A VPN will allow you to access content that is censored, geo-blocked, or otherwise restricted. Because a VPN gives you the ability to “tunnel” into any VPN server location around the world, it remains the ultimate tool for online streaming.
Below I’m using NordVPN to stream US Netflix:
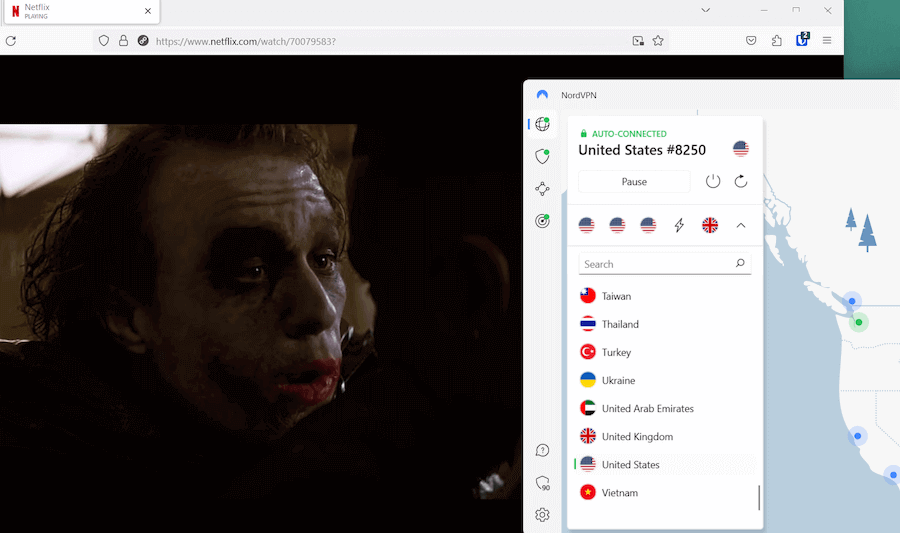
Here are a few popular streaming uses for VPNs:
- Streaming Netflix – Using a good Netflix VPN is a great idea no matter where you live. This allows people living anywhere in the world access to American Netflix, or any other major Netflix library that’s supported by your VPN.
- Streaming sports – Some sporting events/games are restricted to certain geographic regions, with access blocked for anyone outside those regions. A VPN lets you appear to be “virtually” located in the designated area for streaming.
- Streaming Kodi – Using a VPN with Kodi is a popular way to unlock any add-ons and utilize Kodi to its full potential.
- Evading censorship – Censorship continues to ramp up throughout the world and there are numerous media websites that are blocked in different regions. A VPN allows you to easily break through these censorship efforts to access the content you want.
VPNs are also popular for other streaming services, such as Hulu, Amazon Prime, and BBC iPlayer. Many expats living outside their home country use VPN services to unblock websites, streaming add-ons, and media channels in various locations.
Using a VPN for torrenting
Another very popular use for VPNs is with torrenting and P2P downloads. When you use a VPN for torrenting, your true identity and IP address will be concealed from third parties. Additionally, your ISP will not even be able to see your activities — whether you are torrenting or streaming, your ISP will be in the dark.
Torrenting and P2P filesharing is somewhat of a grey area and may be classified as copyright infringement, depending on the content you are sharing/downloading and where you live. Right now, countries throughout the world are cracking down on torrenting, from Europe to the United States and Australia. Here is one such example illustrating the risks of torrenting without a VPN:

While we do not support any illegal activity or copyright infringement here at Restore Privacy, it should be obvious that torrenting without a VPN can be risky.
Media companies often run networks of monitoring nodes, which will join torrenting swarms and collect connection data of all infringing parties. Then, the media companies can go to the internet service providers that own the IP addresses they collected, and link these up to users along with connection times. The user will then be fined or sued for copyright infringement on behalf of the copyright holder.
The best solution here is to always torrent with privacy by using a good VPN.
VPNs on Android and iOS devices
People spend a lot of time on mobile devices, and mobile internet traffic continues to rise. As such, VPNs are also becoming more popular on mobile devices.
There are three different ways to use a VPN on Android and iOS devices:
- With custom VPN apps. Most providers offer custom VPN apps for both Android and iOS devices, which are usually fast, stable, and offer different features. For example, both Surfshark and ExpressVPN, as well as NordVPN, offer secure and user-friendly clients for Android.
- With third-party VPN apps. There are also popular, third-party VPN apps that you can use with your VPN service, such as OpenVPN for Android, which is free and open source.
- With built-in VPN functionality. With Android, you can use the built-in IPSec/L2TP functionality. With iOS, you can use the built-in IPSec/IKEv2 functionality. Both operating systems have VPN preferences in the settings area. You will need to import the configuration files from your VPN provider into your phone/tablet to go this route.
While VPNs have improved significantly on iOS and Android, they still don’t work quite as well as they would on a computer. The main reason for this is that using a VPN is a bit more complicated than typical applications, requiring connection to external servers, encryption, and decryption. Naturally, this is a bit challenging on a phone which may go in and out of connectivity. However, this is improving as cell service and bandwidth continue to improve.
WARNING: Be very careful with mobile VPN apps from third parties. There are many shady VPN apps that are dangerous and should be avoided. Do your research before installing the VPN app and remember that highly-rated (free) apps in the Apple and Google Play stores can still be full of malware – as explained in this study. Your best bet is to only use the VPN mobile apps offered by a reputable (paid) VPN service, not a shady free VPN app that is probably collecting your data for profit.
We have reviewed some of the best VPNs for Android here.
Using a VPN on a router
It is possible to use a VPN on a router, although it may require a bit of work.
A good VPN router offers the following benefits:
- Extends the benefits of a VPN to all your devices without installing software
- Easily protects you against surveillance and internet service provider (ISP) spying
- Secures your home network against attacks, hacking, and spying
The trick to getting this setup correctly is first choosing a good VPN service and then selecting the right router – the rest is easy.
Important note: The main factor when choosing a VPN router is the router’s CPU (processing power). Unfortunately, most consumer-grade routers are underpowered and do not do well with VPN encryption.
Right now, the best VPN router we have tested is the Vilfo router, from the creators of OVPN in Sweden.
Other devices with a VPN
The best way to use a VPN on all types of devices is through a router. This is because there are many internet-connected devices that do not work for VPNs. For example, you can’t use a VPN on Apple TV or a VPN with PS5. However, these devices will benefit when connected to a VPN router.
VPNs and Tor
VPNs and Tor are both privacy tools that offer online anonymity, but they are very different from each other.
Tor stands for The Onion Router and is both a browser and a network that utilizes multiple “hops” to protect user privacy. Tor was created by the US government in 2002 and is still largely dependent on US government agencies for funding. Aside from this troubling fact, there are a few other concerns with Tor:
- Some believe that the Tor network has been compromised
- Microsoft’s DRM can easily expose Windows-on-Tor users
- Viewing PDF documents while using Tor can also leak your identity
- Tor users are vulnerable to end-to-end timing attacks
- Tor is too slow for everyday use, especially with anything that requires some bandwidth, such as watching videos
There have also been numerous issues with malicious Tor nodes. Many also suspect that government agencies are operating Tor nodes for surveillance purposes.
We discuss these issues and more in our VPN vs Tor comparison.
One way to mitigate risk is to distribute trust. You can do this by using a VPN and Tor together, here’s how:
- Connect to a VPN > Launch Tor browser: This method is pretty basic and self-explanatory. Simply use your desktop VPN client and connect to a VPN server, then open the Tor browser and use Tor as normal. This won’t give you great speeds, but it’s a simple way to use “Tor-over-VPN”. This method hides your real IP address from the Tor network.
- Use a VPN service with servers that exit onto the Tor network. In this case, you can simply connect to a designated “Tor-over-VPN” server, and your traffic will automatically leave the VPN server, exit onto the Tor network, and then go through to the regular internet. We tested this out in our NordVPN review.
It should also be pointed out that you can get many advantages of Tor, such as multi-hop configurations, with VPNs. There are a few VPN providers that offer multi-hop VPN servers and cascading support – see the multi-hop VPN guide for an in-depth discussion of this topic.
VPN leaks and kill switches
One serious issue that plagues many VPN services is when data leaks out of the VPN. Here are a few different types of leaks that will undermine your privacy and security when using the VPN:
- DNS leaks – This occurs when your DNS requests leak out of the VPN tunnel and are processed by your internet provider. This can reveal your browsing history (DNS requests) to third parties, the IP address of your internet provider, and your general location.
- IP address leaks – An IP address leak is when your IP address leaks out of the VPN tunnel. This can be a short, temporary leak, or a continuous leak. This is often the case with IPv6 addresses with VPNs that do not support or properly block IPv6.
- WebRTC leaks – This is mainly an issue with Firefox, Chrome, Brave, and any other Chromium-based browsers that utilize WebRTC APIs. A WebRTC leak exposes your IP address through your browser, even if you are using a good VPN. See the WebRTC leak guide for how to fix this problem in your browser.
Here is an example of DNS leaks we found in the PureVPN review:
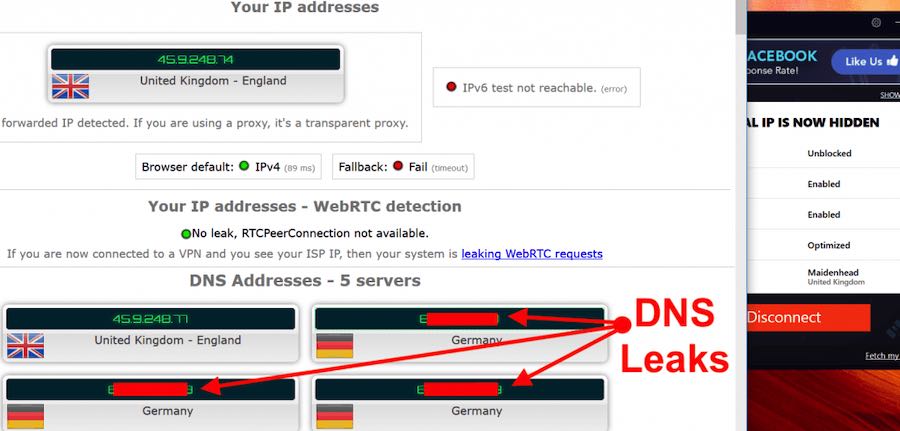
To prevent leaks, many VPNs offer a VPN kill switch. This will block traffic if your VPN connection unexpectedly drops. All of the leading VPNs have this feature.
Are you worried about VPN data leaks? It’s a good idea to regularly test your VPN to check for any problems.
How to defeat VPN blocks
One problem that some people face is that their VPN is getting blocked. There are a few different circumstances in which VPNs are blocked:
- Restrictive countries – China, UAE, and Iran all implement some form of VPN blocking, because they do not want people using VPNs to get around censorship efforts. (See the best VPN for UAE guide for solutions.)
- School networks – School networks sometimes block VPNs for two reasons. First, they want to be able to monitor everything you do online (and on their network), which is easy to do if you aren’t using a VPN. Second, they may want to block torrenting, streaming, and other high-bandwidth activities. A VPN allows you to easily get around these restrictions and access any blocked websites.
- Work networks – Work networks often block VPNs for the same reasons mentioned above: they want to control and monitor workers’ online activities.
The best way to get around VPN blocks is with obfuscation. VPN obfuscation basically hides VPN traffic behind standard HTTPS (Hypertext Transfer Protocol Secure) encryption, such as when you connect to a banking website over port 443.
Many VPNs offer obfuscation features for this situation. Some offer obfuscated servers, while others offer a self-developed protocol that will automatically obfuscate traffic with any server, as we observed in the VyprVPN review. Below is an example with VyprVPN, which uses the Chameleon protocol (based on OpenVPN) to get around VPN blocks when other protocols fail:
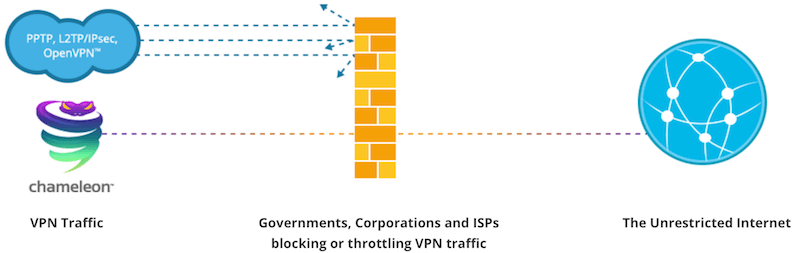
Unless you are in a restricted network situation where VPNs are getting actively blocked, you should not need to use obfuscation, since it may affect performance.
We have many different guides on the best VPNs for streaming different media channels:
Note: Most of the “big players” in the VPN industry will offer solid streaming support. Meanwhile, some of the more privacy-focused VPNs, such as Perfect Privacy, do not do as well with streaming.
What is the future of VPNs?
The future of VPNs is looking bright – but not for the right reasons.
Mass surveillance, corporate tracking, and online censorship are three drivers that will continue to push VPN usage higher. Internet providers are increasingly blocking various websites – from adult content to torrenting sites. Concerns over surveillance and privacy are also rising:
- United States: Since March 2017, US internet providers are able to legally record your browsing history and sell this information to advertisers – or hand it over to surveillance agencies.
- United Kingdom: The UK is one of the worst countries in the world for privacy. Internet providers and telephone companies are required to record all browsing history, text messages, and location data of their customers. This data is provided to UK government agencies and is available without any warrant. The UK is also testing experimental new tools to track the browsing history of everyone.
- Australia: Similar to the UK, Australia implemented a mandatory data retention scheme requiring telecoms to collect text messages, calls, and internet connection data.
Going online without a VPN really leaves you exposed.
As people wake up to the risks of surveillance, data collection, and security threats, VPN usage will continue to grow. The growing trend of people streaming media and wanting to access various content from around the world also increases the demand for VPNs.
Whichever VPN you decide to use, be sure to do your research and select the best fit for your own needs and uses. We have many different VPN guides you can see on the RestorePrivacy homepage.
This VPN overview guide was last updated on May 9, 2024.

Want to know if that VPN address you can use is Blacklisted anywhere?
[https://whatismyipaddress.com/blacklist-check]
Find out what your public IPv4 and IPv6 address is revealing about you!
[https://whatismyipaddress.com/]
My IP address information shows your location; city, region, country, ISP and location on a map. Many proxy servers, VPNs, and Tor exit nodes give themselves away.
Find out whether you have a static IP address or a dynamic IP address.
See what’s the difference between the two?
https://whatismyipaddress.com/dynamic-static
Yes before 2017 here in the US we did have a fig-leaf of PRIVACY to cover us. But, Presidents change and so to does the FCC. Thinking of the arguement that broke the camels back around 2017, ISP’s aruged that google, microsoft, and other titans for the digital information age were not deprived nor limited to the non-monetary gains of selling their users information.
Our privacy in the US can be changed if the people make it so. BECAUSE
The FCC is an independent agency of the United States government that regulates communications by radio, television, wire, satellite, and cable across the United States. The FCC maintains jurisdiction over the areas of broadband access, fair competition, radio frequency use, media responsibility, public safety, and homeland security.
FCC also provides varied degrees of cooperation, oversight, and leadership for similar communications bodies in other countries in North America. The FCC is funded entirely by regulatory fees.
Commissioners:
The FCC is directed by five commissioners appointed by the president of the United States and confirmed by the United States Senate for five-year terms, except when filling an unexpired term. The U.S. president designates one of the commissioners to serve as chairman. No more than three commissioners may be members of the same political party. None of them may have a financial interest in any FCC-related business.
Trouble here is the FCC is an independent agency of the US government headed by no more than three commissioners of the five, to having the same political party. Then NONE of them may have a financial interest in any FCC-related business.
Conflicts-
Indepentent agency of the US Gov. staffed by political party comissioners – – per elected president, as appointed by the president of the United States and confirmed by the United States Senate for five-year terms, except when filling an unexpired term. Commissioners may continue serving until the appointment of their replacements. In practice, this means that commissioners may serve up to 1+1⁄2 years beyond the official term expiration listed above if no replacement is appointed. This would end on the date that Congress adjourns its annual session, generally no later than noon on January 3.
No financial interest in any FCC-related business.
Radio, television, wire, satellite, and cable would be the FCC-related businesses that commissioners are banned from having any financial interest of relationships. But this 5-year term should be extended to a window bigger than their seated commissioned term. Like 25 years in all for any commissioner, consisting as 5 years prior to that of a seat with the FCC and 20 years proceeding their appointment to a seat with FCC.
Financial Interest be defined from the FCC and encompass any relationship that as an FCC commissioner, there was paid or volenteered service, sat on any commission, committee, board, engaged in any service or function by any manner of means covering all radio, television, wire, satellite, and cable industries.
Is the fig-leaf back?
“On Thursday, Rosenworcel added that the vote would also prevent internet providers from selling Americans’ personal data or sharing it with tech companies to train artificial intelligence models”.
[https://www.cnn.com/2024/04/25/tech/net-neutrality-is-back/index.html]
Interesting find!
This move and the coming TicTok end might just decide its time for the national US digital data security and privacy laws policy’s being drafted and implement. That over-rides any state statutes, as well to how digital data is collected, stored, shared, profited from, and our individuals rights to limit and delete that digital data.
Resources:
This article; VPN: Everything You Need to Know in 2024 By Alex Lekander — “What is the future of VPNs? – – The future of VPNs is looking bright – but not for the right reasons.”
https://www.gatewayfiber.com/blog/how-does-the-internet-get-to-your-home
– The Backbone of the Internet –
At its core, the internet relies on a vast network of physical infrastructure to transmit data around the world. This network is commonly known as the internet backbone and consists of high-capacity fiber-optic cables, routers, and switches that connect various locations worldwide — thus the “worldwide” in worldwide web (www). Millions of miles of undersea fiber cables connect the world to the internet.
These backbone networks are managed and operated by major telecommunications companies, internet service providers (ISPs), and content delivery networks (CDNs).
– Local Exchanges and Central Offices –
Once the signal reaches the local area, it is directed to a local exchange or central office. These facilities act as hubs to manage and distribute internet traffic to individual customers. They serve as intermediaries between the ISP’s network and the customer’s home or business. The terms in largely interchangeable. Although a “central office” sounds like a big building such as the ISP’s headquarters, it’s really just an oversized outdoor cabinet that doesn’t take up very much room, especially in a fiber-optic internet setup.
– Internet Service Providers (ISPs) –
Internet Service Providers such as Gateway Fiber are vital to bridging the gap between the backbone network and you, the end user. ISPs provide internet access to both residential and commercial customers. They connect to the backbone network through large data centers and distribute the internet signal to customers via different technologies such as DSL, cable, fiber-optic, or wireless connections.
https://en.m.wikipedia.org/wiki/Decentralized_web
– The Decentralized Web –
is a network of independent computers that provide secure, censorship-resistant access to information and services without relying on central servers or clouds, using decentralized computing.
– Decentralized Computing –
has a long theoretical and practical history in the design of robust systems. The internet itself was designed around principles of decentralization, allowing an unknown network of machines to be organically connected, addressed, and updated over time without a central administration.
– Development of the Internet –
*Web 1.0 is sometimes described by asprimarily static webpages with minimal interactivity.
*Web 2.0 described as the “read/write” web, with dynamic content and user interaction, including platforms like YouTube and the advent of smartphones which could easily capture and broadcast information from anywhere.
*Web 3.0 is the name given to a decentralized web movement that is sometimes described as a “read/write/own” stage of internet development. It focuses on decentralizing the underlying infrastructure of the internet, shifting away from centralized data storage and management using new protocols and technologies.
Questions:
Would it not be a brighter furture for VPN’s and aspiring to their customers privacy needs as well, since the internet relies on a vast network of physical infrastructure commonly known as the internet backbone and consists of high-capacity fiber-optic cables, routers, and switches, for the VPN brands to merge in owning/managing some of that fundamental internet backbone?
Is this Internet Backbone a monoply (backbone networks are managed and operated by major telecommunications companies, internet service providers (ISPs), and content delivery networks (CDNs). that not only is stifling any competition and limiting any substitions but against the Internet itself that was designed around principles of decentralization, allowing an unknown network of machines to be organically connected?
Is it not possible for the major VPN’s to become more rooted in the fundamental Internet Backbone by ownership of any step of Telecomm’s, ISP’s or CDN’s structure?
What kind of service could a VPN provider offer customers by becoming a local hub such as a ISP service that would connect to the Internet Backbone (and encryption secure) this Doorway to the Internet that customers use locally to go worldwide?
Is it possible, feasible or not, for a VPN provider to break-free from the centralized data storage of the centralized web, incorporating data that is stored on users’ computers and used across various decentralized applications, and allowing large files to be shared by many participants who could not store it in its entirety. Blockchain networks are a more recent example of decentralized tools and systems, by 2021, BitTorrent announced the development of Project Maelstrom to develop a fully decentralized and censorship-resistant browser. Other decentralized browsers such as Beaker have been developed building on top of IPFS and other file-storage protocols. Why can’t VPN’s aim to restore the decentralized nature of the original web, thereby returning control and ownership to users by the sheer number of internet users who employ them?
Please add Roku to your testing. While Nord users can access the app would or without a VPN, those outside the USA can’t stream Roku content on Firestick or mobile devices even when using an Obfuscated server and settings. Nord blames my devices not their network.
If it is possible, maybe you could ask someone that you
know that uses a different vpn provider than you to do a few test.
Like, ask them to try streaming Roku with their Firestick and Mobile devices.
If he or she can stream movies, tv series, etc . . .
then I would think that Nord is simply incompatible.
Maybe other users on this website that use Nord
can verify for you that they can stream Roku on their Firesticks
and Mobile devices without any issues. Meaning, the issues might be from your set up.
Atlas Vpn will be closing ( shut down ) and merging with Nord vpn on April 24, 2024.
All current Atlas VPN paid subscribers will be transferred to the NordVPN service automatically for the remainder of their subscription period. For more info, you can visit www . atlasvpn . com
An important announcement from Atlas VPN
Ruth C. | March 25, 2024
Dear Atlas VPN community member,
Today, we share a significant update about the journey of Atlas VPN. After extensive deliberation and evaluation of our long-term business strategy, we have made the difficult decision to sunset Atlas VPN on April 24. This decision was not made lightly – it stems from a comprehensive assessment of the evolving cybersecurity landscape and our place in it.
Any solutions for Canadians who want to unblock Facebook’s recent geolocation restriction on News providers?
One well known premium VPN provider sent out a newsletter offering a free premium membership to anyone who solve this conundrum.
While there isn’t a solution at hand, it’s evident that Facebook, unlike Netflix, has the capability to effectively limit access based on geographical location. Instead of making payments to the Canadian Federal government, they’ve simply restricted access to Canadian news within Canada. I you’re in the USA or outside of Canada, you won’t face these restrictions, but this could lead to numerous authentication problems and raise suspicions, given that Facebook tracks your location.
And then there’s Google. Google is butt hurt about Canada’s Online News Act, and they decided not to offer Bard, its equivalent of ChatGPT to Canadians.
Anyway, one can argue, why would you want to get your news from Facebook, even for an official Facebook news page like the CBC or Global News? In fact, FB reports their decision hasn’t made a dent at all.
The funny thing though. It’s so unhinged how Canada’s news providers are willing to have a presence on TikTok knowing very well what kind of misleading and insecure the platform is.
Does isp see my ip address when i use vpn?
If isp doesn’t see my ip address, how does it know my vpn usage? or How will the isp know who I am?
Your ISP will see an encrypted tunnel between your device and the IP address of the encrypted VPN server you are connected to, but all data (the sites you visit) is encrypted and cannot be seen by your ISP or other third parties.
Doesn’t ISP see the IP address that my modem gives to use the internet?
Yes
Hope to help, this is what I understand.
ISP is your doorway connection to the internet.
VPN subscription (when used) supplies an encrypted tunnel over/on-top/within your ISP connection, through your device VPN’s client for your VPN service you’ve scribed to.
(Assuming the vpn client is system-wide installed, then any web contact would be encrypted (when VPN is on), to the web from that device.
Abstract thinking- open words on a post card compared to a letter enclosed in an envelope.
– Is simply what a VPN service does to your interactions on the frontend device when your internet connection is established through said VPN client. Meant again, what you do on the website from your device is all encrypted to your ISP providers knowledge.
There is a backend here, and I suspose it may be like this. (Alex please chime in)…
Your ISP can see all the IP’s addresses that you land at through the employment of a VPN service. Think point a to b even c, d, e, and f, if you jump from one site to another.
So basically a VPN connection to a visited IP address(es) are all that your ISP provider’s connection can tell them as your IPS provider – from the backend. What you do at a website is all encrypted through the employment of your chosen VPN service and device client.
👍
Ok, see #2. Why a VPN is the best tool…,…,…
https://restoreprivacy.com/unblock-websites/
A VPN (virtual private network) protects your privacy by hiding your actual IP address from the world. When you connect to a VPN server, one of its functions is to strip your actual IP address from the data you send, and replace it with the IP address of the VPN server. This works great for protecting your privacy, hiding your location and ISP-assigned (real) IP address.
This encrypted tunnel prevents any outside observer, including your ISP, from knowing what websites you are visiting. All they can tell is that you are connected to a VPN, not what websites you are visiting through the VPN server.
This leaves the ISP, government, and other third parties no way to know your website access beyond the VPN server.
I’m glad Pixel 7 users get Google One VPN for free. It’s a small step but it matters. Security should be a priority for companies. Every week a business or government and others are getting breached/hacked. Reddit hackers are now threatening to release user data.
We shouldn’t let businesses like financial institutions and other websites deny us access just because they can’t spy on us by tracking our movements and blocking VPN access.
Sven Sir I want to share something.
Sometime back I personally asked Andrey Meshkov, CTO of Adguard, that some in online communities say VPN are not very useful for security and privacy while some say they are useful – according to him how useful are VPN?
He replied – “Pretty useful I’d say, at least it prevents
third parties from knowing what
websites you visit, it prevents websites
from tracking you by IP, etc. All these
points are well known, the only
important prerequisite is that the VPN
you’re using needs to be trusted, not
collecting any info about you.”
I beg you Sven Sir please give your opinion on Point number 6. Is Emsisoft correct or wrong?
https://www.emsisoft.com/en/blog/43213/8-examples-of-bad-security-advice-that-you-can-safely-ignore/
Yes, I completely disagree as I have already noted above. This article also explains why a VPN is an absolute requirement for basic digital privacy when internet service providers are logging everything you do and selling that information to advertisers:
https://restoreprivacy.com/internet-service-providers-isp-privacy-data-collection/
I obviously don’t agree with the Emsisoft article.
Sven Sir please reply,
Emsisift Blog:
https://www.emsisoft.com/en/blog/43213/8-examples-of-bad-security-advice-that-you-can-safely-ignore/
8 examples of bad security advice that you can safely ignore
Point number 6.
6. Use a VPN to improve your security and privacy
Bottom line
Unless you’re trying to access geo-restricted content or torrenting, you probably don’t need a VPN. The reality is that using one would do little to improve either your security or your privacy.
Sven Sir please give you opinion? Please Please Please Please
See sbove “Will a VPN make me 100% anonymous?”
3. Use a VPN to hide your IP address and location, while also encrypting your traffic.
See
https://restoreprivacy.com/unblock-websites/
2. Why a VPN is the best tool for unblocking websites
A VPN (virtual private network) protects your privacy by hiding your actual IP address from the world. When you connect to a VPN server, one of its functions is to strip your actual IP address from the messages you send, and replace it with the IP address of the VPN server. This works great for protecting your privacy, hiding your location and ISP-assigned (real) IP address.
AND later in #2 link I gave,
This encrypted tunnel prevents any outside observer, including your ISP, from knowing what websites you are visiting. All they can tell is that you are connected to a VPN, not what websites you are visiting through the VPN. This leaves the ISP, governments, and other third parties no way to know your website access.
But know the basic threat protection is like #3 that I pointed out above paired with same #1. and #2. below of this information. Against data mining as the tri-basic wedge. These are the three basics that everyone should be doing.
1. Use a secure browser that protects against browser fingerprinting (your browser can reveal lots of information to third parties).
2. Use a good ad blocker. Advertisements are basically tracking in disguise, collecting your activities online, profiling you, and then using that data to target you with better ads. There are also some VPNs with ad blocking.
To answer your questions.
Hey Sven,
Have you ever tried BytzVPN? If so, what did you think?
To get BytzVPN, you have to go to brax.me and create an account with just a username & password. (Real name is optional.) After that, click on the store section to purchase the VPN.
BytzVPN Installation: https://bytzvpn.com/installation.php
Hi,
I would say just use Nord VPN. It is spectacular and I use it all the time. I also have Surfshark VPN as a side VPN which is also nice just in case one needs to connect lots of devices in the family. Why to pay for subpar experience and to compromise? Just use Surfshark or Nord. There are some other smaller but good and trustworthy providers too like Perfect Privacy and OVPN.
Thanks for your input. I’m well aware of Nord & Surfshark. I like to look for things that are great & that no one is talking about. (Diamonds In The Rough)
Can you recommend using VPN all the time? That is, do not turn it off at all, if it does not interfere with me in any way.
@Sven Sir and friends
Reasons we all need a VPN, encryption and privacy.
Here to explain and enumerate I have taken example of India which is at the middle on the spectrum of internet surveillance and censorship – not as restrictive and intrusive as China and North Korea but not quite like western countries which offer a better digital life just as they offer a better life in general.
1. Avoiding Government Censorship which is not restricted to websites harmful websites like Porn and Piracy but also other those websites too which Government deems spreading certain information which it considers harmful or false or propaganda effecting the sovereignty, security and integrity of India or is critical of Indian Government. India despite being a democratic country and claiming free speech has a long history of censorship and bans on books, seminars and web pages or social media posts on various platforms having content which it does not want to reach and spread to the masses. This is done not necessarily for the common good but simply to control and tame the masses and streamline them with the concurrent ideology of the Government in power.
2. Avoiding Government Surveillance as it is a matter of fact that Government of India keeps a constant watch on the flow of internet traffic into the country and out of the country and ISPs are mandated by law to keep logs of user’s internet activity. Government’s keen and close eye on the country’s cyber space is to crack down on threats like terrorism and dissidents. Thus, a VPN is required in India to keep Government from snooping into private affairs and private life of an individual as police and administration in India is very corrupt and judicial system very ineffective to save people from exploitation by Criminals, Mafias and country’s elite.
3. To protect oneself from cyber crimes as India is a global hub of cyber frauds and other abusive and exploitative online activities by malicious actors from India which threaten a user’s digital life both in India as well as abroad.
4. To protect oneself from extensive data collection and data harvesting by private industry and data brokers through online tracking on smartphones and PC’s which is a threat to user privacy, dignity and security. India as of January 2023 does not even have a data and privacy protection law which is not good considering its population of 1.3 Billion out of which 800 million are internet users.
5. To unblock access to internet at work, school and college campus, hostels, overcome IP bans and geo restrictions or simply to get better deals online.
Pressure on open and free internet is increasing day by day as internet is getting increasingly fragmented and compartmentalized due to rising radicalization, formation of eco-chambers and online anti-social or asocial cliques in various online communities as well as ever expanding internet censorship and online surveillance by Governments around the world and also by Private industry including big tech. To combat this trend to safeguard our interest as a progressive and cultured society we need to raise our voices and arms to protect our values and rights by safeguarding and strengthening public and democratic institutions and also by ensuring an open, and safe internet.
Sven Sir a very nice article which describes how VPN and HTTPS both complement each other.
VPNs and HTTPS: A Match Made in Heaven; 5 Reasons You Do Need Both
HTTPS is fantastic for keeping you safe, but it does have a few weaknesses which a VPN can cover.
https://www.makeuseof.com/https-vs-vpn-reasons-you-do-need-both/
A friend of mine is using a pyramid vpn device – see [https://www.pyramidwifi.com/] . How does this work compared to VPN software?
I’ve been reading accounts of where a mother is accused of harassing her OWN DAUGHTER online, but at least two sources I’ve read say that she used a VPN. And yet, the FBI was able to track her using IP addresses. I’d love to hear which VPN she was using. Let’s be clear: I’m not condoning in any way the actions of this “mother of the year” candidate [dripping with sarcasm here], but I AM curious just how they found her. Here’s two accounts of this story:
https://www.gadgetany.com/news/kendra-gail-licari-michigan-mom-who-catfished-daughter-for-a-year-got-arrested/
https://meaww.com/kendra-gail-licari-michigan-mom-42-charged-for-cyberbullying-her-own-daughter-for-a-year
Anyone hear more about this? I’m guessing she must have used a free VPN or one that gladly handed over their logs. All the more reason to read Sven’s reviews of these!
Well, as we have noted before, there are many inferior VPNs on the market that leak data, particularly when you get into the world of free VPNs. It only takes one leaked packet to be exposed, or accessing a site or service just one time without a VPN on.
Hi Sven Sir,
I want to share certain important information with you. It is important for global equality, fraternity and freedom of thought, speech and expression. it is regarding Indian Government’s crackdown on VPN and the subsequent court hearing on a plea filed by an Indian VPN Company (basically a seed box company) against the government regulation on VPN. which claims itself to be the largest democracy and its population of 1.3 billion forms quite a sizable chunk of global human population.
Please also share your views on this matter.
Exclusive: Indian govt in Delhi HC: VPNs “prone to misuse”
https://entrackr.com/2022/12/exclusive-indian-govt-in-delhi-hc-vpns-prone-to-misuse/
Collecting ‘basic information’ such as names does not alter the nature of VPNs: Government to Delhi HC – Anonymity cannot be used as a ground for evading authorities or not complying with the law, the central government said in reply to a legal challenge to CERT-In’s cybersecurity directions.
https://www.moneycontrol.com/news/business/collecting-basic-information-such-as-names-does-not-alter-the-nature-of-vpns-govt-to-delhi-hc-9689831.html
Summary: Indian government staunchly defends its rules for VPN providers in Delhi HC
https://www.medianama.com/2022/12/223-cert-in-counter-affidavit-cybersecurity-directions-vpn/
VPNs Prone To Misuse, Info Sought Under CERT-In Directives Not Sensitive: Centre
https://inc42.com/buzz/vpns-prone-to-misuse-info-sought-under-cert-in-directives-not-sensitive-centre/
============
Some of the readers might not be aware of the background. So I have posted links to relevant articles below.
India’s Anti-VPN Plan a Threat to Privacy, Internet Freedom: Experts
https://www.thequint.com/tech-and-auto/indias-anti-vpn-plan-a-threat-to-internet-freedom-experts#read-more
Indian hosting company sues government over VPN rules
https://entrackr.com/2022/09/indian-hosting-company-sues-government-over-vpn-rules/
India-based VPN to challenge new data law in court
https://www.techradar.com/news/india-based-vpn-to-challenge-new-data-law-in-court
Indian Government Sued Over VPN Logging Orders
https://www.cnet.com/tech/services-and-software/indian-government-sued-over-vpn-logging-orders/
India orders VPN companies to collect and store user data – It seems that India is following the path of Russia and will monitor the online activities of its citizens more closely. Its most recent move will force internet infrastructure providers, including VPN services, to collect and, if requested, hand data over to the country’s governing bodies.
https://nordvpn.com/blog/indian-servers-removal/
Here’s How India Is Cracking Down on VPNs
https://www.howtogeek.com/811010/heres-how-india-is-cracking-down-on-vpns/
This is how new Indian privacy law will have ‘negative impact on people’s privacy
https://www.techradar.com/features/this-is-how-new-indian-privacy-law-will-have-negative-impact-on-peoples-privacy
How India’s Guidelines For VPN Providers Will Kill User Privacy, Restrict Internet Freedom
https://inc42.com/features/how-indias-guidelines-for-vpn-providers-will-kill-user-privacy-restrict-internet-freedom/
Ban on VPNs in India is likely to follow the new VPN rules
https://www.indiatoday.in/technology/talking-points/story/ban-on-vpns-in-india-is-likely-to-follow-the-new-vpn-rules-1947613-2022-05-10
***** Indian Legislators Want The Government To Be Able To Intercept Encrypted Messages
https://www.techdirt.com/2022/09/28/indian-legislators-want-the-government-to-be-able-to-intercept-encrypted-messages/
============
The laws were introduces in April this year, VPN companies were gives time till June to adapt to these laws. It was then that VPN companies like Nord and Surfshark closed their Indian based servers. Deadline was extended till September to implement these laws as three months relaxation was given. Now most other VPN companies closed their Indian servers and companies like Tunnelbear, Norton and McAfee which have their operations and employees in India, for protection of their employees completely shut down their services for Indian users. Others still allow Indian users to connect to VPN servers abroad,
“This is against everything we stand for,” Proton VPN exits India over new data law
https://www.techradar.com/news/this-is-against-everything-we-stand-for-proton-vpn-exits-india-over-new-data-law
We replaced VPN servers in India to keep your data private
https://protonvpn.com/blog/servers-india/
Many common Indians support these laws because they Hero Worship their elected Government and its leader Narendra Modi (Hindu Nationalism) and do not understand the full implications of the actions of their Government and their blind support for it.
Hi Sven,
Can you add information on how to access financial institutions while travelling and using a VPN? In particular, most financial institutions block or lock-out customers should they use a VPN. I’ve had this happen and their “IT Security Department” flagged my bank account when I was using a VPN (locally) and I didn’t disable the VPN.
The bank’s wanted me to basically implode my PC and wipe it completely because they felt I was a victim of malware (which I wasn’t). When I told them I use a VPN, they didn’t care. They told me to take my PC to a computer shop and have the investigate and even if nothing was found, wipe it clean. This is the kind of nonsense some of us who use VPNs have to put up with.
As such, it’s best to take pre-emptive action in the first place and prevent yourself from being locked out should you need to access your bank while travelling.
Hi Dan, I’ve been using various commercial VPNs for 6+ years with four different banks and have never once had an issue, but I have heard others say it can be problematic. You may want to just use a split tunneling VPN, such as ExpressVPN, and then set the split tunneling rules to allow your bank websites to bypass the VPN tunnel, while having everything else encrypted.
Hi Sven,
I’m not sure I follow you on split tunneling. I haven’t found even Express VPN split tunnelling to work. The financial institution(s) detect I’m using a VPN and then I’m blocked.
For instance, I’m in Frankfurt, Germany and my bank is located in Toronto, Canada. I set my VPN location to Toronto, enable split tunneling.
If I understand what you’re saying, when I create a rule to bypass the VPN tunnel, it will raise [another] flag that I’m in Germany, not in Canada. I’m blocked in both circumstances.
The only workaround I have found is to use telephone banking and enable the call via Wi-Fi calling from my registered phone. I have found that even the financial institutions’ app (with biometrics) I’m blocked when outside my “home” city. This one particular financial institution has a “hissy fit” or livid after I clean my cookies and access their site locally.
I’m still waiting to gain access to one bank account, it’s been almost a month.
Oh wow, if you are overseas, then that is a completely different situation and split tunneling will do you no good. In your case, you could try getting a VPN with a dedicated IP address in Canada, then log into your bank from that IP address through your VPN. That should do the trick. When I was overseas, I always used my VPN with a US server for accessing US bank accounts and did not have any major issues, but I know some banks are crazy with the way they lock down their websites.
Like Sven mentioned. There’s only one option aside from doing your banking over the phone. That option is paying extra for a dedicated ip address. Actually, that’s not really an option. It’s a workaround. It’s absurd to pay for a VPN subscription and then pay for a dedicated VPN ip address because VPN ip addresses are flagged or registered as a VPN.
Sven Sir please write a research article on free VPNs like Thunder VPN, Hot VPN etc. I believe they are Chinese honeypots.
Sven Sir, do you know that double VPN is very useful feature. If I am in Iran or similar country where ISP Store user data, then if I make a social media post connected to a VPN, and the repressive Government demands my ip address in hope to get the ip assigned by my ISP to locate me exactly. They will get VPN ip but using ISP records they might know who were the ones connected to that VPN ip address at that time in the country. And they they might use police action.
But with a double VPN feature, they would never find me out as the IP address they obtain and the VPN IP address I am connected to is different.
Thank you Sir
Good point Pea Tea.
Hi guys
It’s been about six years since my first use of a VPN service, so here are my short and honest conclusion of using different VPNs throughout the years.
The first service I bought (annual subscription) was NordVPN. While it worked generally OK at the time, I had a few problems with unblocking some geo-restricted websites, with no help from Nord stuff. That was the primary reason for me not to extend my Nord subscription. Meanwhile, they also had some minor scandals with certain servers, so I’ve decided it’s time to quit Nord and try some other service. When I asked them to delete my account, their response was not so polite and professional, so it was kind of a bitter ending, a bit. But generally, my experience with this service was OK.
Second was Surfshark. A brand new service at the time. Worked good most of the time. Not so great on Windows, much better with mobiles (though killswitch option on iOS is a fake, it doesn’t work; but that might be due to Apple and their restrictions more than to any VPN). BUT: Surfshark is not fully audited service and their privacy policy is not clear and transparent at all. Latest developments of merging with Nord are strange to me, but you can put that in a perspective you like. To me, it’s definitely not a good move for trusting the company and its independence.
ProtonVPN. A good company, with good policy and apps. Average speeds. Probably the best Windows app. But very unstable iOS app. Also, their help service (mailing) is among the worst of all VPNs I tested.
Next is Mullvad. Good speeds and standard settings, but somehow basic apps, with not so many features. All in all, a very solid VPN. Like with Proton, excellent on Windows, not really for iOS. Much better for Android.
Windscribe is a nice VPN, with generous 10 GBs a month for free and a bunch of useful options in settings. Top ad and tracking blocker! But, Canada is their jurisdiction, so it’s not really recommended if that is your privacy concern. Great mobile apps. This is a good service to use from time to time.
IVPN. This is a top notch service from my experience. Everything works just as it should. Absolutely the best VPN for iOS, you can customize it to your like. And unlike Surfshark and most VPN companies that offer multi-hop servers, you can choose among their servers for multi-hop, ie the primary server and the exit node server: just great! Their ad and tracking blocker feature is second best (Windscribe is number one here). A very reliable and trustworthy company. I’m really pleased with this VPN, so it’s definitely my top recommendation.
@Bronco Sir currently which VPN do you use? Personally I use Nord VPN and Surfshark VPN as my main VPN and also subscribed to Atlas VPN. I also get Avast VPN from Avast and Hotspot Shield from Dashlane. And Malloc VPN from Malloc Privacy and Security on Android.
On Windows I get poor experience when installing multiple VPN apps due to conflict because of background services so I only use and have installed Nord on my PC. Surfshark as Firefox Addon on PC. On Android have installed all the apps and use these VPNs with Next DNS except Hotspot Shield as when using this VPN Next DNS does not work
Sven Sir Please reply, I have a big doubt regarding VPNs.
There are numerous online communities which say that VPNs are not useful for online security and privacy. Thought sometimes they do accept that it can be useful for unblocking. They criticise VPN industry and call VPNs useless and a waste of money.
And then they put forth various points involving already existing HTTPS security, TOR, masking IP not useful, no danger if ip is exposed, there are other ways of tracking, VPNs themselves not trustworthy, etc etc.
Below are some of the videos on YouTube with millions of views and people in comment section very happy with the videos and agreeing with the youtuber.
[
All Things Secured 1.4M views 1 year ago
https://youtu.be/8x1BJCKwqpI
Don’t Use a VPN…it’s not the ultimate
security fix you’ve been told
]
[
Wolfgang’s Channel 2.2M views • 2 years ago
https://youtu.be/FMScV1Mkaok
Stop using VPNs for privacy.
]
[
Cyberspatial 983K views 1 year ago
https://youtu.be/9_b8Z2kAFyY
Why VPNs are a WASTE of Your Money
(usually…)
]
[
The Hated One 282K views 2 yr ago
https://youtu.be/gTS17WzsZz8
VPN Providers Are LYING To Your Face!
ft. Techlore
]
Also there are arguments that exist for Antivirus too where people say antivirus are totally useless.
Please help resolve my doubt regarding VPNs. Many of us have these doubts. I am totally confused. Are VPN really necessary for online privacy and security from Governments and Big corporates and Hackers and other malicious actors or they are not useful as widely circulated in many online communities.
Thank you
These are Youtubers who get views from controversial headlines, also known as click bait. They’re trying to give a “hot take” that gets them views. Obviously, I disagree with them, as you can see from my article. Not using a VPN is insanity because it allows internet service providers to collect all of your browsing data and online activity to be sold to advertising networks and handed over to government agencies. It’s that simple.
Yes Sven Sir I agree with you. I read an article where Indian Government is howling to the global community that they need to act together for tougher regulations on and to abolish altogether “encryption”, ” VPNs” and ” Crypto currency”. Also many countries have mandatory data retention laws, for example in my country ISPs have to hoard user data for 180 days. Governments are war mongering, power hungry, manipulative and corrupt. Many of these governments from various countries were involved in targeting activists, journalists and whistleblowers with spywares like Hermit and Pegasus for which they had spent huge sums of money amounting to millions of dollars to acquire these spywares.
VPNs help,
1. a. Unblocking restrictions on local school and office Networks
b. Unblocking government censorship.
2. a. Unblocking access to geo restricted content.
b. Unblocking access to the same product or service in a different region to buy at a cheaper price or to compare prices.
3. a. Hiding browsing activity and online activity on local school and office networks from network administrator.
b. Hiding browsing activity and online activity from ISP.
4. a. Hiding from server side tracking by complementing HTTPS and hiding ip address and geolocation of the user.
b. Hiding from 3rd party trackers on websites by masking user ip address and also preventing the website from tracking user by IP address and geolocation etc.
5. a. Securing from man in the middle attack on public WiFi.
b. Securing from Hackers to some degree by hiding from malicious players on the other end by mixing user activity with other users and this help lower user profile
Thus VPNs serve these 10 purposes and help secure user from the dark side of the internet while also helping to take greater advantage of the existing bright side.
VPNs are thus very very useful tools which serve essential and unique purposes and along with other security tools and secure practices help secure user online.
Only pre-requisite is that VPN should not be logging and collecting user’s online activity.
@Truebluerover
Discussed here. And I do think this should be reviewed.
https://worldofmatthew.com/technology/mullvad-m247/
I was reading recently how the technology streaming companies like Netflix use to identify, mitigate, and stop access to anyone using a VPN may become mainstream sooner than later. More governments are imposing rules that VPN providers must keep [identifiable] logs.
My take-away is that eventually VPNs will be used only for a link or gateway to your work (company’s) portal. Otherwise, if you use a VPN to access (most) if not all websites, it will be blocked.
Hi.
I’ve noticed that many, if not most, VPN companies use M247 for their connection & DNS resolving.
As far as I am aware, this company is UK based and the thought of this company being responsible for what appears to be the lions share of VPN connections surely cannot be a good thing.
Any thoughts?
Yes, it’s a large hosting provider, and consequently, it has data centers where VPNs rent serves. If the VPN is properly encrypting and securing all of the servers in its network, then there are no concerns that I see. But that’s not always the case – see the Windscribe security incident.
Hi Sven,
A very comprehensive and thorough guide!
Very well backed up by the extensive RP work linked to.
The best guide on the web.
BoBeX
Thank you, BoBeX!
@ThatGuy
I spend too many hours reading RP guides – lol.
The RP guide guide about securing an Android devise provides good advise for choosing apps and extensions.
(Each person needs to research there own apps)
I don’t know how the apps you use work.
I would guess the are blocking lists using DNS.
(DNS is the phone directory of the internet)
You can find tools to do this, they are often described as “parental control tools”
(I guess this term reflects is the most common use case, though I note this isn’t your case)
OpenDNS is one example of this which I previously used.
I recall Sven has commented on these services.
OpenDNS was not in his recommended list,
But in chat I asked and he did not criticize OpenDNS either.
(I can’t remember where that was discussed)
What you are asking is simple to do.
Trial OpenDNS if you are interested.
If you like the idea you could look further into RP privacy guides.
Where this gets a bit more tricky is combining a DNS provider with a VPN provider.
Sure it would work and is not hard to do.
The RP privacy recommendation is to use the VPN’s built in DNS service.
Possibly good questions for Sven…
Your advise is to use the DNS service provided by the VPN.
a) do you know of a VPN that provides customization and controls of DNS filtering?
b) if not, what is you view on using a VPN service and also using a separate DNS service where DNS is recommended as private and secure?
To your questions:
1) Yes, there are a few VPNs with ad blockers that utilize DNS filtering. With Perfect Privacy, you have the ability to enable different filtering lists. With some of the others, it is a simple ‘On’ or ‘Off” without customization.
2) Using a separate DNS service on the same device you are using a VPN can potentially cause some issues — namely DNS leaks. I’d recommend sticking to a good VPN, and if you want the ad blocking feature via DNS, that can be enabled with the VPN.
Hi Steve,
I hope that you can help me. I was reading one of your VPN reviews and came across on that seemed interesting. It offered a solution for situations where websites block VPN traffic. This VPN service would camouflage it’s VPN traffic making it appear like routine HTTPS traffic.
But I now can’t find that review or the name of the VPN. Can you help? Thanks!
You are probably thinking of Surfshark VPN with the Camouflage mode.
Hi, been reading your site for a couple of months and have made some major changes to my security practices since – and have slowly but surely getting my fiancee to understand the importance of this as well. You guys are awesome!!!
Had a question about VPNs – since your own IP is now getting masked, it seems to me that when you log into websites that allow you to hit “Remember me”, they’re seeing the VPN server’s IP. If someone else now goes to the same website, wouldn’t the website mistake the two distinct people as having the same IP? Is this not a security risk now if I clicked “remember me” to log in to a website?? Sorry if this is a dumb question, I’m new to this!
No, when you click “Remember me” as you describe on websites, the site is dropping a cookie in your browser to remember you. It’s not based on IP address at all.
What about Adguard VPN? 🙂